Security incidents are not uncommon in traditional finance, and they are even more common in the anonymous currency circle, which is like a dark forest.
Data shows that in the past May alone, 37 typical security incidents occurred in the crypto circle, and the total loss caused by hacker attacks, phishing scams and rug pulls reached 154 million US dollars, an increase of about 52.5% from April.
On June 3, two security incidents occurred again. Slightly different from other incidents, both incidents were related to large exchanges, and the process was also quite bizarre. However, at the end of the story, some people were happy and some were worried.
On June 3, a user named Nakamao posted a long article on the X platform and it went viral. In the article, he mentioned that "he became a victim of the currency circle, and 1 million US dollars in his Binance account disappeared." In the self-narration, a series of hacker thefts kicked off.
It is said that on May 24, Nakamao was still on his way to work, and all his communication devices were not left. However, in this seemingly foolproof background, the hacker used the knock-on transaction to steal all the funds in his account without obtaining the Binance account password and the two-factor authentication instruction (2FA).
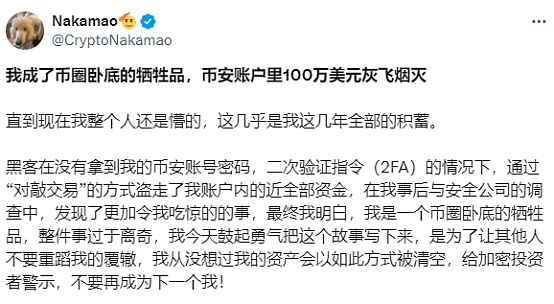
In short, knock-on transactions are large-scale transactions in trading pairs with scarce liquidity, and the trading party buys in large quantities to take over the selling of the hacker account. In the end, the other party obtains actual funds or stablecoins in a certain altcoin, and the buyer takes over the altcoins in the hands of the seller. This type of theft is not uncommon in exchanges. In 2022, FTX had a theft of up to 6 million US dollars due to the leakage of 3commas API KEY. At that time, SBF used its cash ability to redeem and settle the matter. After that, Binance also had large-scale counter-trading transactions. But the viciousness of this model is that for exchanges with poor risk control, it is just a very common trading behavior, and there is no abnormal theft.
In this case, QTUM/BTC, DASH/BTC, PYR/BTC, ENA/USDC and NEO/USDC were selected, and the user's large amount of funds was used to buy up more than 20%. The user did not discover all the hacker's operations until he checked the account information more than an hour later and found the abnormality.
According to the response of the security company, the hacker manipulated the user account by holding the web cookies hostage. In simple terms, it used the terminal data saved on the web page. To give a typical example, when we enter a certain interface on the Internet, we do not need to log in with an account password, because historical access and default records have been left before.
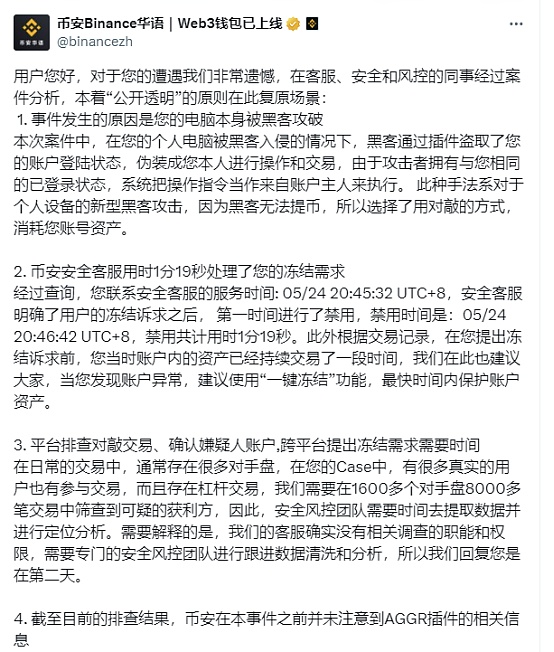
At this point, it may be just the user's own negligence, but the follow-up has become even more bizarre. After the theft, Nakamao immediately contacted the customer and Binance co-founder He Yi, and handed over the UID to the security team, hoping to freeze the hacker's funds in a short time. But it took Binance staff a day to notify Kucoin and Gate. There was no surprise that the hacker's funds had already disappeared, and the hacker only used one account, without diversifying the accounts, and took all the funds from Binance safely. During the whole process, the user not only did not receive any security reminders, but more ironically, due to the purchase of large transactions, Binance actually sent him an invitation email to become a spot market maker the next day.
In the subsequent review, an ordinary Chrome plug-in Aggr entered Nakamao's field of vision again. The plug-in is used to view market data on the website. According to the victim's description, he saw that multiple overseas KOLs had been promoting it for months, so he downloaded it for his own needs.
Here is a simple popular science. The plug-in can actually perform multiple operations. In theory, it can not only log in to the trading account through malicious extensions, access the user's account information for trading, but also withdraw funds and modify account settings. The core reason is that the plug-in itself has a wide range of permissions to access, operate network requests, access browser storage, operate the clipboard and other functions.
After discovering that there was a problem with the plug-in, Nakamao immediately found the KOL to inquire and warned the KOL to notify users to disable this plug-in, but unexpectedly, the boomerang was inserted into Binance at this moment. According to Nakamao's initial statement, Binance had already known about the problem with the plug-in. A similar case occurred in March this year, and Binance tracked down the hacker. Perhaps to avoid alerting the enemy, it did not notify the suspension of the product in time, and let the KOL continue to keep in touch with the hacker. At this stage, Nakamao became the next victim.
Only using Cookies to log in and trade, there must be some problems with the Binance mechanism, but the incident itself was actually caused by the user's own negligence, and accountability became a problem.
Sure enough, Binance's response to this afterwards caused an uproar in the market. In addition to the official account's review that the cause was a hacker attack, and Binance did not notice the relevant information about the AGGR plug-in, He Yi also commented on the incident in a WeChat group, "This is a matter where the user's computer was hacked, and even the gods can't help, and Binance has no way to compensate the user's own device for being hacked."
Nakamao obviously cannot accept Binance's operation, believing that Binance has no risk control and that KOL has clearly confirmed that he mentioned the plug-in to the Binance team, and Binance is also suspected of not reporting it. As public opinion continues to ferment, Binance also responded again that it will apply for a reward as feedback for users reporting malicious plug-ins.
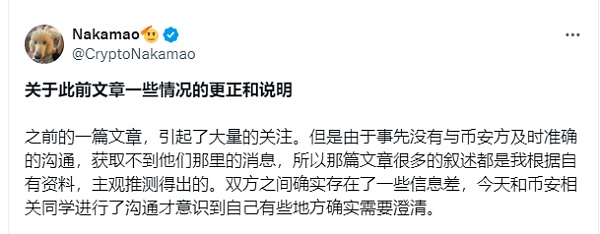
I thought the matter had come to an end, but interestingly, on June 5, the incident reversed again. Nakamao once again apologized to Binance on the X platform, saying that there was a gap in information with Binance and that he had subjective assumptions. Binance was not actually aware of the plug-in. Binance first learned about the aggr.trade website on May 12, not in March as mentioned earlier. In addition, the KOL was not an undercover agent of Binance. The communication between the KOL and Binance was about the account issue, not the plug-in issue.
Whether this statement is true or false, the 180-degree turn in attitude, from disappointment to public apology, can also be seen that Binance must have compensated him, but the specific amount of compensation is unknown. <span yes'; font-size:10.5000pt;mso-font-kerning:1.0000pt;">
On the other hand, coincidentally, on June 3, in addition to Binance, OKX was also affected. An OKX user said in the community that his account was stolen by AI face-changing and 2 million US dollars in the account was transferred away. The incident occurred in early May. According to the user's description, the reason for the theft of his account had nothing to do with personal leakage, but the hacker logged in to the email account and clicked "Forgot password", and simultaneously built a fake ID card and AI face-changing video, bypassing the firewall, and further changed the mobile phone number, email and Google's authenticator, and then stole all the assets in the account within 24 hours.
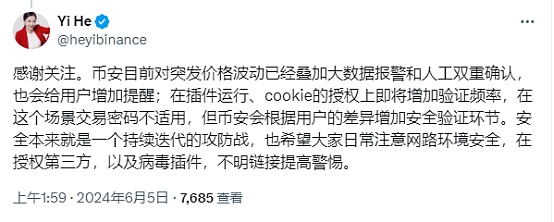
He Yi also responded to this, saying that "at present, big data alarms and manual double confirmation have been superimposed on sudden price fluctuations, and reminders will also be added to users; the verification frequency will be increased in plug-in operation and cookie authorization. The transaction password is not applicable in this scenario, but Binance will increase security verification links based on user differences."
Back to the starting point, judging from the two incidents, users also need to pay great attention and enhance their own security awareness. On the premise of dispersing assets, try to use completely independent devices for operation. It is recommended to use decentralized authentication, not convenience as the core, avoid setting up password-free and liveness authentication, use plug-ins with caution, and use hardware wallets for storage of large assets.
After all, crypto assets are different from physical assets. Physical assets can at least be tracked, while the theft of crypto assets is almost difficult to obtain subsequent compensation due to regulatory restrictions, and even filing a case is quite difficult.
Such cases are not uncommon. A typical example appeared in the recent report of 1818 Golden Eye. The victim, Mr. Zhu, found a big man "Cheng Qiqi" on Zhihu who claimed to have earned tens of millions of yuan by speculating in cryptocurrencies, and hoped to follow him to speculate in cryptocurrencies to make money. After negotiation, the two parties signed a contract to achieve profit-sharing cooperation, clearly stating that 70% of the profits belonged to Cheng Qiqi, and 30% was retained by Mr. Zhu. If there was a loss, the two would each bear 50%. During the transaction, Mr. Zhu only followed the order and the ownership of all accounts was in his own hands.
Such a high profit-sharing contract that seemed to have a degree of trust did not bring trustworthy results. After the initial small profit, the victim increased his investment and used the borrowed principal of 600,000 yuan and leverage of 100 times to short ETH under the slogan of "full compensation for liquidation" guaranteed by Cheng Qiqi. In the end, due to the rise of ETH, the victim lost all his money.
This situation is obviously difficult to file a case because all operations are done by individuals and there is no fraud or coercive behavior. At the end of the matter, the police and reporters could only helplessly emphasize that according to my country's laws and regulations, virtual currency transactions are not protected, there are high risks, and vigilance should be increased.
In the end, Mr. Zhu, with a heartbroken and innocent expression, staged a ridiculous ending.
Anyway, I would like to remind the spectators who are participating in the transaction again that in any financial field, even in the crypto circle, which sacrifices some security to obtain high profits and freedom, security is far more important than efficiency or profitability. This may be one of the reasons why the so-called decentralized crypto world is difficult to leave centralization.
After all, human nature is like this. Everyone wants someone to cover the bottom, and no matter how much money they make, they don’t want to make wedding clothes for others.
 Wilfred
Wilfred
 Wilfred
Wilfred JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance cryptopotato
cryptopotato Bitcoinist
Bitcoinist