On March 28, 2024, Prisma Finance suffered a flash loan attack, and the project lost approximately US$12.21 million.

SharkTeam conducted a technical analysis of this incident and summarized the security precautions. We hope that subsequent projects can learn from this and jointly build a security defense line for the blockchain industry.
1. Attack transaction analysis
Attacker 1: 0x7e39e3b3ff7adef2613d5cc49558eab74b9a4202 (abbreviated as 0x7e39)
Attack contract 1: 0xd996073019c74b2fb94ead236e32032405bc027c (abbreviated as 0xd996)
Attacker 2: 0x7fe83f45e0f53651b3ed9650d2a2c67d885 5e385
Attack contract 2: 0x4148310fe4544e82f176570c6c7b649290a90e17
The target contract being attacked: 0x1cc79f3f47bfc060b6f761fcd1afc6d399a968b6
The attack contains 16 transactions, taking the first attack transaction as an example:
0x00c503b595946bccaea3d58025b5f9b3726177bbdc9674e634244135282116c7
The attack process is as follows:
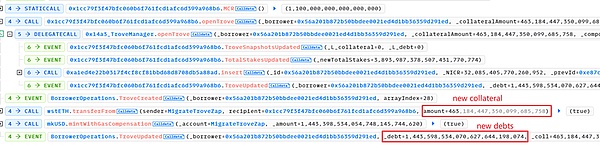
1. Read the address 0x56a201b872b50bbdee0021ed4d1bb36359d291ed (abbreviated as 0x56a2) in the target contract all collateral and debts.
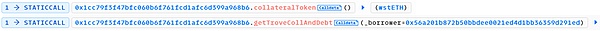
The return result is as follows:
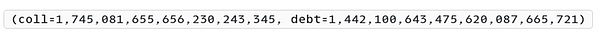
Address 0x56a2 has a total of 1,745 wstETH as collateral in the target contract, and a total debt of 1,442,100 mkUSD.
2. Attacker 0x7e39 calls the flashLoan function in the mkUSD debt contract by attacking contract 0xd996.
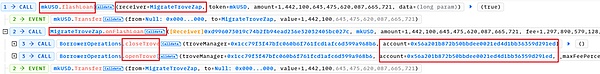
The parameter receiver is set to MigrateTroveZap, and amount is all the debt queried above.

Then, the onFlashLoan function in the receiver (here MigrateTroveZap) will be called in the flashLoan function.
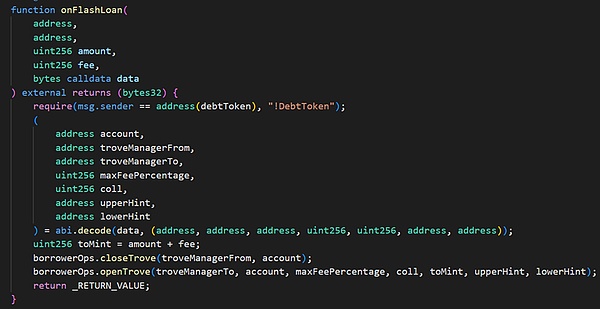
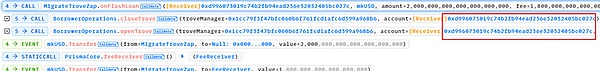
The onFlashLoan function first repays all the original debts through flash loans, withdraws the collateral to the receiver, and then the receiver re-mortgages a certain amount of collateral and borrows a certain amount of debt. There are two main functions called:
(1) closeTrove function, which repays the debt and extracts all collateral (1745.08 swtETH) from troverManager to receiver (here is the MigrateTroveZap contract);
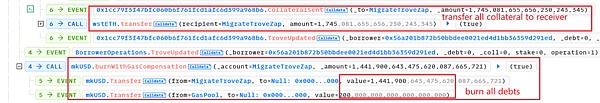
(2) openTrove function, the receiver re-mortgages 463.18 wstETH into troverManager and incurs a debt of 1,443,598 mkUSD.
As can be seen from the above data, after the execution of the flashLoan function is completed, the collateral extracted from troverManager and belonging to address 0x56a2 is still retained in the receiver, and the amount is approximately 1745.08 – 463.18 = 1281.90 wstETH.
3. Attacker 0x7e39 borrowed 1 wstETH from Balancer through flash loan by attacking contract 0xd996.
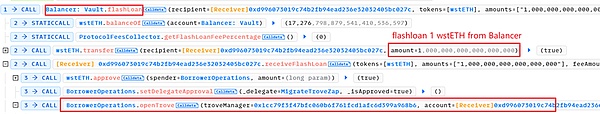
Then, mortgage 1 wstETH and borrow debt of 2000 mkUSD, plus fee, the total debt is 2200 mkUSD.
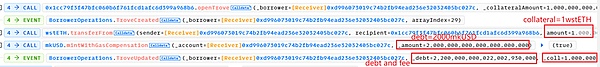
4. Similar to step 2, call the flashLoan function in the mkUSD debt contract. The parameter receiver here is still set to MigrateTroveZap, and the amount is the entire debt after pledging 1 wstETH, which is 2000 mkUSD. . In the FlashLoan function, the onFlashLoan function in the receiver is called, and then the closeTrove and openTrove functions are called.

It's just that the parameter account in the closeTrove and openTrove functions here is no longer the address 0x56a2 above, but the attack contract 0xd996 that pledges 1 wstETH.
(1) closeTrove function, repay the debt and withdraw all collateral (1 swtETH) from troverManager to receiver (this is still the MigrateTroveZap contract). At this time, there are 1281.90 +1=1282.90 wstETH in the receiver.
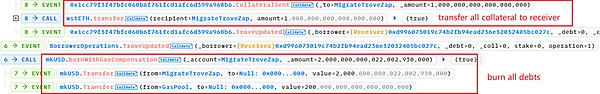
(2) openTrove function, the receiver re-mortgages 1282.80 wstETH (almost all) into troverManager, and incurs a debt of 2001.8 mkUSD.
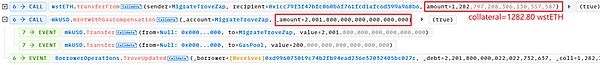
In fact, the 1281.80 wstETH in the collateral here does not belong to the attack contract 0xd996, but to the above address 0x56a2.
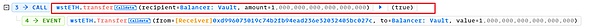
5. Finally, the attacker 0x7e39 called the closeTrove function separately through the attack contract 0xd996, and extracted the mortgaged 1282.80 wstETH into the attack contract 0xd996.
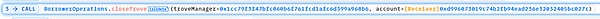
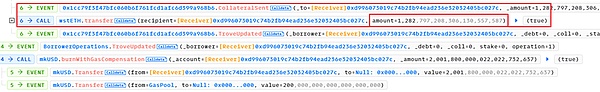
After repaying the flash loan, the attacker still made a profit of 1281.80 wstETH, which is about 2.30M USD.
2. Vulnerability Analysis
The root cause of this incident is that the project contract has logic and permission verification, which makes the attacker This vulnerability can be exploited to obtain pledged assets from other account addresses.
The wstETH finally obtained by the attacker is the collateral of the original address 0x56a2 in the troverManager contract. Through the flashLoan function of the mkUSD contract, the onFlashLoan function in the MigrateTroveZap contract is customized. Parameters, use MigrateTroveZap to turn them into collateral for the attack contract, and then withdraw them.
The attacker manipulates the mortgage and withdrawal of other account addresses through the flashLoan function in the mkUSD contract and the onFlashLoan function in the MigrateTroveZap contract.

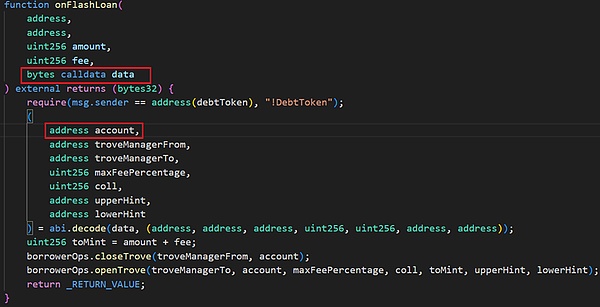
(1) The flashLoan function lacks verification of the parameter receiver address, because the receiver in the onFlashLoan function will receive all the collateral of the account, so the receiver needs to be verified credible;
(2) The onFlashLoan function lacks verification of the account address, because the closeTrove and openTrove functions are both assets of the account being operated, so it is necessary to add permission verification to the account;
In addition to verifying these two address parameters, it may also be necessary to verify the quantity parameters and implementation logic in the flashLoan function.
3. Security recommendations
In response to this attack, we should Follow the following precautions:
(1) During the design and development process of the project, the integrity and rigor of the logic must be maintained, especially when it comes to the transfer of assets. During the process, it is necessary to strengthen the verification of function research permissions to ensure that the caller, calling function, function parameters, transfer logic, etc. are safe and trustworthy.
(2) Before the project goes online, you need to find a professional third-party audit team to conduct a contract audit.
About Us
SharkTeam's vision is to protect the security of the Web3 world. The team consists of experienced security professionals and senior researchers from around the world, who are proficient in the underlying theory of blockchain and smart contracts. It provides services including risk identification and blocking, smart contract audit, KYT/AML, on-chain analysis, etc., and has created an on-chain intelligent risk identification and blocking platform ChainAegis, which can effectively combat the Advanced Persistent Threat (Advanced Persistent Threat) in the Web3 world. , APT). It has established long-term cooperative relationships with key players in various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, polygon, Sui, OKX, imToken, Collab.Land, etc.
Official website: https://www.sharkteam.org
Twitter: https:/ /twitter.com/sharkteamorg
Telegram: https://t.me/sharkteamorg
Discord: https://discord.gg/jGH9xXCjDZ
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance Kikyo
Kikyo Alex
Alex JinseFinance
JinseFinance Alex
Alex nftnow
nftnow Bitcoinist
Bitcoinist Bitcoinist
Bitcoinist Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph