Source: Beosin
On January 17, 2024, according to Beosin’s EagleEye security risk monitoring, early warning and blocking platform monitoring, theSocket protocol suffered a call injection attack by an attacker, resulting in a large number of Authorized user funds were stolen. Currently, the attacker converts the stolen funds into ETH and saves them on the attacker's address.
After the attack, Socket officially confirmed that it had been attacked and immediately suspended the affected contracts.

At the same time, MetaMask issued a document on the X platform saying, MetaMask Bridge users are not affected by the Socket vulnerability that occurred today. MetaMask said that it adopted a unique architecture when designing the cross-chain bridge contract to prevent such attacks.
Regarding this attack, the Beosin security team Analyzed.
Vulnerability Analysis
The main reason for this incident is that the Socket contract's performAction function does not exist. Safe call calling. As shown in the figure below, the basic function of this function is to convert the user's ETH and WETH. If the caller selects fromToken as ETH, then the toToken (WETH) balance of the contract will be queried, and then toToken is called through call (normal logic Next, the deposit function of WETH must be called here) and the amount of ETH specified by the user is transferred. Next, the new balance of toToken (WETH) of the contract is queried. If it is equal to the amount of ETH transferred by the user, then it is passed and the toToken is transferred. Specify the address of the caller. If the caller chooses fromToken other than ETH, then in the same way as above, the function function is to convert the caller's WETH into ETH (under normal circumstances, the call must call the withdraw function of WETH) and send it to the user's specified address.
Although there are no checking restrictions on fromToken and toToken in the function, except for the WETH address passed in, other ERC20 addresses will cause the balance check to fail, making it impossible to forge these two parameters and indirectly change the token address. Limit to WETH.
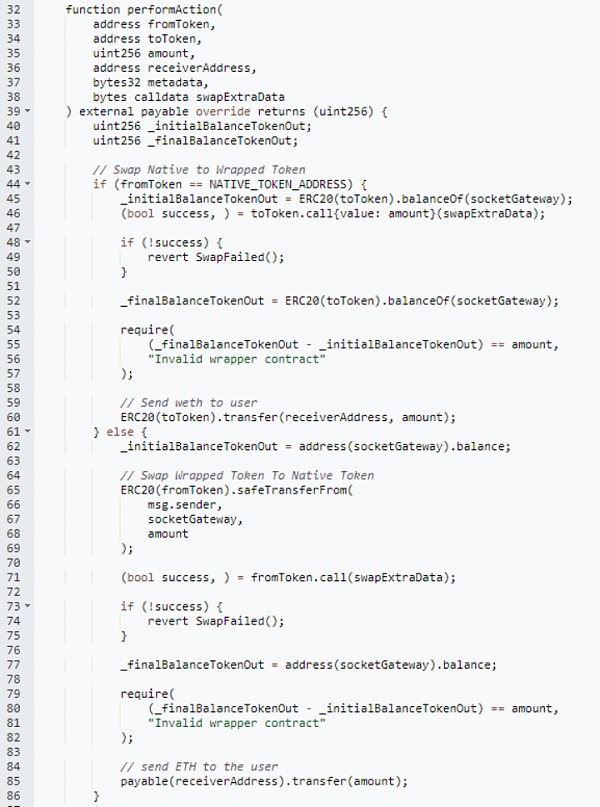
Although there are restrictions on token addresses, this function also has a The problem is that there is no limit on the amount. If the amount passed in by the caller is 0, the function's check condition will always pass, and there is no need to call WETH's deposit and withdraw functions. At this time, abnormal data can be injected into the call to achieve the purpose of attack.
Attack Process
Now that we understand the problem with the function, let’s take a look at how the attacker carries out the attack.
1. The attacker first creates an attack contract.

2. Subsequently, the attacker queried the WETH balance of different addresses multiple times, and Query the authorized number of the address for the Socket: Gateway contract, and finally call the Socket: Gateway contract.
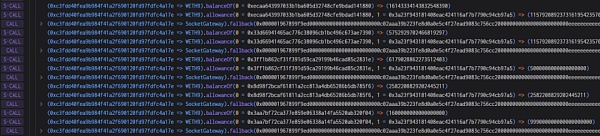
3. As you can see, when the performAction function is called here, swapExtraData The parameter passed in is 0x23b872dd..., which is the function signature of transferfrom, indicating that the transferfrom function of token will be called directly here.

4. It can be seen that the attacker passes in fromToken as WETH and the amount is correct. It is the 0 we mentioned above. The contract transferred the attacker's WETH into the contract, but it was 0. In the call call, the attacker specified a user address and transferred 16 WETH to the attacker.
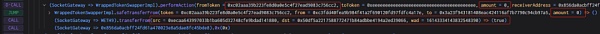
5. The attacker transfers the WETH of countless users to himself through a large number of operations .
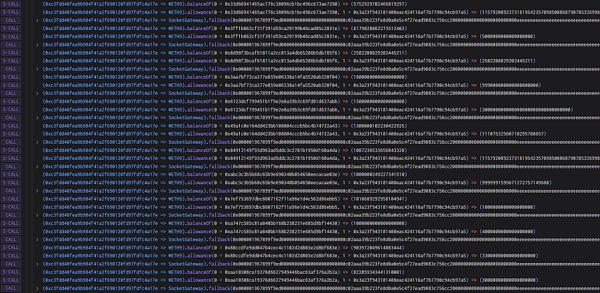
6. The attacker uses the same method to authorize the contract Transfer the USDT to yourself.
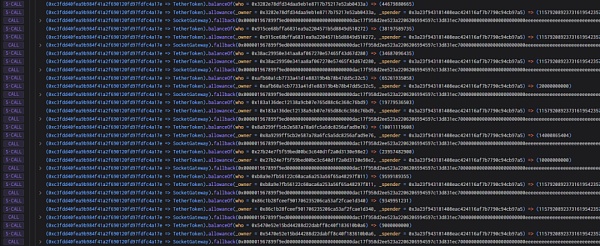
7. It also includes three tokens: WBTC, DAI and MATIC.
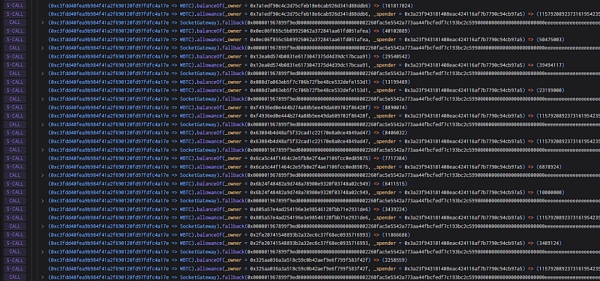

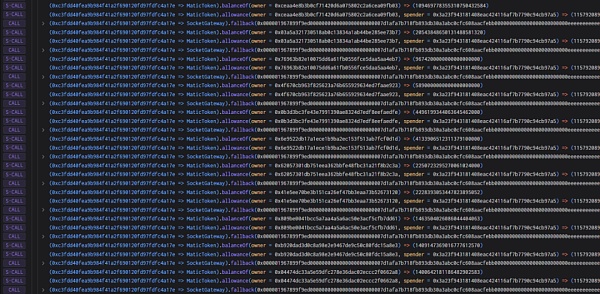
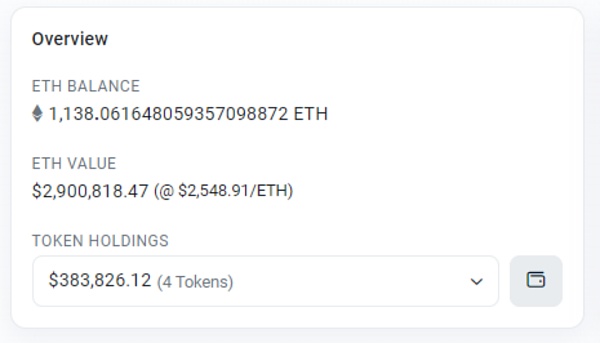
As of press time, nearly US$3.3 million has been stolen Some of the funds were converted into ETH by the attacker, and the hacker's address has not been moved. Beosin Trace will continue to monitor the stolen funds.
Currently, the interoperability protocol Socket releases security event updates on the X platform : Socket has now resumed operations, affected contracts have been suspended, and the damage has been fully contained. Bridging on Bungee and most of its partner frontends has been restored. A detailed analysis of the incident and next steps will be announced soon.
Socke reminds: “Beware of fake Socket accounts in replies trying to phish you. Always double check the account before taking any action.”

This incident also reminds everyone that safety cannot be taken lightly.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Beincrypto
Beincrypto Coindesk
Coindesk Nulltx
Nulltx Cointelegraph
Cointelegraph Bitcoinist
Bitcoinist