Source: Shenzhen Lingshi Technology
Background
On February 25, 2024, we monitored an attack on Ethereum : https://etherscan.io/tx/0xf0464b01d962f714eee9d4392b2494524d0e10ce3eb3723873afd1346b8b06e4, targeting BlueBerryProtocol, with a loss of approximately 455 ETH 1.4M USD. Fortunately, the attack was intercepted by a white hat with the ID c0ffeebabe (0xC0ffeEBABE5D496B2DDE509f9fa189C25cF29671[c0ffeebabe.eth]), and 366.5 ETH 1.2 M USD was finally returned.
BlueBerryProtocol is a DeFi project based on Compound fork, providing lending, mortgage and other services. The specific operating mode is as follows:
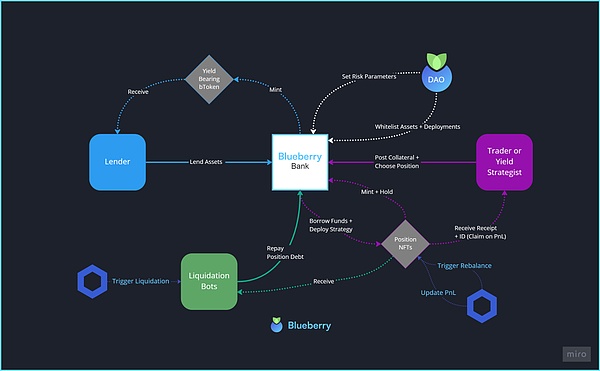
Attack Analysis
The attacker first borrowed 1 WETH from Balancer through a flash loan.
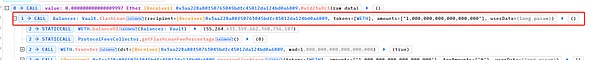
Subsequently, the attacker mortgaged 1 WETH to BlueBerryProtocol in, and mint 1 bWETH. Then, the attacker used 1 bWETH as collateral to borrow 8,616 OHM (Decimal=9), 913,262 USDC (Decimal=6), and 6.86 WBTC (Decimal=8).
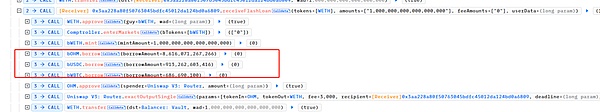
Finally, the attacker will obtain the OHM, USDC and WBTC are exchanged for 457 ETH.
Vulnerability Analysis
The root cause of the problem is that the code handles the mantissa incorrectly when processing different assets. The decimal of WETH is 18, the decimal of OHM is 9, the decimal of USDC is 6, and the decimal of WBTC is 8.
However, the price oracle of BlueberryProtocol scales according to decimal=18 when processing the token price.
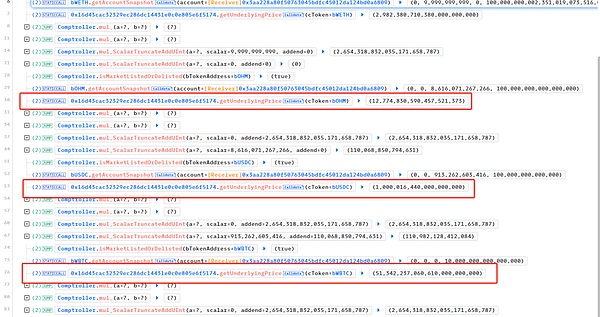
As a result, the value of OHM has shrunk by 1e9, and the value of USDC has shrunk by 1e12 , the value of WBTC shrank by 1e10. As a result, the attacker took away assets worth 460 ETH with only 1 ETH as collateral.
Summary
This vulnerability is caused by the project using the same code to process different tokens and failing to take into account the different decimals of different tokens. As a result, assets with smaller decimal sizes shrank significantly and were borrowed as collateral by attackers at a very low cost. It is recommended that project parties conduct sufficient audits and cross-audits on smart contracts before the contracts go online to avoid such security issues.
 JinseFinance
JinseFinance









