L2 MEV core role: Sequencer
L2 Sequencer, as the Ethereum Layer 2 is the core component of the program and plays a key role. Its main task is to process transactions, that is, package and submit them to the ETH main chain or off-chain network, to improve the throughput and efficiency of the entire blockchain ecosystem. Specifically, Sequencer plays a similar role to the transaction pool on the Ethereum main chain, but its working method and scope are more specialized. In addition, L2 Sequencer also provides more operational freedom for applications and smart contracts, allowing more complex logic and contracts to be implemented at the L2 level without worrying about high gas fees.
Sequencer transaction processing process
Collect
Sequencer receives transaction requests from users, these requests are usually in the format of Ethereum transactions, but they are sent to the Layer 2 network instead of the main chain.
Verification
Sequencer verifies the transaction to ensure that the sender has sufficient funds to execute the transaction and complies with the Layer 2 network the rule of. It also ensures the validity of transactions to prevent fraud and double spending.
Sorting
Sequencer sorts transactions according to certain rules to ensure that they are executed in the correct order to prevent potential transaction conflicts.
Commit
Once transactions are verified and sequenced, the Sequencer submits them to the Layer 2 network so that they can be executed. This typically involves interacting with Layer 2 smart contracts, updating state, and ensuring that the ledger on Layer 2 is in sync with the ledger on the ETH main chain.
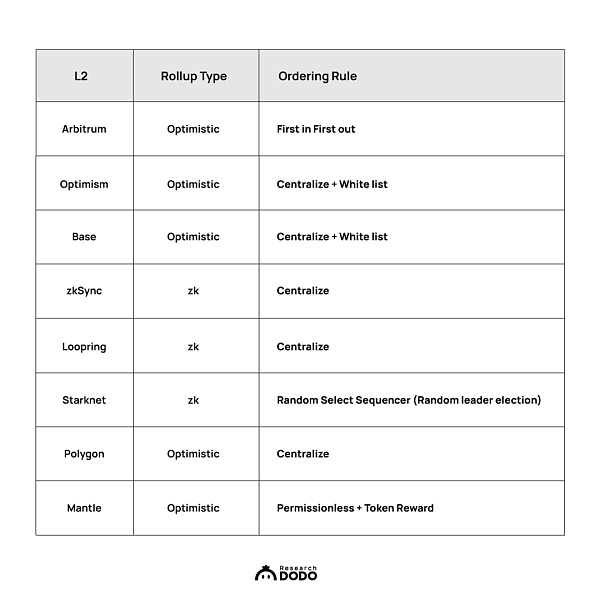
Collation rules of different L2 Sequencers
< p style="text-align: left;">
Arbitrum's sorting rulesIn order to avoid MEV problems as much as possible, Arbitrum does not make it public memory pool and adopts a first-come-first-served (FCFS) sorting mode so that transactions submitted first can be processed earlier.
Optimism’s sorting mechanism
Optimism introduces auctions An ordering mechanism, the MEV Auction (MEVA), to fairly distribute the advantages and disadvantages of transaction processing. Additionally, Optimism launched the Bedrock Sequencer after the Bedrock upgrade, used for sequencing in conjunction with MEVA. Similar to Arbitrum, the Bedrock sequencer has its own private memory pool. MEVA has not been fully implemented yet, but according to the current plan, MEVA winners will have the right to reorder submitted transactions and insert their own transactions, but cannot delay a specific transaction for more than N blocks, which also means that the MEVA winner's MEV profits are subject to limit.
Collation of other L2 solutions
Except Arbitrum and Optimism, there are many other L2 solutions such as zkSync, Loopring, Starknet, etc., each of which adopts different ordering rules to meet the needs of different users and applications.
 < br>
< br>
MEV extraction in L2
In the blockchain world, the generation of MEV (Miner Extractable Value) is the result of a variety of factors. The root cause is the inevitable delay between the transaction information submitted by users being propagated in the network and the actual blocks being mined. This time difference gives nodes room to operate. Due to the nature of a decentralized system, different nodes may receive transactions in different orders and at different times, which means that the system cannot guarantee that the status of all nodes at the same time is consistent. This inconsistency creates the conditions for MEV to arise.
On the Ethereum mainnet, the extraction of MEV has generated large-scale profits. MEV attackers typically monitor transactions in the Mempool and ensure that their transactions are prioritized by participating in so-called Gas Auctions (bidding transaction fees to prioritize transactions) or by paying bribes over the counter. In this way, they are able to obtain benefits through a predetermined sequence of transactions.
The process of earning MEV profits can be broken down into two key steps. First, an attacker would need to identify potentially profitable transactions and construct a block of transactions specifically optimized for the purpose of extracting MEV. Secondly, it is necessary to ensure as much as possible that these specially constructed transactions can be accepted by the network and included in the blockchain.
However, with the rise of Layer 2 (L2) solutions, MEV extraction methods and strategies have changed significantly. Since the sequencers of L2 solutions are often centralized, MEV extraction faces new challenges and opportunities compared with traditional Layer 1 (L1).
For those L2 solutions without a mempool, monitoring transactions becomes more difficult. In this case, the sequencer has more power because it directly determines the order in which transactions are processed. The absence of a mempool means that an attacker cannot adjust the order of transactions by monitoring the transaction pool as in an L1 solution, which greatly increases the difficulty of conducting MEV attacks.
In L2 solutions with memory pools under the control of a centralized sorter, the impact of Gas Auction on sorting is also reduced. Some L2s even have no Gas Auction at all, which is a game changer. Although attackers cannot determine the exact order of transactions, they can still try to influence the placement of their own transactions by adjusting the Gas Fee. This strategy is much less successful and less predictable than L1.
In addition, some independent DAPPs on L2 may maintain their own local transaction memory pool. These memory pools have become potential monitoring targets for attackers, who may exploit these DAPP-specific memory pools to implement MEV extraction.
For those L2 chains that run Gas Auction, such as Polygon, the addition of validators is not completely open and thresholdless (permissonless). In this case, when attackers detect MEV opportunities, they may adopt a strategy of submitting a large number of transactions to increase the possibility of their own transactions being included on the chain. This strategy relies on luck and low transaction costs and is a less deterministic attack method.
Finally, an attacker may also exploit the interaction between L1 and L2 or between different L2 solutions to extract MEV. This requires attackers to have a deep understanding and analysis of cross-chain status and dynamics.
Differences in MEV extraction space between different L2s
< strong>MEV extraction space varies significantly between different L2 solutions. These differences are mainly determined by factors such as L2's sorter rules, mempool design, transaction volume, and transaction size. Tin general, the more centralized an L2 solution's sequencer is, the more concentrated the MEV extraction space will be, and therefore the extraction opportunities will be relatively smaller. The more open the memory pool design is, the more space is provided to attackers, and they have more opportunities for transaction monitoring and sequential operations.
At the same time, the transaction volume and transaction size of the L2 solution also have an important impact on the MEV extraction space. L2 with large transaction volume and transaction size provides more opportunities to extract MEV, because in a high-traffic environment, there are more profitable transactions and attackers have more opportunities to extract profits. On the contrary, for L2 with small transaction volume and small transaction size, the space for MEV extraction is relatively small because the opportunities themselves are few.
L2 MEV Future Solution
Blockchain Technology One of the essential issues is how to achieve true decentralization. In L2, the core of this problem is the implementation of the decentralized sequencer, which is related to how the order decision rights of transactions are distributed. This directly affects the fairness, security and other key performance of the blockchain system. The MEV problem of L2 is actually a derivative problem of transaction ordering weight. Currently, most L2 are centralized sorters, and MEV extraction is opaque. There are two potential solutions. One is to decentralize the sorter through a specific mechanism, and the other is to outsource the sorting power to the third party. Third party, a third party constructs the sorting scheme.
Decentralized sorter
< li>Blockspace Auction achieves the allocation of sorting rights through bidding. In this mechanism, participants publicly bid for block space for a specific period of time and then have the right to sort the block space. The advantage of this approach is that it is transparent and competitive, which can encourage participants to offer more reasonable prices. However, the disadvantage is that it may create a "winner's curse", where the winner actually suffers a loss due to excessive bidding.
Random leader election (Random leader election), which passes Leaders are randomly selected from a pool of participants that meet certain conditions to sort. For example, select from those users who have pledged 32 ETH, such as Starknet’s random drawing method. The advantage of this method is its randomness, which can reduce potential unfair competition, but the disadvantage is that the abilities and contributions of participants may be ignored, and the lack of competition may lead to a decrease in efficiency.
"Proof-of-Work" , by having many potential sequencers compete for the construction of a certain block, the sequencer wins by being the most efficient or fastest competitor. The advantage of this approach is that it encourages technological innovation and efficient operation, but the disadvantage is that it may lead to a large waste of resources.
Economic competition (Economic competitionion)ion strong>It is a method in which different participants compete to achieve the best economic results. For example, the block inclusion order is determined based on the block fee. This method is more flexible and has a lot of room for design, such as MEV redistribution, MEV auction, etc., and encourages everyone to build blocks through an open economic mechanism. This approach encourages market dynamism, but it is also possible for a few entities to monopolize the right to sort through competitive advantage.
Fair Sequencing is a specific algorithm The way of directly sorting transactions is essentially a language and a network. Chainlink has now implemented this solution. The advantage of fair sorting is that it limits the space for extracting MEV value from the bottom by adjusting the transaction sequence. However, the disadvantage is that the performance of DAPP under fair sorting will become worse, and the applicability of fair sorting rules is not high. .
The implementation of a decentralized sorter may not only promote fairness and transparency, but also improve the overall System security. However, it also brings a series of challenges, such as resource waste and market barriers. From a future perspective, each L2 will develop in the direction of decentralized sorters, but for now, for efficiency and cost considerations, most L2s should maintain centralized sorters.
Outsource sorting rights to a third party
Shared sorters, such as Espresso and Astria. They focus on providing sorting services and organize sorting in a specific way. The chain connected to their service does not need to consider the issue of sorting itself. The benefit of this approach is that it can standardize and specialize the work of the sequencer, but it may also introduce external dependencies, thus affecting the degree of decentralization.
From a personal point of view, the solution of sharing the sorter is actually a modular idea, but we should also think about it. For a public chain, for a zone Block building and transaction ordering Establishing viable decentralized solutions and mechanisms is itself part of building a public chain. As modularity takes off, shared sequencers are likely to become more widely used.
By organizing cross-chain MEV auctions, ordering services are provided in disguise, such as SUAVE. SUAVE is actually a chain, and the solution using SUAVE is actually to outsource the block construction and memory pool services to SUAVE.
SUAVE's features include: SUAVE itself does not capture MEVs (except for gas fees); searchers (expressing their preferences on SUAVE) accept them by asking executors to transaction package (including cross-chain MEV) to extract MEV; the executor can also capture a portion of the searcher's MEV (paying as much back to the searcher as possible). The advantage of this approach is that it can optimize resource allocation through the open market, but the disadvantage is that it may increase system complexity and may reduce the level of decentralization to a certain extent.
Outsource block construction to L1, i.e. Based Rollup (e.g. Taiko).
L1 has built a sufficiently decentralized system to provide decentralized sorting services. Based Rollup's MEV extraction method is as follows: MEV naturally flows to Ethereum, which strengthens the economic security of L1; L2 searchers (create L2 transaction packages) and L2 builders (can run mev-boost) can also be divided into part MEV; cross-chain MEV value can also be captured if an L2 searcher monitors the Ethereum memory pool, the Rollup-based memory pool, and the status of both chains. This solution has strong feasibility, but the disadvantage is that the upper limit will not exceed the current solution. Ethereum has a large MEV extraction space under the current architecture. If the sorting power is given to L1, this will not improve the MEV ecology.
Outsourcing the block proposal work to a third party can lead to resource optimization and the advantages of diversifying risks, but it also poses a potential threat to decentralization.

L2 MEV Data
The dune panel created by Dragonfly's data analyst @hildobby shows part of the MEV of L2 data.
Polygon
Sandwich attacks on Polygon are relatively rare , less than 1% most of the time. In September of this year, it peaked at around 2.3%. Based on the transaction volume, the transaction volume affected by the sandwich attack is very low.
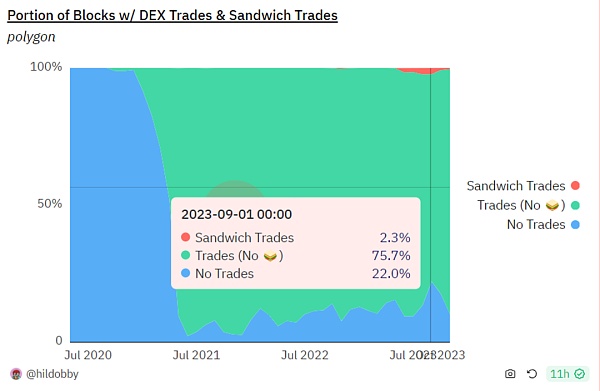
Sandwich transaction ratio

Sandwich trading volume
The proportion of arbitrage transactions on the Polygon network is higher, and the transaction volume is significantly larger than the sandwich attack.
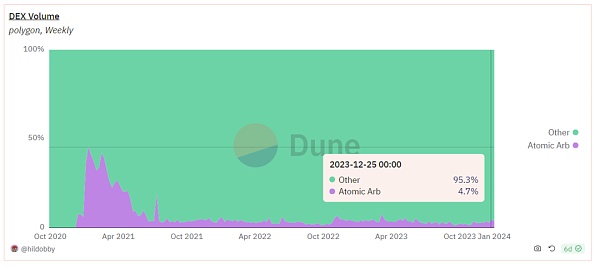
Arbitrage ratio

Arbitrage volume
Arbitrum
Sandwich attack on Arbitrum block transactions since 2023 ratio has dropped to a sufficiently low level. In terms of transaction volume, the total transaction volume is in the billions of dollars, while the transaction volume involved in the sandwich attack is only a few hundred thousand dollars, which is also very small. This may be related to the transaction ordering rules of Arbitrum FIFO.
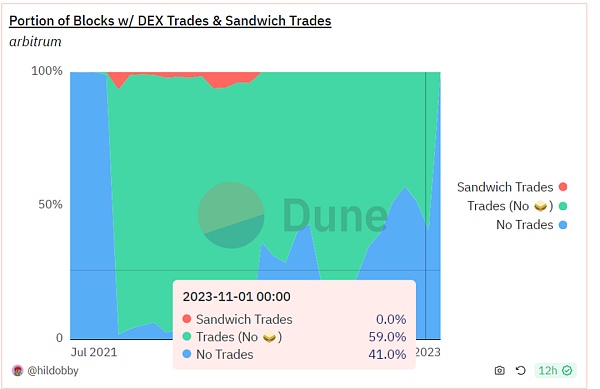
Sandwich transaction ratio

Sandwich transaction ratio
The proportion of arbitrage trading on Arbitrum is relatively small compared to other chains. However, the volume of arbitrage trading is still much higher compared to sandwich trading on Arbitrum.
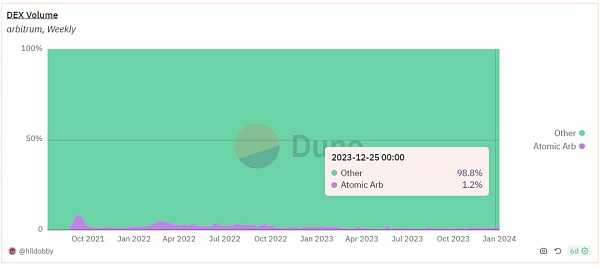
Arbitrage ratio

Arbitrage volume
Optimism
On Optimism, things are different. The proportion of sandwich attacks in block transactions was once as high as 62.7%, but has gradually decreased over time because the bedrock upgrade introduced a gas mechanism similar to EIP-1559. Recently, the proportion of sandwich attacks has dropped to sufficiently low levels. In terms of transaction volume, the size of sandwich attacks has been reduced to a few thousand dollars.

Sandwich transaction ratio

Sandwich trading volume
On Optimism, the proportion of arbitrage trades ranges between 2% and 4%, showing a downward trend compared to last year. The trading volume of arbitrage trades is relatively low.
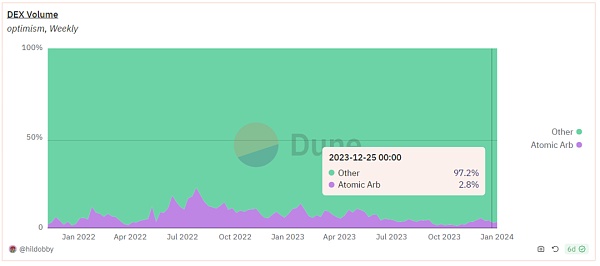
Arbitrage ratio

Arbitrage trading ratio

< strong>Summary
In general, the relationship between L2 Sequencer and MEV is of great significance to the development of the ETH ecosystem. Currently, the challenge faced by L2 is to ensure a fair and transparent sorting mechanism to prevent the extraction of MEV. However, the complexity and diversity of L2 solutions have brought many challenges, including how to resist MEV, ensure a fair and transparent sorting mechanism, etc. . At the current stage, there are already some feasible solutions, such as Shared Sequencer, and cryptographic methods to protect the privacy of transaction sequencing.
In the future, practical solutions may focus more on the decentralization of Sequencer to reduce potential MEV extraction space. At the same time, you can also consider outsourcing block generation to a third party to improve the fairness and efficiency of the entire network system. On the other hand, the emergence of cross-chain MEV requires us to re-examine the definition and importance of MEV, and explore new solutions such as Slot Auctions and Interchain Scheduler. In addition, future research questions include how to quantify MEV on the L2 chain, the impact of PGA on L2, etc. Solving these issues will help further improve MEV resistance strategies in the L2 field.
References
https://taiko.mirror .xyz/VjNjFws6OOVez5YCDMwjy4BUiDqZBHYDvcW4-JZGDkc
https://timroughgarden.github.io/fob21/reports/r11.pdf
https://explore.marlin.org/#/
https://arxiv.org/pdf/2112.01472.pdf< /p>
https://www.panewslab.com/en/articledetails/2nlmo28j.html
https://ethresear.ch/t/mev-for-based-rollup/15636
https://public.bnbstatic.com/static/files/ research/ethereums-rollups-are-centralized-a-look-into-decentralized-sequencers.pdf
Dune Dashboard:
https://dune.com/hildobby/sandwiches?Blockchain=optimism
https://dune.com/hildobby/ atomic-mev
 JinseFinance
JinseFinance

 < br>
< br>












