Author: JW, Four Pillars Researcher; Translation: Jinse Finance xiaozou
Abstract of this article:
Modern crypto wallets have three basic components: key management for handling cryptographic keys, accounts for user authentication and interaction, and interfaces for user engagement. Each part has different challenges and innovations, which together shape the overall wallet experience.
Key management has evolved from simple private key management to more complex solutions: Shamir's Secret Sharing scheme splits keys into multiple fragments, Threshold Signature Schemes supports multi-party computation without rebuilding keys, and Trusted Execution Environment uses hardware-level isolation. Projects such as Privy, Particle Network, and Turnkey have adopted these approaches in practice.
Account abstraction makes blockchain interactions more user-friendly by converting complex accounts into programmable interfaces. This enables features like gas-free transactions, social recovery, and customized security settings, making blockchain technology more accessible to mainstream users, as demonstrated by projects like Abstract’s Global Wallet.
Chain abstraction solves the complexity of cross-chain interactions by making the various blockchains invisible to the end user. Users can manage balances across chains, pay with any token, and seamlessly interact with multiple blockchains while maintaining decentralization and security. One Balance’s Credible Accounts system shows us one way to achieve these features.
The crypto industry is rapidly moving from a desktop-first to a mobile-first development model, and platforms like Zora are leading the transition by providing a sophisticated mobile experience while maintaining the complexity of the blockchain under the hood.
The future of wallet development lies in simplifying the user experience without compromising security. The path to wider adoption requires moving from private keys to social logins, while also having a seamless experience comparable to Web2 applications and retaining the core advantages of blockchain.
1. Introduction to the wallet stack
For crypto applications facing end users, wallets are far more than digital containers for assets - they are the gateway to the entire blockchain experience. Every interaction with a crypto application, from initial setup to daily transactions, flows through the user's wallet. This makes the wallet not just a function, but the most basic infrastructure that determines the user's blockchain experience.
Creating a new wallet and depositing funds into it requires users to invest a lot of time, energy, and risk tolerance. While this high threshold drives up the user acquisition cost of the application, it also creates a strong retention mechanism - once a user uses a wallet, he is likely to use it all the time, and will not choose to switch to another wallet and go through the process again.
However, despite the critical role they play, crypto wallets have earned a reputation for having one of the most technically challenging user experiences. First-time crypto wallet users often find themselves lost in a maze of technical concepts — private keys, public keys, seed phrases — leaving little room for error. This complexity has led many to question whether such a steep learning curve is really necessary to fully utilize blockchain technology.
However, this is finally changing. After years of stagnation, wallet technology is experiencing a major renaissance due to an increased focus on user experience. Modern wallets are building a bridge between the convenience of Web2 and the security of Web3 through innovations such as social login authentication, biometric verification, and gas fee abstraction. These developments are finally bringing crypto wallets closer to the user-friendly experience people have come to expect from modern applications.
The technical infrastructure of a blockchain wallet consists of three basic layers:
Key Management:This foundational layer orchestrates the generation, storage, and recovery of cryptographic keys. It encompasses key technical decisions about cryptographic methods, security protocols, and access control. Modern solutions have gone beyond basic key storage to include methods such as multi-party computation (MPC), Shamir Secret Sharing (SSS), social login integration, and mobile-friendly Passkey.
Accounts:This layer defines how users are identified and how they interact with the blockchain network. It ranges from basic concepts like external accounts (EOA) to complex concepts like smart contract accounts (SCA). Each type of account can be enhanced with different features—from gas fee sponsorship and multi-signature requirements to customized transaction controls—which ultimately determines the functionality and versatility of the wallet.
Interface:This is where users interact directly with the blockchain. Whether through a browser extension, mobile app, or web interface, this layer provides key points for user operations such as signing transactions, managing assets, and connecting to dApps.
Each layer has its own set of design considerations and trade-offs. How they are implemented and integrated determines the overall wallet experience. In this article, we will look at the components and latest innovations of each layer, exploring how various methods can help create more user-friendly crypto applications.
2. Key Management: Where and How to Store Your Keys
The key management layer contains three key decision points:
Key Generation:The core of the key generation method is to define how to create keys and use them to sign transactions. While the single private key approach remains the traditional approach, the industry is increasingly adopting complex solutions such as multi-party computation (MPC) and Shamir Secret Sharing (SSS). These new approaches distribute the key generation and signing process to multiple parties, thus achieving a better balance between security and usability.
Storage:This component determines where the generated keys or key fragments are stored. The final choice depends on various factors: security requirements, accessibility requirements, operating costs, and the degree of decentralization required. Available options include centralized cloud servers (such as AWS), decentralized storage solutions, personal storage devices, and hardware wallets, each of which has unique advantages and trade-offs.
Authentication:Users prove their identity through various authentication methods to access their own keys. Traditional password systems are giving way to more friendly methods such as social login and Passkey, reflecting the industry's shift towards better user experience, especially on mobile devices.
When deploying a key management system, the components can be configured differently depending on specific needs, whether it is the purpose of the application, technical limitations or business requirements. In current market solutions, the key difference is often the choice of key generation method and authentication method combination, because these choices fundamentally determine the degree of balance between security and user experience.
The earliest key management methods were simple but demanding: users retained full control of their private keys through external accounts (EOAs). While this direct ownership model continues to be widely used, its limitations are becoming increasingly apparent. New users are often frustrated by the technical complexity of key management, and even experienced users face significant security risks - whether it is a potential hacker attack or improper storage of keys leading to permanent loss of funds.
To address these challenges, the industry has developed three different modern key management methods: Shamir Secret Sharing (SSS), which distributes key fragments to multiple locations; multi-party computation (MPC), which supports transaction signing; and trusted execution environment (TEE), which provides a secure enclave for key operations. Each of these solutions addresses the limitations of traditional wallets in a unique way, providing a different balance between security, usability, and decentralization, which we will explore in depth below.
2.1 Shamir Secret Sharing (SSS)
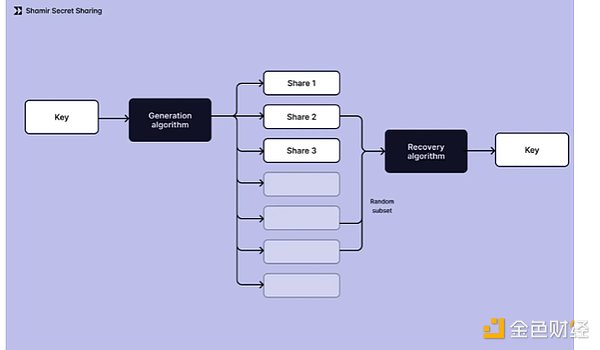
Developed in the 1970s, SSS is a cryptographic algorithm that improves security by splitting keys into multiple fragments. The main purpose of this approach is twofold: it eliminates the single point of failure inherent in single-key management, while ensuring that keys remain recoverable when needed. The key feature of the system is its threshold mechanism - a certain minimum number of key fragments must be combined to reconstruct the original key, and any smaller set of fragments cannot reveal the key content.
In practice, SSS works by generating a private key locally on the user's device, splitting it into multiple fragments, and distributing these fragments to different stakeholders (usually including users and service providers). For transaction signing, the system temporarily reunifies the required number of key fragments to reconstruct the key. This approach enhances security while seamlessly integrating with existing blockchain infrastructure.
- Proven stability: The algorithm has been extensively validated for decades, resulting in multiple battle-tested open source implementations.
- Flexible key distribution: Administrators can precisely customize the total number of key fragments and the threshold required to reconstruct the key.
- Modularity: Storage solutions for individual fragments can be updated independently, enabling targeted system improvements without a comprehensive update.
- Scalability: The client-side computing model ensures consistent performance regardless of the size of the user base.
- Key reconstruction vulnerability: A temporary security vulnerability is generated when key reconstruction is performed during transaction signing.
- Verification limitations: SSS lacks cryptographic methods to verify that fragment deletion was successful or that initial key generation was accurate.
- Complex implementation: The solution often requires complex development expertise, especially in ensuring client-side operation security.
Privy demonstrates an advanced SSS implementation in a modern wallet architecture. Their embedded wallet solution uses a secure isolated iframe environment where a CSPRNG is used to generate wallet credentials. The system then uses mnemonics to generate the wallet’s public address and private key.
After initial generation, the system uses SSS to split the private key into three different fragments:
-Device Share: stored locally on the user’s device, and in the browser’s local storage when using a web application.
-Authentication Share: stored in encrypted form on Privy servers, accessed during the authentication process.
-Recovery Share: can be flexibly stored in Privy’s key management infrastructure or directly by the user.
A key security feature is that the full private key is only temporarily stored in memory during operation and is never permanently saved anywhere. The system’s architecture requires any two fragments to reconstruct the key, creating three strong recovery paths:
-Device Share + Authentication Share:This is the standard user flow. The user authenticates through social login or similar means, triggering the decryption of the user's authentication share, which is combined with the user's local device share.
-Device Share + Recovery Share:This path provides a fallback mechanism when the Privy server is unreachable or the user cannot access their primary authentication method.
-Authentication Share + Recovery Share:Seamless migration of devices is achieved by generating new device shares on other devices.
Privy's advanced recovery system allows secure access to wallets in a variety of situations without compromising security. The deployment successfully achieves a delicate balance between reliable security measures and user accessibility in digital asset management.
2.2 Threshold Signature Scheme (TSS)
TSS is a form of multi-party computation (MPC) in which multiple participants jointly generate and combine signature shares to perform cryptographic operations on shared keys. Unlike SSS, a key feature of TSS is that participants can combine their signature shares to perform operations without having to reconstruct the key.
TSS can be implemented in a variety of ways, from large-scale networks involving multiple computing nodes to simple two-party signature schemes between users and service providers. Participants can contribute to signature generation without directly knowing the key, maintaining high security while implementing a flexible signing process.
- Enhanced security: By eliminating the need for key reconstruction, the single point of failure present in SSS is eliminated
- Flexible architecture: Allows custom configuration of the number of participants and required signatures, supporting a variety of trust models.
-Technology maturity:As a relatively new commercial technology, there are few proven deployment and large-scale deployment cases.
-Scaling limitations:TSS-based systems require communication between participants, resulting in slower processing speeds, especially when ECDSA is deployed on Ethereum.
-Deployment complexity:Multi-party coordination and communication are required, resulting in complex deployment and high operating costs.
In summary, although TSS has attracted attention as a powerful alternative to solving the single point of failure problem of SSS, its current deployment faces some limitations in terms of performance and complexity. These limitations have, to a certain extent, restricted its scalability in practical applications.
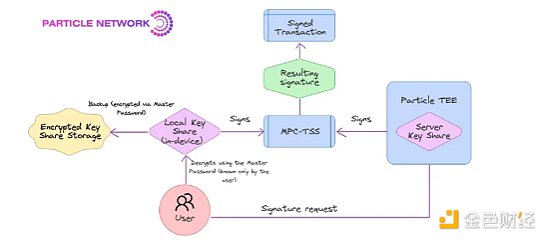
Particle Network is a prime example of providing a user-friendly wallet solution through MPC-TSS deployment. They specifically adopted a 2/2 TSS approach, ensuring that private keys are never centralized in one place throughout their lifecycle (from generation to storage and use).
In the Particle network's TSS deployment, two independent key shares are generated and stored in different locations. One share is stored in the user's local environment, while the other is kept in Particle's trusted execution environment (TEE). Importantly, the individual shares do not disclose any information about the full key, and operations are performed by combining the shares without reconstructing the full key.
As an additional layer of security, users can set a master password to encrypt the locally stored key share. This provides additional security beyond social login authentication while still supporting secure wallet recovery across different devices.
Currently, the Particle network provides MPC signature support for Solana and EVM chains. With this approach, the Particle network provides a secure, non-custodial key management system that remains user-friendly and chain-agnostic.
2.3 Trusted Execution Environment (TEE)
TEE takes a completely different approach from SSS and MPC. It performs all private key-related operations in a securely isolated execution environment (enclave). This security is guaranteed at both the hardware and software levels through platforms such as Intel SGX or AWS Nitro Enclaves.
In a TEE-based system, authorized code runs in a remote enclave with isolated CPU and memory resources, free from external monitoring or interference. The enclave can generate certificates that prove that operations are performed correctly, allowing users to verify that their private keys are being handled securely. This provides a simple and powerful platform for key management. Unlike SSS or TSS, which require complex key splitting or multi-party computation, TEE achieves secure key management through hardware-level guarantees.
-Strong Security: Provides advanced security through hardware-level isolation.
-Verifiability: All operations can be cryptographically proven to be performed as expected.
-Efficient Performance: Compared to TSS, less network communication is required, resulting in relatively faster processing.
-Hardware Dependence: High reliance on specific hardware or vendors may lead to centralization or censorship risks.
- Security vulnerabilities: If the enclave itself is attacked, the entire system may be at risk.
TEE provides a practical solution to the key management problem through hardware-based security. Although it is simpler to deploy than SSS and more efficient to operate than TSS, the reliance on the hardware platform is still an issue that needs to be seriously considered.
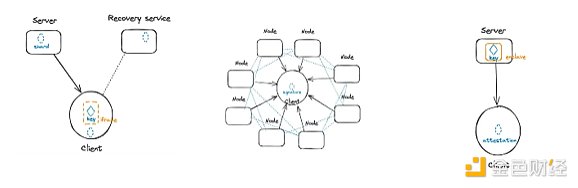
Turnkey’s core security strategy revolves around handling all critical security operations within the TEE. In the Turnkey system, all security-sensitive services—including key generation, signing, and policy engines—are executed within the secure enclave.
Turnkey's architecture consists of two main parts:
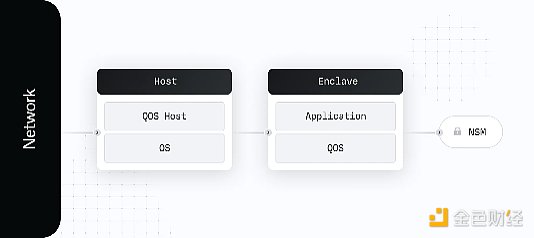
-Host:This is a standard AWS virtual machine that runs basic applications for receiving network traffic and making enclave calls. It acts as a buffer between the enclave and external systems, collecting metrics and other operational information related to enclave operations.
-Enclave:This is an environment that is completely isolated from external connections, with only a virtual serial connection to the host and its own security coprocessor, called the Nitro Security Module (NSM) in AWS. This environment runs QuorumOS (QOS), Turnkey's enclave operating system, and security applications running on it.
With this structure, Turnkey can prove to itself and its users that all critical safety systems are operating exactly as expected. Enclave runs in a highly constrained computing environment with no permanent storage, interactive access, or external networking, so it can provide the highest level of security.
3. Accounts: Invisible Accounts and Chains
As blockchain technology continues to develop and gain mainstream adoption, there is a growing need to abstract its technical complexity. Wallets are the main contact point between users and blockchain networks, but they often have a high barrier to entry. New users must work hard to master unfamiliar concepts such as private key management, gas fee payments, and transaction signatures, and these technical aspects can be daunting and too complicated for ordinary users.
This need for abstraction also reflects the development of other technologies we use every day. Think about how we interact with the Internet: users do not need to understand the TCP/IP protocol or the DNS system to browse websites. Similarly, making a phone call does not require understanding GSM or LTE technology. This pattern is consistent in mature technologies - as they develop, technical complexity is increasingly hidden behind user-friendly interfaces.
In this article, we will explore two fundamental abstract concepts that reshape the wallet user experience. The first is Account Abstraction, which transforms complex blockchain accounts into a programmable, user-friendly interface. The second is Chain Abstraction, which removes the complexity of cross-chain interactions and gives users the ability to operate seamlessly across different blockchain networks without understanding the underlying mechanisms.
3.1 Account Abstraction
The original EOA only provided a few basic functions: storing addresses and signing transactions. The lack of programmability at the account level meant that any advanced features or customized operations were impossible. The introduction of account abstraction changed this situation by enhancing functionality directly at the account level. While account abstraction initially showed promise in solving blockchain user experience challenges, there were several obstacles that delayed its widespread adoption. Complex deployment requirements, high gas costs, and poor compatibility with existing EOAs have all led to slower adoption than we expected. The technology has matured, overcome early challenges, and is now moving towards real-world applications. Some recently launched consumer applications have successfully integrated account abstraction, allowing end users to interact seamlessly with blockchain applications, often without realizing that they are using a wallet or blockchain. This development signals the potential for broader crypto adoption beyond the existing crypto user base. The impact of account abstraction continues to expand across the crypto ecosystem. L2 rollups are now being integrated at the protocol level to enhance the user experience, while wallet-as-a-service (WaaS) providers deploy more advanced embedded wallet solutions. The importance of this technology is further highlighted by the upcoming Ethereum Pectra upgrade, which includes EIP-7702, which allows EOAs to leverage the temporary programmability of SCA on the mainnet.
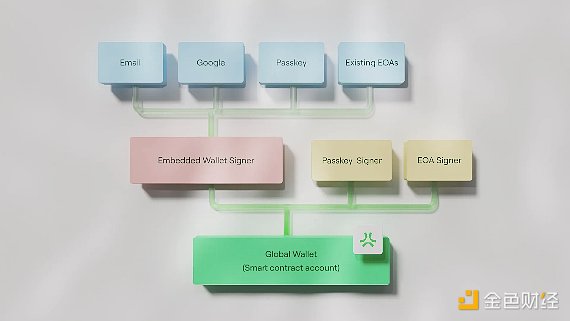
Abstract has developed the Abstract Global Wallet (AGW), a universal, embedded wallet designed to power the applications of its platform. Unlike application-specific wallets, AGW acts as a comprehensive solution that allows users to access any application in the Abstract ecosystem. The wallet solves a real need: allowing users to manage their data and assets across multiple applications through a single access point.
Compared to traditional EOA, AGW implements Native Account Abstraction to create smart contract wallets with greater security and flexibility. This approach treats all accounts as smart contracts, ensuring that they follow the same transaction lifecycle. While traditional Ethereum maintains separate processes for EOA and smart contract accounts, Abstract deployment handles all accounts uniformly, providing consistent functionality for existing EOA users and users using new AA wallets.
The wallet creation process follows a simple two-step approach for EOA and smart contract account (SCA) integration. When a user logs in through common methods such as email, social login, or password, the system creates an EOA wallet in the background. The EOA address then becomes an authorized signer of the deployed smart contract wallet. This design eliminates the complexity of blockchain wallet creation while maintaining its security features.
Abstract's local account abstraction follows the zkSync standard and includes the following key components:
- IAccount standard interface:Defines the methods required by all smart contract accounts, standardizes account behavior, and ensures consistency.
- DefaultAccount conversion:EOA wallets (such as MetaMask) are automatically converted to IAccount's DefaultAccount deployment during transaction processing, enabling them to access SCA advanced features.
- Paymaster support:All accounts can sponsor gas fees for other accounts, or use ERC-20 tokens instead of ETH to pay gas fees, which greatly reduces the entry barrier for new users.
Through this architecture, Abstract supports users to seamlessly access advanced features without understanding the underlying complexity. Users simply log in via familiar methods such as email or social accounts, and the system automatically handles EOA creation and smart contract wallet deployment in the background. After initialization, users can access features such as multi-signature settings, transaction limits, and account recovery mechanisms.
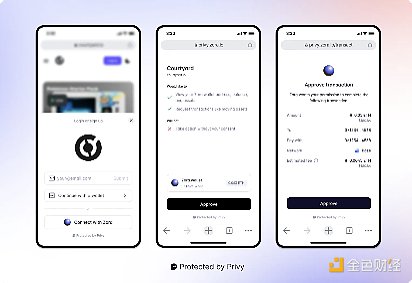
In addition to native account abstraction, AGW also integrates Privy's Cross App Wallet to support its consumer-centric approach. Traditional embedded wallets, while providing simple social login and key management, are limited by the nature of their specific applications, resulting in fragmented asset management across platforms. The Cross-app Wallet concept deployed in AGW solves this problem by allowing users to access their assets and data across multiple applications with a single authentication.
The development of a universal embedded wallet poses significant technical challenges, especially in terms of security architecture. Unlike application-specific wallets that contain security risks, cross-app wallets mean that security issues in one application may affect all associated applications. This requires a more reliable security model. However, the benefits of this approach are huge:
- Simplified asset management: One deposit point can be used for all integrated applications.
- Centralized tracking of assets: Centralized tracking of assets across multiple applications for users and developers.
- Seamless transfers: Direct transfers between different applications within the ecosystem.
3.2 Chain Abstraction
In addition to account abstraction, chain abstraction has recently become an important concept in blockchain development. While account abstraction focuses on improving the user experience within a single blockchain, chain abstraction addresses a different challenge: enabling users to seamlessly interact with assets on multiple chains without involving a bridging mechanism. At its core, chain abstraction is about making the concept of different blockchains transparent to end users, a requirement that becomes increasingly important as more modular blockchains continue to create more complex on-chain ecosystems.
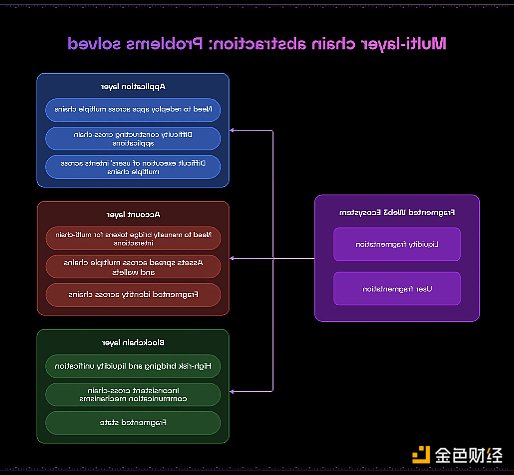
Unlike account abstraction, which is defined by specific technical specifications such as EIP-4337, chain abstraction is a broader approach. It can be deployed across all layers of the blockchain stack - from applications and accounts all the way to protocols - with the goal of abstracting away the complexity of cross-chain interactions.
Chain abstraction can provide an enhanced blockchain user experience, including but not limited to:
- Unified balance management: Users can manage their assets through a single interface, regardless of which blockchain they are on. This unified management approach eliminates the requirement for users to track balances on different chains or understand the underlying blockchain architecture.
-Flexible payment system:Users can pay with any token on any chain. There are dedicated solutions to handle the complexity in the background - accepting various payment tokens, managing cross-chain bridges, and processing gas fees - while providing users with a simple payment experience.
-Seamless cross-chain interaction:While centralized applications can easily provide similar functionality, chain abstraction achieves these benefits while retaining the core principles of blockchain technology (decentralization, personal asset ownership, and security).
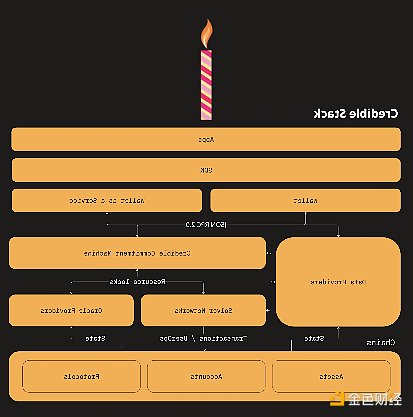
One Balance is a project initiated by the Frontier Research team, who are famous for proposing their CAKE (Chain Abstract Key Elements) framework. At the core of their solution is the "Credible Account" concept, which combines the advantages of EOA and SCA.
Credible accounts extend the traditional blockchain account format, providing trusted guarantees without the need for cross-chain consensus requirements. These accounts run on secure machines selected by the user and make trusted commitments to message signing. They maintain the security guarantees of SCA while supporting key features of account abstraction, including gas abstraction, social recovery, permission policies, and modern authentication methods. Trusted accounts can generate and manage any number of subaccounts across multiple chains, with full control over the state of each chain. They are designed to be universally compatible and can be compatible with a variety of blockchain networks (Ethereum, Solana, Bitcoin) and a variety of smart contracts and assets (including ERC20 tokens, NFTs, DAOs, and DeFi protocols). One Balance's chain abstraction system is based on the following two key components: - Resource Locking: Users under this mechanism make a verifiable commitment to lock their assets until specific conditions are met or expire. Unlike traditional smart contract deposits or ERC20 approvals, these are account-level locks that do not require on-chain finality. For example, when using Ethereum USDC to purchase a Solana NFT, the user will lock their USDC until a specific block height is reached where the NFT was purchased. This design protects solvers from risks such as double-spending attacks and ensures transaction integrity during cross-chain operations.
- Trusted Commitment Machines: This is a secure infrastructure for executing cross-chain transactions. These machines run in a dedicated secure environment and perform two basic functions: they verify the validity of resource locks set by users and ensure accurate execution when the lock conditions are met. For example, when using Ethereum USDC to purchase a Solana NFT, the commitment machine verifies the user's USDC ownership and manages the secure transfer to the seller after the NFT purchase is completed. This automated process follows predefined rules to ensure reliable execution for all parties involved. Commitment machines can be deployed through four methods: TEE, MPC, SCA, or Protocol Virtual Machine.
While One Balance is still in development, it has released an integration example using Privy. Their approach stands out from other chain abstraction solutions by providing a framework for integrating existing blockchain infrastructure or applications without the need for a dedicated chain or system, thereby minimizing barriers to adoption.
4. Interface: Mobile apps are the next frontier
High-quality mobile apps are rare in the crypto ecosystem. Most crypto apps are primarily developed around desktop platforms for two main reasons.
The main reason is the nature of crypto apps themselves. These platforms typically handle complex financial transactions that require detailed information, comprehensive analysis, and multiple data points to be displayed simultaneously - all of which are better suited to desktop interfaces. While mobile platforms excel at providing a streamlined, user-friendly experience, they often have to do so at the expense of the depth and breadth of features required by serious crypto traders and users. This natural limitation makes desktop development a natural priority for most crypto apps.
This desktop-centric development shapes how users interact with crypto apps: they typically maintain a main wallet and connect to various apps as needed. However, this model creates significant friction when switching to a mobile environment. Users find themselves frequently switching between the wallet app and the main app, performing basic operations like logging in or signing transactions over and over again. This back-and-forth is in stark contrast to the seamless interactions that mobile users expect from traditional apps.
The second main reason is the restrictive policies of mobile app stores, with Apple’s App Store being particularly challenging. Their strict policies on crypto-related payments have forced many crypto apps to seek creative solutions. Early attempts to circumvent these restrictions through Progressive Web Apps (PWAs) showed initial promise but ultimately failed to gain traction, primarily due to users’ unfamiliarity with the installation and usage process and the cumbersome operation. This distribution challenge is further highlighted by the success story of Telegram App Center, which has managed to harvest a staggering 500 million MAUs across more than 1,000 small apps, demonstrating that the potential is huge when crypto apps are given an effective distribution channel.
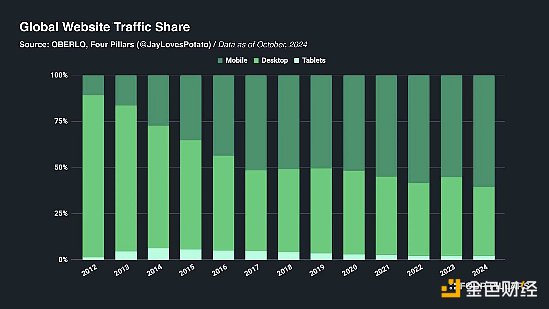
However, the situation is slowly changing. As the crypto market expands from a pure financial services market to more consumer-friendly areas such as meme coins and artificial intelligence applications, we are seeing a resurgence in the mobile-first development model. This trend evolution is evident in the emergence of new players such as social platforms (Farcaster, Interface) and meme coin exchanges (Moonshot, Sauce), which prioritize sophisticated mobile experiences. Even traditional DEXs like Jupiter and Uniswap have set their sights on mobile-optimized interfaces to attract more users. This trend is further supported by infrastructure providers, with WaaS platforms like Privy and Reown (formerly WalletConnect) expanding their SDK capabilities to provide better support for mobile-first development. These developments demonstrate a clear industry-wide understanding that mobile optimization is no longer optional, but a must for mainstream crypto adoption.
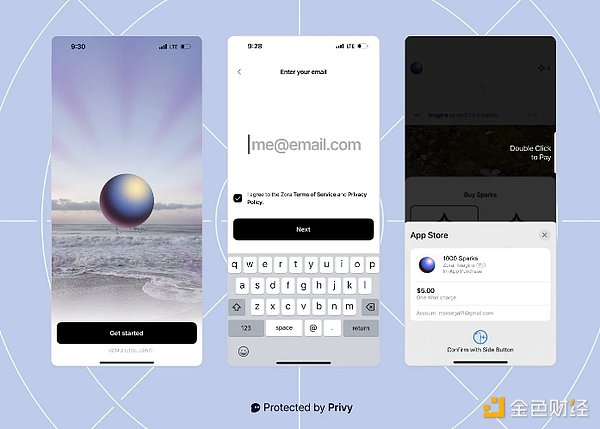
Zora is a prime example of how a crypto application can successfully adopt mobile-first design principles. As a digital creation social network, Zora enables users to seamlessly create, share and trade all forms of digital content - whether it is images and videos, music or memes.
Zora is unique in that it is fully mobile-optimized, from initial account creation to NFT minting. The onboarding process is simple: users only need to enter an email address to sign up, and those who already have a Farcaster or Instagram account can link these accounts to instantly receive personalized feed recommendations and find friends. Perhaps most importantly, Zora leverages native mobile capabilities - users can take photos or videos directly through their phone's camera and instantly mint them into NFTs, creating an experience as natural as posting on traditional social media.
Under the hood, Zora uses complex blockchain technology while maintaining simplicity for users. They have deployed a modern account abstraction stack that combines Privy's embedded wallet technology with Coinbase's smart wallet infrastructure. This technical architecture allows Zora to handle complex operations completely in the background, such as gas fee management and transaction batching. Users don’t need to understand or interact with these technical elements, allowing them to focus solely on content creation and sharing.
One of Zora’s unique innovations is its in-app currency system called “Spark”. Sparks are denominated in units of one millionth of an ETH (equivalent to 1000 Gwei) and can be purchased directly using common payment methods such as credit or debit cards. The system is designed to be very simple: with a sufficient Spark balance, users can mint NFTs with a simple double-click. Each NFT costs 111 Sparks, including gas-free transactions. Importantly, the Sparks you purchase never expire, and they remain valid even if Zora’s minting fees change in the future.
One thing that is particularly noteworthy about Zora is that they have successfully abstracted away the complexity of the blockchain. All of the technical elements that typically create friction in crypto applications—wallet creation, gas fee management, the NFT minting process—are all handled invisibly in the background. The result is an experience that is indistinguishable from any popular social media, while retaining all the benefits of blockchain technology. This approach sets a new standard for what can be achieved with mobile-first crypto applications, demonstrating how blockchain technology can be seamlessly integrated into everyday mobile experiences.
5. Conclusion
The crypto industry has come a long way since applications exploded in the DeFi & NFT summer of 2021. The DeFi & NFT summer marked an era of explosive innovation in the field. The following two years have seen significant advances in infrastructure: modular blockchains have emerged, L1 networks have achieved significant performance improvements, and technologies such as Oracle and bridging have matured significantly. These developments have effectively overcome many of the bottlenecks that once hindered blockchain adoption, especially the persistent problems of slow transaction speeds and high fees.
However, while the technical foundation has been greatly strengthened, the user experience has not kept pace. Despite continued experimentation and development at the application layer, few crypto platforms can match the seamless, intuitive experience that users get from Web2 applications. As our infrastructure becomes more reliable and ready to support the next generation of applications, this experience gap will become increasingly apparent. The most pressing challenge now is to create services that deliver a familiar web2-level user experience while also preserving the unique benefits of blockchain technology.
At the heart of this challenge lies the crypto wallet - perhaps the most critical factor in determining the overall user experience. The wallet is the entry point for new users and the gateway to all important operations within an application, from simple login to transaction approval. Crypto wallets are positioned as the foundational layer through which users interact with the entire crypto ecosystem, and their design and functionality are critical to mainstream adoption.
Innovation in wallet technology is not limited to a single layer, but spans multiple dimensions simultaneously - from key management and account structure to UI/UX. Each layer presents different design parameters that vary depending on the characteristics and needs of the application. Innovation in wallet technology continues, with new narratives emerging around account abstraction and chain abstraction, while also introducing new technologies such as WebAuthn and TEE.
As a result, the success of an application may require a good understanding of the decision-making process at each layer of the wallet architecture. By analyzing successful deployments and understanding the trade-offs, teams can make informed choices based on their specific use cases while maintaining a balance between functionality and user experience.
Crypto’s ability to achieve widespread adoption ultimately depends on our ability to make complex blockchain technology accessible to everyday users without compromising fundamental principles of decentralization and security. While recent case studies show promising progress in this direction and innovative solutions emerging in the ecosystem, we are still in the early stages of this transformation. The challenge ahead lies in creating experiences that not only match but surpass traditional digital services while preserving the unique value proposition of blockchain technology. As wallet technology continues to evolve, it will play an increasingly important role in shaping how the next generation of users interact with crypto applications.
 Alex
Alex