Background
At 2:00 pm UTC on October 23, SHAR[1] made a dramatic debut, with its price soaring from $0.00056 at the opening to $0.05986, and its market value soaring to $60 million in just one hour, an increase of nearly 100 times. In the following hours, negative news about the SHAR team[2] began to emerge, with some influencers accusing them of manipulating KOLs to attract investment. Due to negative public opinion, SHAR's price fell to $0.02393 in the next three hours, and its market value fell to less than half of its high point. But despite the negative news, many buyers believed that this would not have a significant impact on the SHAR project, as some well-known KOLs continued to buy in large quantities at low prices and expressed optimism about SHAR's future. Between 6pm and 8pm on October 23, the token price gradually recovered to $0.042.
At 9:26pm UTC on October 23, address CHj3[3] initiated a transaction[4], exchanging 500 million SHAR tokens (about 50% of the total supply) for 19,619 WSOL, almost exhausting the liquidity pool. This operation caused the price of SHAR to plummet to $0.0013 within a minute, and the market value dropped to $3 million, causing investors to suffer a sell-off.
Using MetaSleuth for fund flow analysis
Using MetaSleuth, we can clearly track the flow of funds in this incident and reveal some valuable clues. As early as two or three days before the dump, between October 20 and October 22, the perpetrator of this incident (the entity controlling the address CHj3[5]) withdrew a total of 6,045 SOL from four exchanges. The four exchanges are Binance 2[6] 2,595 SOL, KuCoin[7] 950 SOL, MEXC 1[8] 580 SOL, and OKX 1[9] 1,920 SOL. The withdrawn SOL was distributed to 14 addresses, all of which were controlled by the perpetrator of the dump.
The implementers achieved two goals through these addresses: artificially raising the price of SHAR tokens and hoarding a large number of SHAR tokens in preparation for the final dump.
The following is a diagram of the flow of funds from the four exchanges to these 14 addresses:
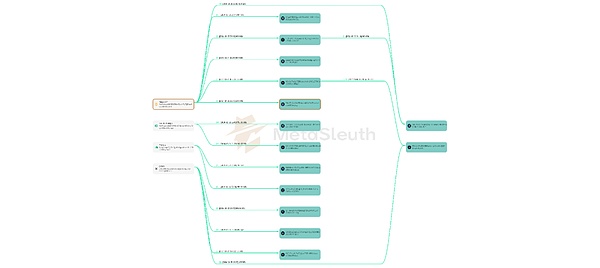
Within two minutes of SHAR going live at 2 pm UTC on October 23, these 14 addresses exchanged all their SOL holdings for SHAR tokens. This move injected a lot of value into the liquidity pool and quickly pushed up the price of SHAR. Here are some of the transactions used by these 14 addresses to purchase SHAR: Q81H[10], 4Jxa[11], 5q5n[12], 3xvB[13]. In the next half hour, the implementer transferred all SHAR held in these 14 addresses to 104 other addresses under its control to further disperse these tokens. Below is a flow chart of SHAR distribution funds for 4 of these 14 addresses.

This decentralized strategy makes it seem that no single address holds a large number of SHAR tokens from the on-chain data, thereby reducing outside concerns about the security of SHAR assets. However, an analysis of the flow of funds clearly shows that although these large amounts of SHAR tokens were dispersed to multiple addresses, they were ultimately controlled by the same entity (the implementer). The implementer retained the ability to sell all of these SHAR tokens at any time, thereby being able to extract potential value from the liquidity pool, which indicates that SHAR tokens present significant security risks. This model of centralized control and decentralized disguise not only exacerbates the market's opacity, but also directly threatens the safety of investors' funds.
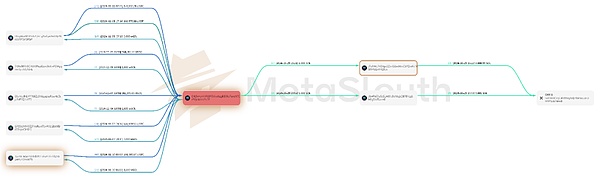
Finally, as the price of SHAR rose, the implementer seized the opportunity to dump the market. At 9:25 pm UTC on October 23, the implementer transferred and concentrated all SHAR tokens from the 104 addresses under his control to the address CHj3[14]. Just one minute later, address CHj3 initiated a transaction[15] to sell off the accumulated 500 million SHAR tokens at one time. This transaction almost depleted the SOL reserves in the liquidity pool, and the implementer obtained 19,619 SOL tokens, worth about $4.2 million. At 9:26 pm on October 23, all users who still held SHAR became victims of this dump, and the value of their SHAR holdings plummeted to one-tenth of the original value in just one minute. The following is a flow chart of funds where some SHAR tokens were concentrated (from 104 addresses) to address CHj3 and then sold to the liquidity pool.
In order to track how the implementer cashed out the 19,619 SOL illegally obtained, we continue to track the flow of these funds. The 19,619 SOL remained in address CHj3[16] for nearly a week until 4:21 PM UTC on October 29, when the actor initiated two transactions (ajqYwt[17] and 3uD6Ys[18]) to transfer 6,000 SOL to another address under his control, J7aV[19]. In the next 20 minutes, the actor deposited 6,000 SOL into the OKX[22] exchange through two additional transactions (5STJND[20] and 3z6C72[21]). Subsequently, at 7:52 PM UTC on the same day, another 5,000 SOL were transferred to address J1wF and transferred to the OKX exchange via transaction at 7:53 PM. Between November 4 and November 10, the implementers gradually converted the remaining 8,600 SOL in address CHj3 into USDC and USDT. Here is a list of all swap transactions: 2rGGMf[27], 5cWJte[28], 4AE6z7[29], 5HovYa[30], 4Da6zR[31], 5P9rmx[32], 5AAHn1[33], 5nm1Xy[34], Mn3Rxa[35]. As of 8:30 AM UTC on November 14, 2023, the implementer still has $1.41 million USDC and $168,000 USDT obtained through the swap in the address CHj3. In addition, there are still about 19 SOLs in the CHj3 address that have not been redeemed. Below is a diagram of all swap transactions (left) and funds deposited into OKX (right).
Key addresses and transactions
Dumping address: CHj3vHyMhF6DF3VkwhzgK833o7uvsN7CrPVyUdmbFo5E.
14 addresses controlled by the dumper that bought a large amount of SHAR at a low price at the opening:
•E78TudQEcPwqiwnJ5HYEjJzogKPVAHGcLx7YRonxMuU3•5Cyg8Y4jEKKgna8Pf4xVXWLtNRZ mJQksU23p1GyKnToU•EzHJnPZ83RKvXzGDZLtfgoEBWoVjLEetMHFos2XcES6g•5rXZD1pZjJqSLCNRS xhn3MQLvRQUQB5nDD1Gf8nNXjT3•5MMdwsfXXcZNpK95mHFTtYz8K7JQ3JcboRNAimH61suC•DZnhX2V G7LKLvfB747DgAmahGBdARevBfeTM4K1p1Rz7•BnCFNcGHh6pMZXgHUHJi4a82Vfo2Xtcw818b9FNMU49 P•75fXUzEqjNeBtqhXzjAbVKa84AcfnvG59nMUnvb3SXUx•DEGdacTknp6BSYQc6fhJdfq9dZNZM3T4N BTSt8jnkygA•H6x6k37wSe7ZBUct4eHyHn6W1o2TTXfAy2z9WyvUNLpZ•Bhx3ZqViaRA4ZbXapro4Vak YuS5bwhu2rc4cS8Dog1cy•RSaAciLFtxDVtBH3awdnrjrDmcGUQBjYTon2FPRpCJG•3UtiQzi1HGH7sEg28T1sZpeQPLAb4m6Hive2cW6CV9XR•86DrFintdQt5w7jyJjobFQ5hVU63rbneYnDfkqC9xAbL
Transactions cashed out via OKX1 (5VCwKtCXgCJ6kit5FybXjvriW3xELsFDhYrPSqtJNmcD):
left;">•5STJNDbQBMbigzHf6mzCrtiM6s8QJjpQazzu5j7zC61uBB46V9NkumCw8UwWHXg7YxpomAFN664PnxHYMAU353q2•3z6C72fm6VVGdkFW3VcpjTccq725ZuVWpcZJv3GM3DB p3D3oLVjq2nyaRDhNZbmG95fi9cTTZfZ8bT22rdXjdEfR•64wMUp3VFz7pxZEpZak9uXAPfbEMBDiTWUGZLgECLn8fSMPexuR5ifRqJTSTpe98ELzRG676Pfe9xoXmG9DreiG1
Explore more details now and discover valuable clues: https://metasleuth.io/result/solana/CHj3vHyMhF6DF3VkwhzgK833o7uvsN7CrPVyUdmbFo5E?source=5e4fca36-208b-4714-afb3-0800d5355323[36].
 Edmund
Edmund







