Event background
Recently, the SlowMist security team and the Rabby Wallet team discovered A phishing attack using Google ads. Subsequently, the SlowMist security team teamed up with the Rabby Wallet team to conduct an in-depth analysis of the attack method.
According to the description of the Rabby Wallet team, the team did not purchase any Google ads. However, this fake advertisement jumped to the real official website. Could it be that the fishing gang spent money to promote the real website? wallet?
Judging from the Google search keywords, the top two search results are phishing ads, but the link to the first ad is very abnormal. What it shows is obviously the official website address of Rabby Wallet https://rabby.io. Why do the phishing gangs do this?
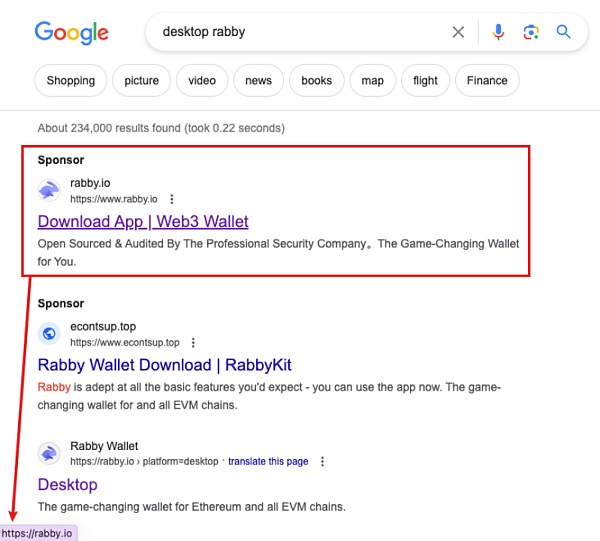
Through tracking, it was found that phishing advertisements sometimes jump to the real official address https://rabby.io. After changing agents to different regions multiple times, they will jump to the phishing address http://rebby.io. , and the phishing address will be updated and changed. At the time of writing, the link leads to the phishing address https://robby.page[.]link/Zi7X/?url=https://rabby.io?gad_source=1.
Technical Analysis
Let’s first talk about what 302 is , 302 is an HTTP status code that represents temporary redirection (Found). After the server receives the client's request, if it needs to temporarily transfer the requested resource to another location, it will return a 302 status code and include a Location field in the response header to indicate the new location to which the client should be redirected. This redirection is temporary.
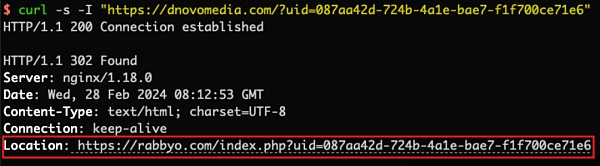
After analysis, it was found that the link of the phishing advertisement will undergo multiple 302 jumps, as shown in the figure below. Use the curl command to request the link. The first time It will 302 jump to the phishing address https://rabby.iopost.ivsquarestudio.com. However, two situations occurred during the second 302 jump:
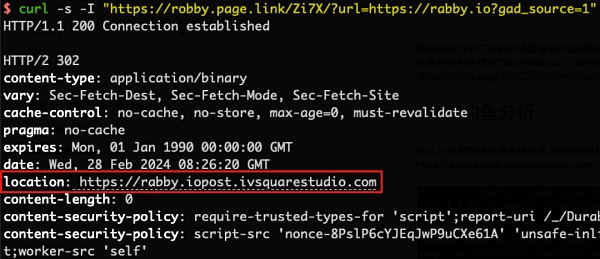
1. When we use the curl command to request the above Location address https ://rabby.iopost.ivsquarestudio.com, will 302 jump to the real official address https://rabby.io.
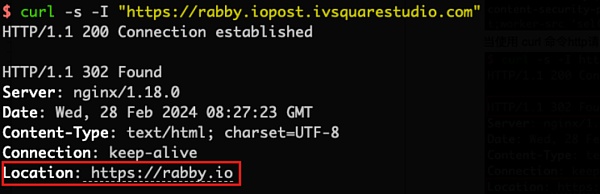
2. However, when we use the curl command to simulate a normal browser requesting the above Location address https://rabby.iopost.ivsquarestudio.com (the request headers include User-Agent, Accept, Referer, Accept-Encoding fields), a 302 jump will be made to a new Location address https://dnovomedia.com?uid=087aa42d-724b-4a1e-bae7-f1f700ce71e6.
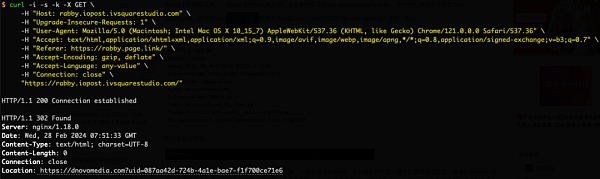
It can be seen that the phishing link will make a judgment during the second 302 jump. When an abnormal browser request is detected, it will be redirected to the official address; and when a normal browser request behavior is detected and If the region is reasonable, it will be redirected to the phishing address.
We tracked and found that the last redirected phishing address was https://rabbyo.com/index.php?uid=087aa42d-724b-4a1e-bae7- f1f700ce71e6.
Open the phishing link and find that this phishing page has almost cloned most of the content of the real official website:

By tracking 302 jumps, we found the following phishing link address:
https://robby.page.link/Zi7X
https://rabby.iopost.ivsquarestudio.com
< p style="text-align: left;">https://dnovomedia.com?uid=087aa42d-724b-4a1e-bae7-f1f700ce71e6
https: //rabbyo.com
https://rebby.io
Threat intelligence platform Querying the two phishing domain names rebby.io and rabbyo.com, we found that they were both registered in January 2024.


Trojan analysis
Looking at the code, we found that the attacker used Russian:

The phishing deployment background program uses Fastpanel (Fastpanel is a virtual host management panel developed by hosting providers in Russian-speaking areas):

Then we reviewed the source code of the phishing webpage and found that clicking to download the desktop version will perform a client verification:

If the current environment is found to be a Mac computer, it will jump to the download address https://brandsrocket .com/data/rabby-wallet-desktop-installer-x64-latest.dmg.
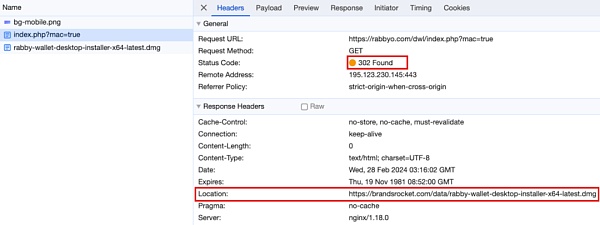
It can be found that the storage space occupied by this Trojan is very small, only 1.1 MB:

Uploaded the Trojan program to an online threat analysis website for analysis, and found that the Trojan sample had been analyzed 19 days before writing this article. And it is recognized as a Trojan horse backdoor program by multiple anti-virus engines.
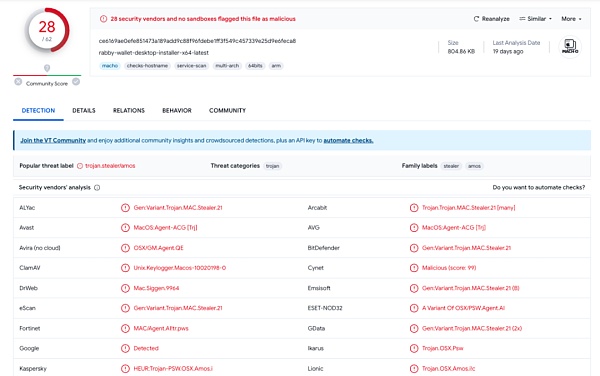
(https://www.virustotal.com/gui/file/ce6169ae0efe851473a189add9c88f96fdebe1ff3f549c457339e25d9e6feca8/detection)
The technology behind phishing
It can be seen that from advertising to phishing website production to Trojan horse production, the phishing group operates smoothly. What is confusing is why the advertising information on Google search shows the official address? And why did it go through multiple 302 jumps? The analysis found that the key operation was that the phishing group used the 302 jump of Google's own Firebase short link service to deceive Google's display.
In order to make this process clearer, we also need to first understand the delivery mechanism of Google ads (as long as you have a Google account, you can log in to Google's advertising management site https: //ads.google.com for promotion settings):
1. First, you need to create a new ad on the advertising management site with the goal of website traffic and the type of search. series.
2. After setting the price and frequency of advertising, select the region and language for advertising. This also explains why ads may not necessarily appear when searching for keywords in different regions or different language environments.
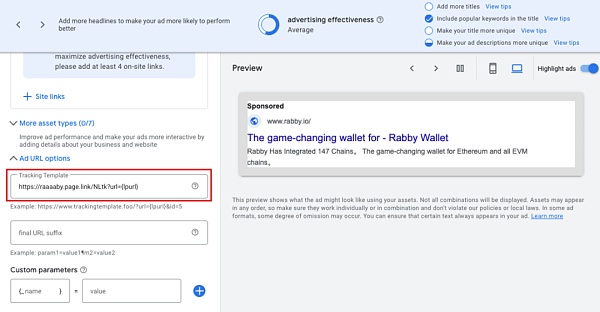
3. The crucial step is to set up the tracking template. Tracking templates are an advanced feature of Google Ads that allow third parties to track ad links.
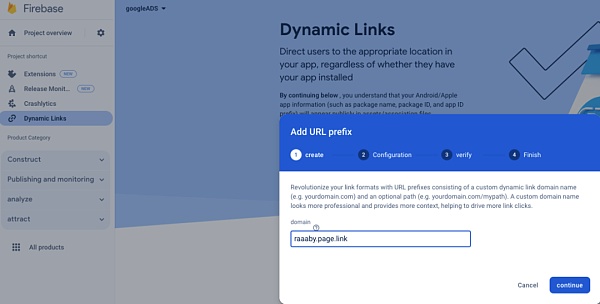
We noticed that the first jump link domain name used by the phishing page is page.link. This is actually a short address service of Google's Firebase. This service allows binding any redirect address to a page.link in the subdomain name.
Since the third-party tracking link needs to be an address certified by Google, and page.link happens to be Google's own domain name, the phishing gang bypassed this restriction.
4. After the advertisement is placed, since Google will not check whether the 302 jump link has changed in real time, nor will it modify the advertising information in real time, so The phishing gang will modify the redirection to the phishing URL after the advertisement has been placed for a period of time.
Similar fishing routines also appear on various chat software. Take Telegram, a chat software, as an example. When you send a URL link during a chat, the Telegram background will capture the URL link domain name, title, and icon for preview display.
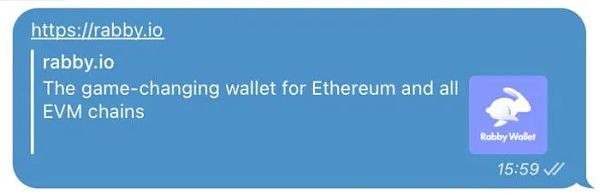
(This picture is for demonstration only)
However, Telegram did not prevent 302 jumps when grabbing preview information. Therefore, if the user only judges based on the information on the page and then clicks on the link, he may jump to the preset phishing address.
Summary
Please look for the official Rabby Wallet The address is https://rabby.io. Do not trust any advertising address displayed in the search results. If you are unfortunately caught, please transfer your wallet funds as soon as possible and conduct a comprehensive anti-virus check on your personal computer. Usually, before clicking on the website link Be skeptical; for more security knowledge, it is recommended to read the "Blockchain Dark Forest Self-Rescue Handbook" produced by the SlowMist Security Team: https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob /main/README_CN.md.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Coinlive
Coinlive  Coinlive
Coinlive  Coinlive
Coinlive  Coinlive
Coinlive  Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph