Talking about OP_Codes: How AVM will "restart" the Bitcoin programming era
Bitcoin becomes digital gold only out of necessity? AVM under the Atomicals protocol may "restart" the Bitcoin programming era
 JinseFinance
JinseFinance
Source: SharkTeam
In 2023, the Web3 industry experienced more than 940 large and small security incidents , an increase of more than 50% year-on-year in 2022, with losses reaching US$1.79 billion. Among them, the third quarter had the most security incidents (360) and the largest losses (US$740 million). The losses increased by 47% year-on-year in 2022. Especially in July, a total of 187 security incidents occurred, with losses reaching US$350 million.
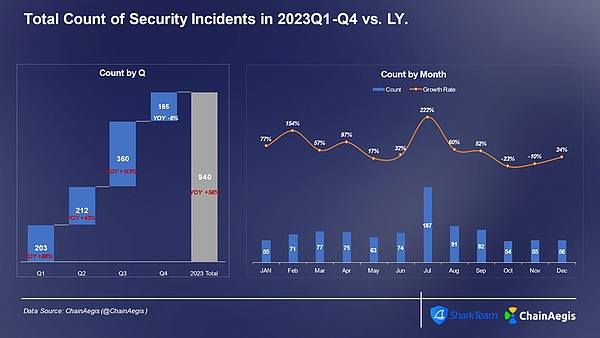
Figure: Number of security incidents per quarter/month in Web 3 2023
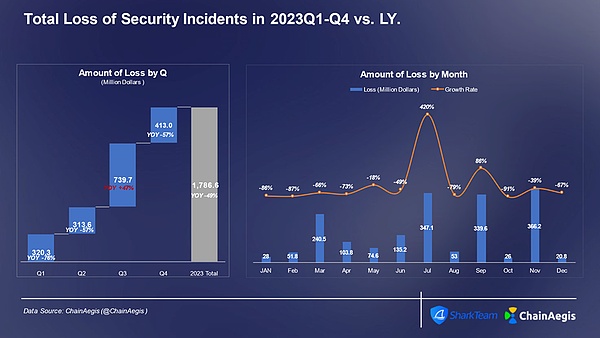
Figure: Web 3 2023 quarterly/monthly security incident losses (millions of dollars)
First of all, hacker attacks are still a major cause of heavy losses. In 2023, there will be 216 hacker attacks, causing losses of US$1.06 billion. Contract vulnerabilities, private key theft, phishing attacks, and state hackers are still important reasons that threaten the security of the Web3 ecosystem.
Secondly, Rugpull and fund disk fraud are on the rise. A total of 250 Rugpull and Scam fraud incidents occurred in 2023, among which such incidents occurred most frequently on BNBChain. Fraudulent projects attract investors to participate by publishing seemingly attractive crypto projects and provide some false liquidity. Once they attract enough funds, they will suddenly steal all funds and transfer assets. This type of fraud will cause serious economic losses to investors and greatly increase the difficulty for investors to choose the right project.
In addition, it has become a trend for ransomware to use cryptocurrencies to collect ransoms, such as Lockbit, Conti, Suncrypt and Monti. Cryptocurrencies are more difficult to track than fiat currencies, and it is increasingly important to use on-chain analysis tools to track and locate the identities of ransomware gangs.
Finally, in these criminal activities such as cryptocurrency hacking and fraud and extortion, criminals usually need to perform on-chain fund transfers and OTC after obtaining cryptocurrency. money laundering. Money laundering usually adopts a mixture of decentralized and centralized methods. Centralized exchanges are the most concentrated places for money laundering, followed by on-chain currency mixing platforms.
2023 is also the year when Web3 supervision has achieved substantial development. FTX2.0 will be restarted, Binance will be sanctioned, and USDT will ban Hamas and other addresses. In 2024 In January, the SEC passed the Bitcoin spot ETF. These landmark events represent that supervision is deeply involved in the development of Web3.
This report will conduct a systematic analysis of key topics such as Web3 hacking attacks, Rugpull fraud, ransomware, cryptocurrency money laundering, and Web3 regulation in 2023 to understand The security posture of the cryptocurrency industry’s development.
Contract vulnerability attacks mainly occur on Ethereum in 2023 In the second half of the year, a total of 36 contract vulnerability attacks occurred on Ethereum, with losses exceeding US$200 million, followed by BNBChain. In terms of attack methods, business logic vulnerabilities and flash loan attacks are still the most common.
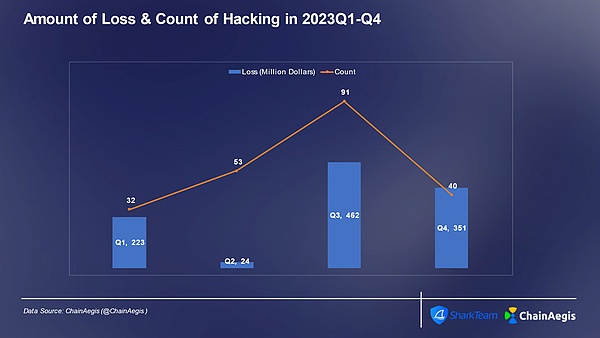
Figure: Number of hacker attacks and amount of losses (millions of dollars) in each quarter of Web 3 2023< /p>
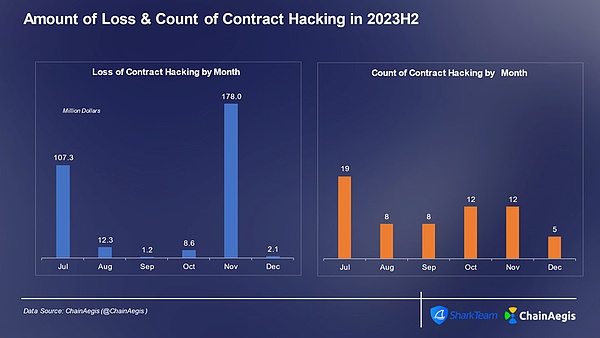
Figure: Number of monthly contract vulnerability exploit hacking attacks and amount of losses in Web 3 2023H2
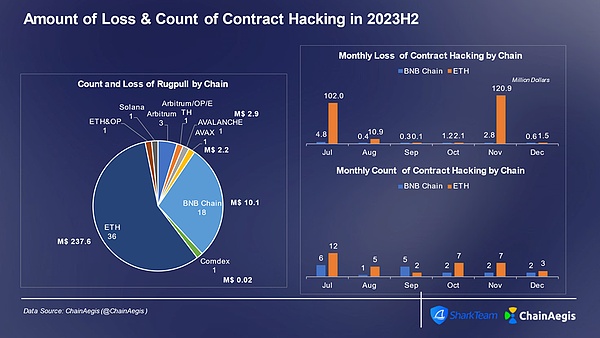
Figure: Number of contract vulnerability exploitation attacks and amount of losses per month on different chains in Web 3 2023H2
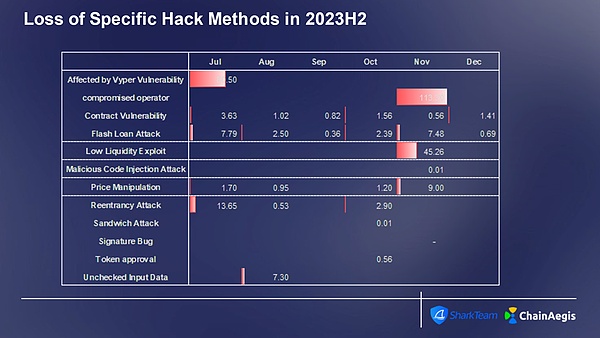
Picture: The number of specific attack methods and the amount of loss using Web 3 2023H2 contract vulnerabilities
Take JPEG'd being attacked as an example:
Attacker address: 0x6ec21d1868743a44318c3c259a6d4953f9978538
Attacker contract: 0x9420F8821aB4609Ad9FA514f8D2F5344C3c0A6Ab
Attack transaction:
0xa84aa065ce61dbb1eb50ab6ae67fc31a9da50dd2c74eefd561661bfce2f1620c
(1) Attack The author (0x6ec21d18) created the contract 0x466B85B4 and borrowed 80,000 WETH from [Balancer: Vault] through flash loan.

(2) The attacker (0x6ec21d18) added 40,000 WETH to the pETH-ETH-f (0x9848482d) liquidity pool and obtained 32,431 pETH.
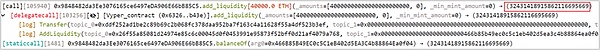
(3) The attacker (0x6ec21d18) then repeatedly removed liquidity from the pETH-ETH-f (0x9848482d) liquidity pool.
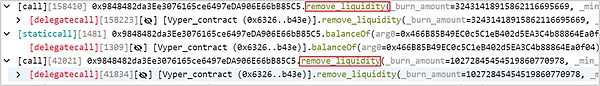
(4) In the end, the attacker (0x6ec21d18) obtained 86,106 WETH. After returning the flash loan, he left the market with a profit of 6,106 WETH.
Vulnerability analysis: This attack is a typical reentrancy attack. After decompiling the bytecode of the project contract under attack, we can find from the figure below: when the two functions add_liquidity and remove_liquidity verify the storage slot value, the storage slots to be verified are different. Using a different storage slot, the reentrancy lock may become invalid. At this time, it is suspected that there is a vulnerability in the underlying design of Vyper.
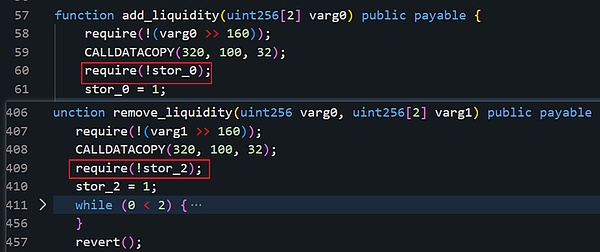
Combined with Curve’s official tweet. Ultimately, it was identified as a Vyper version vulnerability. This vulnerability exists in versions 0.2.15, 0.2.16, and 0.3.0, and has flaws in the reentrancy lock design. We compared the 0.2.14 before 0.2.15 and the 0.3.1 version after 0.3.0, and found that this part of the code is constantly being updated. The old 0.2.14 and newer 0.3.1 versions do not have this problem.
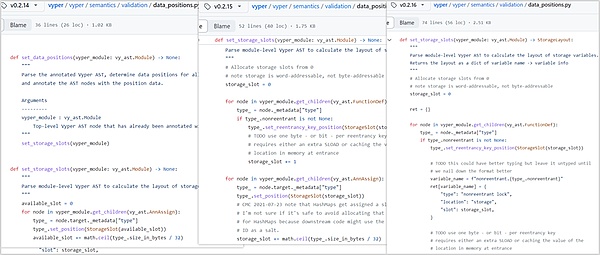
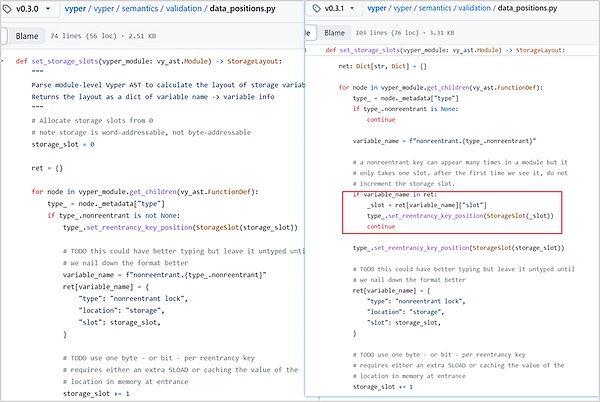
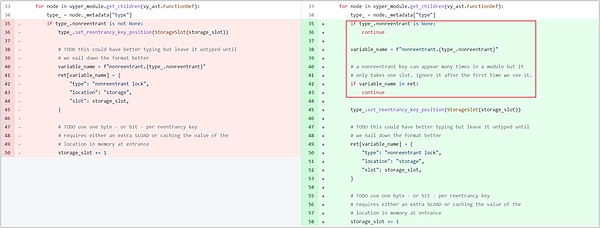
In the reentrancy lock related settings file data_positions.py corresponding to Vyper, the value of storage_slot will be overwritten. In ret, the slot of the lock acquired for the first time is 0, and then when the function is called again, the slot of the lock will be increased by 1. At this time, the reentrant lock will become invalid.
Phishing attack is a network attack method that aims to deceive and induce the target to obtain their sensitive information or induce them to perform malicious operations. This kind of attack is usually carried out through email, social media, SMS or other communication channels. The attacker will pretend to be a trusted entity, such as a project party, an authority, KOL, etc., to lure the victim to provide private keys, mnemonic words or Transaction authorization. Similar to contract vulnerability attacks, phishing attacks showed a high incidence and high losses in Q3. A total of 107 phishing attacks occurred, of which 58 occurred in July.
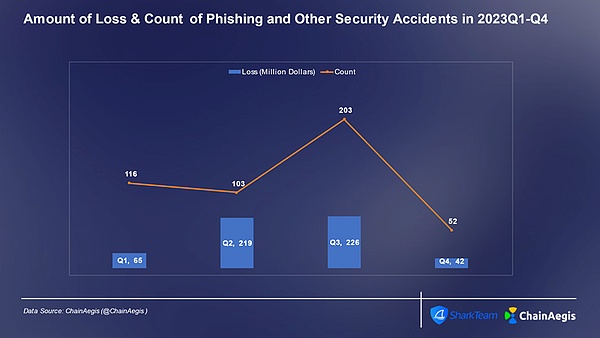
Figure: Number of phishing attacks and amount of losses (millions of US dollars) in each quarter of Web 3 2023< /p>
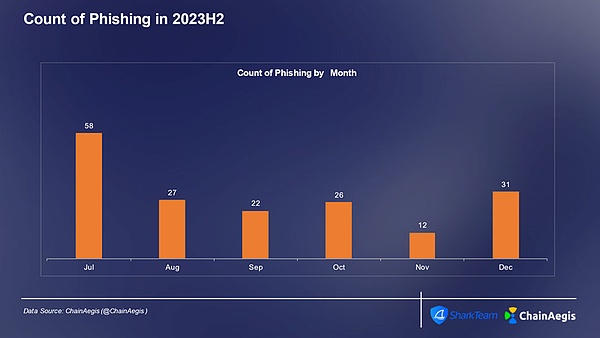
Figure: Number of phishing attacks per month on Web 3 in 2023
On September 7, 2023, the address (0x13e382) suffered a phishing attack and the loss exceeded 2,400 Ten thousand U.S. dollars. Phishing hackers used fund theft, fund exchange and decentralized fund transfer. Of the final lost funds, 3,800 ETH was transferred to Tornado.Cash in batches, 10,000 ETH was transferred to the intermediate address (0x702350), and 1078,087 DAI so far Reserved at intermediate address (0x4F2F02).
This is a typical phishing attack. The attacker steals user assets by defrauding wallet authorization or private keys, forming a black industry chain of phishing + money laundering. At present, more and more fraud gangs and even national hackers are using phishing methods to do evil in the Web3 field, which requires everyone's attention and vigilance.
According to the tracking analysis of SharkTeam’s on-chain big data analysis platform ChainAegis (https://app.chainaegis.com/), we will analyze the typical phishing attack scams Conduct relevant analysis on the process, fund transfer situation and fraudsters’ on-chain behavior.
(1) Phishing attack process
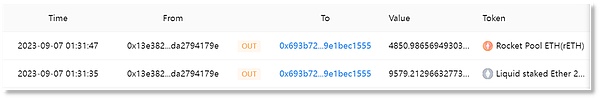
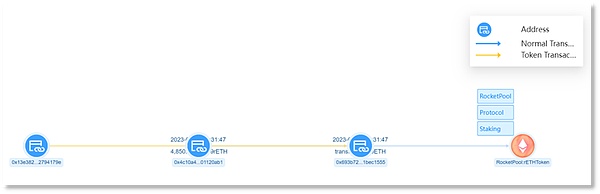
The victim address (0x13e382) passes 'Increase Allowance 'Authorize rETH and stETH to scammer address 1 (0x4c10a4).
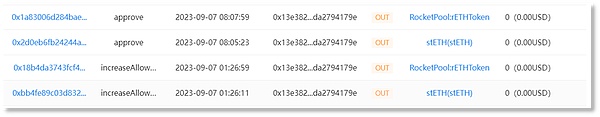
Scammer address 1 (0x4c10a4) transferred 9,579 stETH in the account of the victim address (0x13e382) to scammer address 2 (0x693b72), amounting to approximately US$15.32 million.
Scammer address 1 (0x4c10a4) transferred 4,850 rETH in the account of the victim address (0x13e382) to scammer address 2 (0x693b72), with an amount of approximately 8.41 million Dollar.

( 2) Asset exchange and transfer
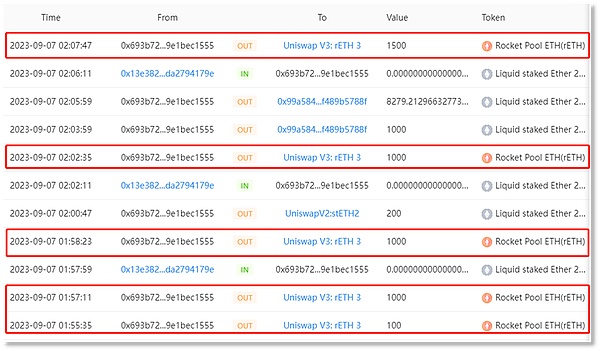
Exchange the stolen stETH and rETH into ETH. Since the early morning of 2023-09-07, scammer address 2 (0x693b72) has conducted multiple exchange transactions on the UniswapV2, UniswapV3, and Curve platforms, converting all 9,579 stETH and 4,850 rETH into ETH, with a total exchange of 14,783.9413 ETH.
stETH exchange:

rETH exchange:

Part of the ETH is converted into DAI. Scammer address 2 (0x693b72) exchanged 1,000ETH into 1,635,047.761675421713685327 DAI through the UniswapV3 platform. The scammers used decentralized fund transfer methods to transfer stolen funds to multiple intermediate wallet addresses, totaling 1,635,139 DAI and 13,785 ETH. Of these, 1,785 ETH was transferred to an intermediate address (0x4F2F02), 2,000 ETH was transferred to an intermediate address (0x2ABdC2), and 10,000 ETH was transferred to an intermediate address (0x702350). In addition, the intermediate address (0x4F2F02) received 1,635,139 DAI the next day
The intermediate wallet address (0x4F2F02) fund transfer:
This address has been transferred through a layer of funds and has 1,785 ETH and 1,635,139 DAI. Decentralized transfer of funds DAI, and exchange of small amounts into ETH
First of all, the scammer began to transfer 529,000 DAI through 10 transactions in the early morning of 2023-09-07 . Subsequently, the first seven transactions totaling 452,000 DAI were transferred from the intermediate address to 0x4E5B2e (FixedFloat), the eighth transaction was transferred from the intermediate address to 0x6cC5F6 (OKX), and the last two transactions totaling 77,000 DAI were transferred from the intermediate address to 0xf1dA17 (eXch).
Secondly, on September 10, 28,052 DAI was exchanged for 17.3 ETH through UniswapV2.
From September 8th to September 11th, 18 transactions were carried out, and all 1,800 ETH was transferred to Tornado.Cash.
After the transfer, the address still had 1078,087 DAI of stolen funds that had not been transferred out.
Intermediate address (0x2ABdC2) fund transfer:
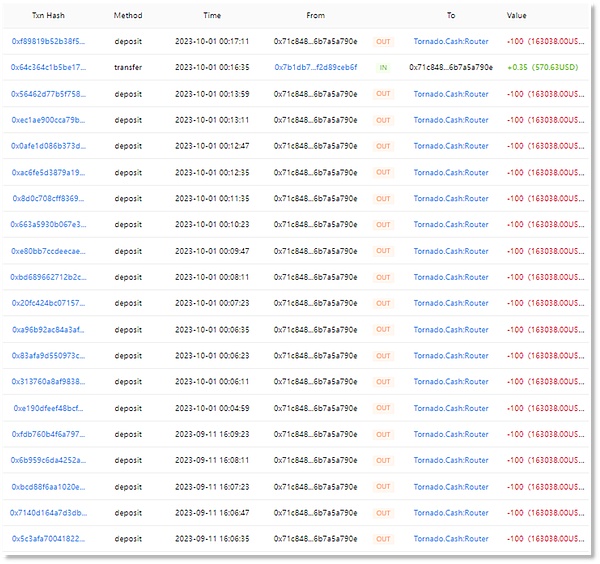
This address has been transferred through a layer of funds. Own 2,000ETH. First, this address transferred 2000ETH to the intermediate address (0x71C848) on September 11.
Then the intermediate address (0x71C848) transferred funds twice on September 11 and October 1 respectively, with a total of 20 transactions, each transferring 100 ETH , a total of 2000ETH was transferred to Tornado.Cash.
Intermediate address (0x702350) fund transfer
This address has been transferred through a layer of funds and has 10,000 ETH. As of October 8, 2023, 10,000 ETH is still in the account at this address and has not been transferred.
Address clue tracking: After analyzing the historical transactions of scammer address 1 (0x4c10a4) and scammer address 2 (0x693b72), it was found that there was an EOA address (0x846317) transferred 1.353 ETH to scammer address 2 (0x693b72), and the source of funds for this EOA address involves hot wallet addresses with centralized exchanges KuCoin and Binance.
The frequency of Rugpull fraud incidents will be more significant in 2023 The upward trend reached 73 transactions in Q4, with a loss amount of US$19 million, and the average loss per transaction was approximately US$26,000. The quarter with the highest proportion of Rugpull fraud losses throughout the year was Q2, followed by Q3, with the loss proportion exceeding 30%.
In the second half of 2023, a total of 139 Rugpull incidents and 12 fraud incidents occurred, causing losses of US$71.55 million and US$340 million respectively.
In the second half of 2023, the Rugpull incident mainly occurred on BNBChain, reaching 91 times, accounting for more than 65%, and the loss reached US$29.57 million, accounting for 41%. . Ethereum (44 times) followed with a loss of $7.39 million. In addition to Ethereum and BNBChain, the BALD Rugpull incident occurred on the Base chain in August, causing serious losses of US$25.6 million.
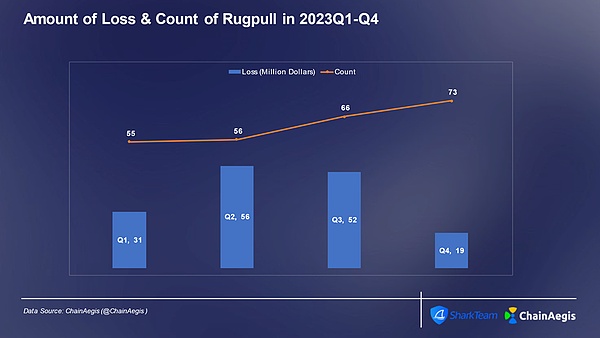
Figure: Number of Rugpull and Scam incidents each quarter and amount of losses (millions of dollars) in Web 3 2023
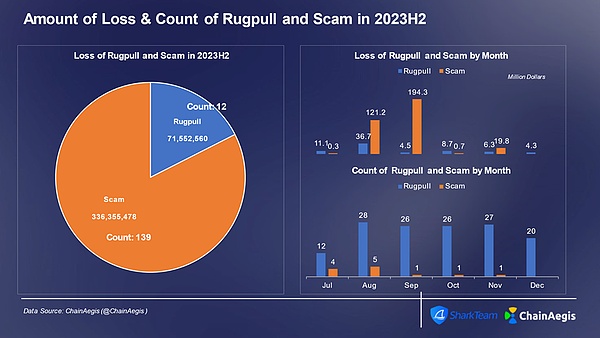
Figure: Number of Rugpull and Scam incidents and amount of losses per month in Web 3 2023H2
< p style="text-align:center;">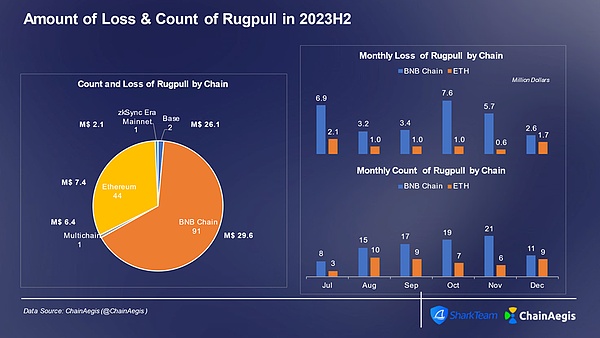
Figure: Web 3 2023H2 monthly number of Rugpull events and loss amount on different chains
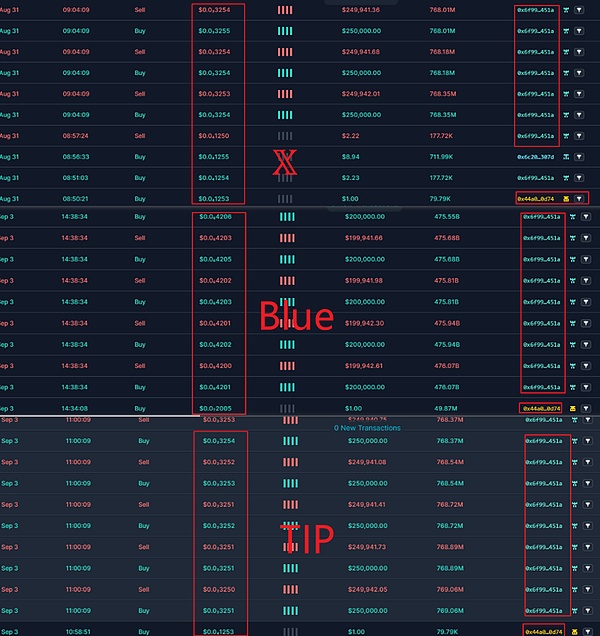
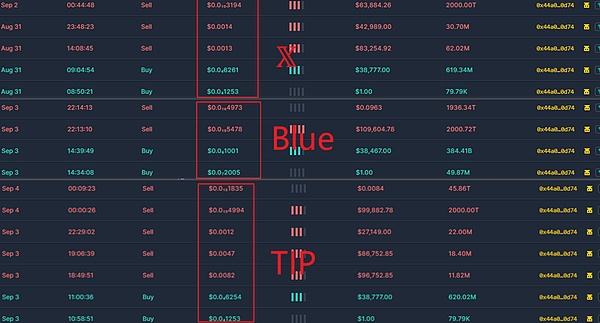
A Rug fraud factory model is popular on BNBChain, which is used to manufacture Rugpull tokens in batches and carry out Fraud. Let’s take a look at the Rugpull factory fraud patterns of fake SEI, X, TIP and Blue tokens.
(1) SEI
First, the fake SEI token owner 0x0a8310eca430beb13a8d1b42a03b3521326e4a58 sold 1U of The price was exchanged for 249 fake SEI.
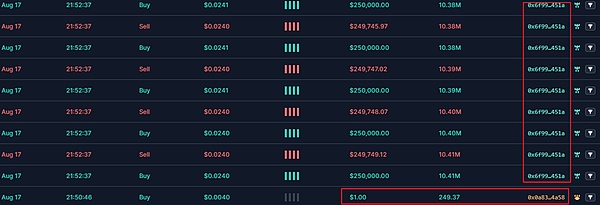
Then, 0x6f9963448071b88FB23Fd9971d24A87e5244451A performed bulk buying and selling operations. Under buy and sell operations, the liquidity of the token increased significantly and the price also increased.
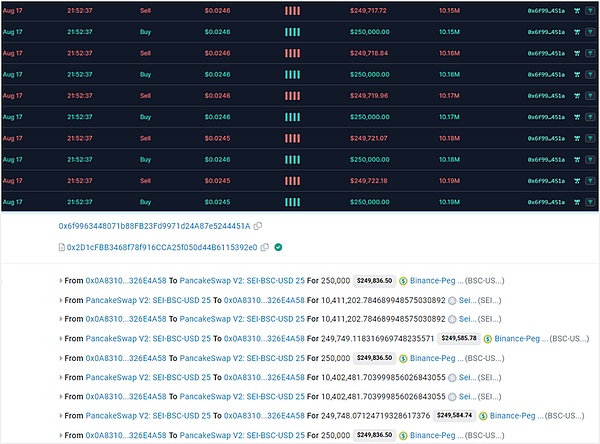
Promote through phishing and other methods to lure a large number of users to buy. As liquidity increases, the price of the token doubles.
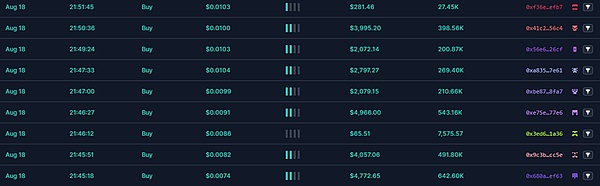
When the price of the token reaches a certain value, the owner of the token enters the market to sell and perform rugpull. As can be seen from the figure below, the entry and harvest time periods and prices are different.
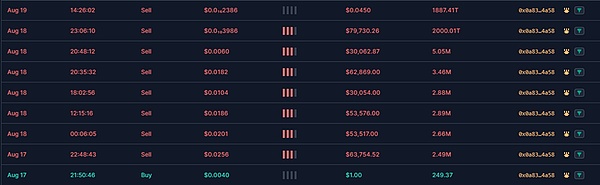
(2) Fake 1U was exchanged for the corresponding token. Then, same as fake Sei tokens.
0x6f9963448071b88FB23Fd9971d24A87e5244451A Batch buying and selling operations. Under buy and sell operations, liquidity increases significantly and prices rise.
Then it is promoted through phishing and other channels to lure a large number of users to purchase. As liquidity increases, the token price doubles.
Similar to the fake SEI, when the price of the token reaches a certain value, the owner of the token enters the market to sell and perform rugpull. As can be seen from the figure below, the entry and harvest time periods and prices are different.
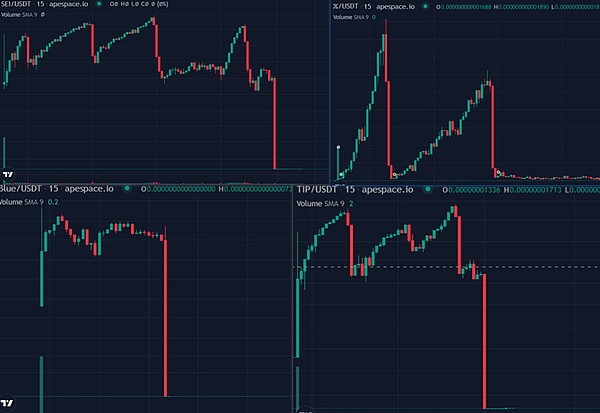
The fluctuation charts of fake SEI, fake X, fake TIP and fake Blue tokens are as follows:
We trace the source of funds and behavior patterns It can be known that:
In the fund traceability content, the founders of the token factory and the token creators’ funds come from multiple EOA accounts. There are also fund flows between different accounts, some of which were transferred through phishing addresses, some were obtained through previous token rugpull behaviors, and some were obtained through currency mixing platforms such as tornado cash. Using multiple methods to transfer funds aims to build a complex and intricate financial network. Different addresses also create multiple token factory contracts and produce tokens in large quantities.
While analyzing the token Rugpull behavior, we found that the address
0x6f9963448071b88FB23Fd9971d24A87e5244451A is one of the funds source. A batch approach is also used when operating token prices. The address 0x072e9A13791f3a45fc6eB6AD38e6ea258C080cc3 also acts as a fund provider, providing corresponding funds to multiple token holders. .
Through analysis, it can be concluded that there is a Web3 fraud gang with a clear division of labor behind this series of behaviors, forming a black industry chain, mainly involving hotspot collection and automatic publishing. Coin, automatic trading, false propaganda, phishing attacks, Rugpull harvesting and other links mostly occur in BNBChain. The fake Rugpull tokens issued are closely related to hot industry events and are highly confusing and instigative. Users need to be vigilant at all times, remain rational, and avoid unnecessary losses.
The threat of ransomware attacks in 2023 is still a constant threat Across organizations and businesses, ransomware attacks are becoming increasingly sophisticated, with attackers using a variety of techniques to exploit vulnerabilities in organizations' systems and networks. Proliferating ransomware attacks continue to pose a significant threat to organizations, individuals, and critical infrastructure around the world. Attackers are constantly adjusting and improving their attack strategies, using leaked source code, intelligent attack schemes and emerging programming languages to maximize their illegal gains.
LockBit, ALPHV/BlackCat and BlackBasta are currently the most active ransomware extortion groups.
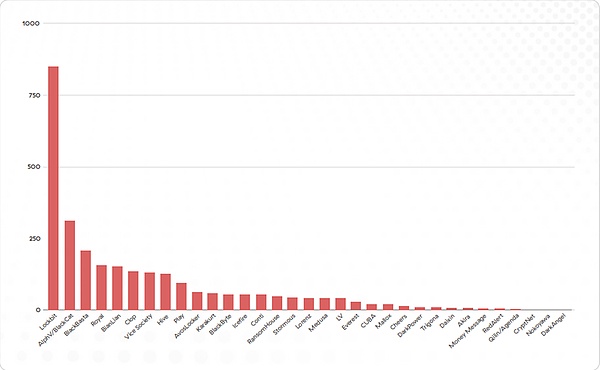
Picture: Number of victims of the ransomware organization
Currently, more and more ransomware uses cryptocurrency to collect payments. Take Lockbit as an example. Companies recently attacked by LockBit include: TSMC at the end of June this year, Boeing in October, and Industrial and Commercial Bank of China in November. Wholly-owned subsidiaries, etc., mostly use Bitcoin to collect ransoms, and LockBit will launder cryptocurrency money after receiving the ransom. Let's take Lockbit as an example to analyze the ransomware money laundering model.
According to ChainAegis analysis, LockBit ransomware mostly uses BTC to collect ransoms, using different payment addresses. Some addresses and payment amounts are summarized as follows. A single ransom of BTC It ranges from 0.07 to 5.8, and ranges from approximately US$2,551 to US$211,311.
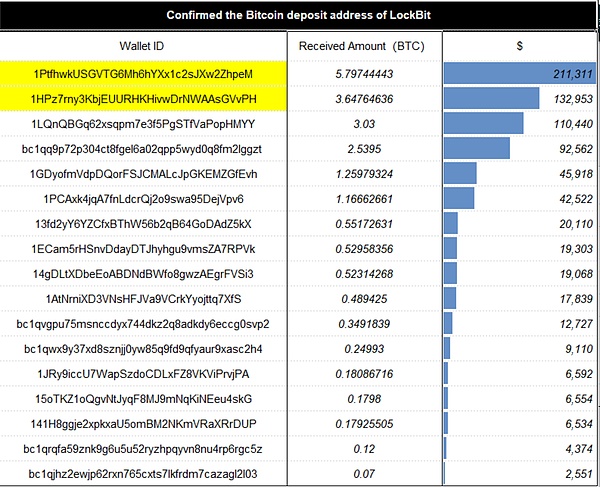
Picture: Part of LockBit’s payment address and payment amount
Use the two addresses with the highest amount of money involved to conduct on-chain address tracking and anti-money laundering analysis:
Blackmail payment address 1: 1PtfhwkUSGVTG6Mh6hYXx1c2sJXw2ZhpeM;
Blackmail collection address 2: 1HPz7rny3KbjEUURHKHivwDrNWAAsGVvPH.
(1) Blackmail collection address 1: 1PtfhwkUSGVTG6Mh6hYXx1c2sJXw2ZhpeM
According to the analysis in the figure below, the address 1 (1Ptfhw) received a total of 17 on-chain transactions from March 25, 2021 to May 15, 2021. After receiving the funds, it quickly transferred the assets to 13 core intermediate addresses. These intermediate addresses are transferred layer by layer to 6 second-layer intermediate addresses, namely: 3FVzPX…cUvH, 1GVKmU…Bbs1, bc1qdse…ylky, 1GUcCi…vSGb, bc1qan…0ac4 and 13CPvF…Lpdp.
The intermediate address 3FVzPX…cUvH, through on-chain analysis, was found to eventually flow to the darknet address 361AkMKNNWYwZRsCE8pPNmoh5aQf4V7g4p.
The intermediate address 13CPvF...Lpdp transferred a small amount of 0.00022 BTC to CoinPayments. There were 500 similar transactions, and a total of 0.21 BTC were collected to the CoinPayments address: bc1q3y…7y88, using CoinPayments for money laundering.
Other intermediate addresses eventually flowed into centralized exchanges Binance and Bitfinex.
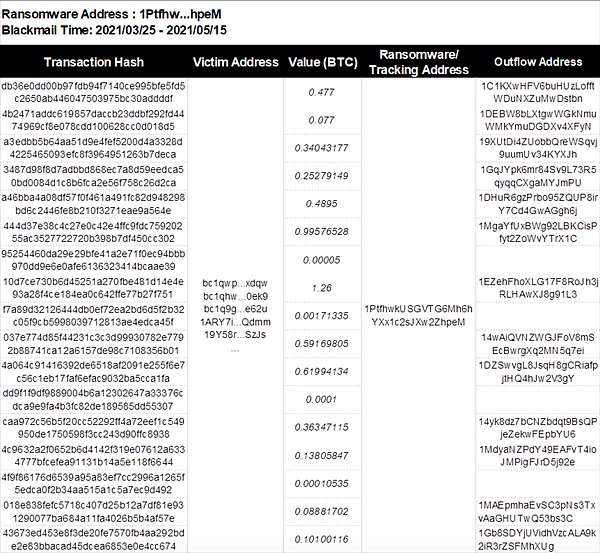
Picture: Address 1 (1Ptfhw...hpeM) fund source and fund outflow details
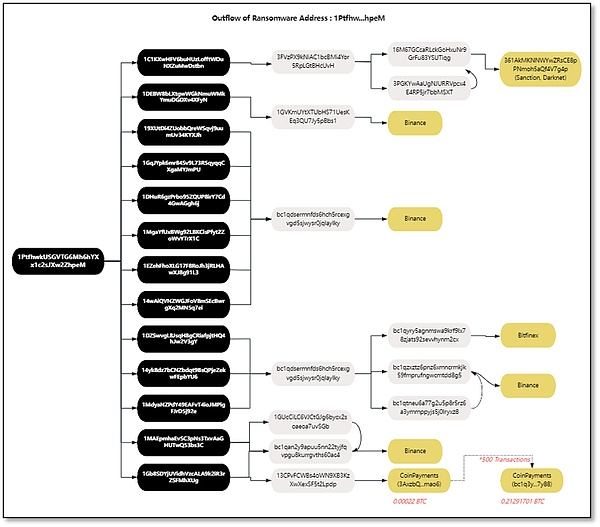
Figure: Address 1 (1Ptfhw...hpeM) fund flow tracking
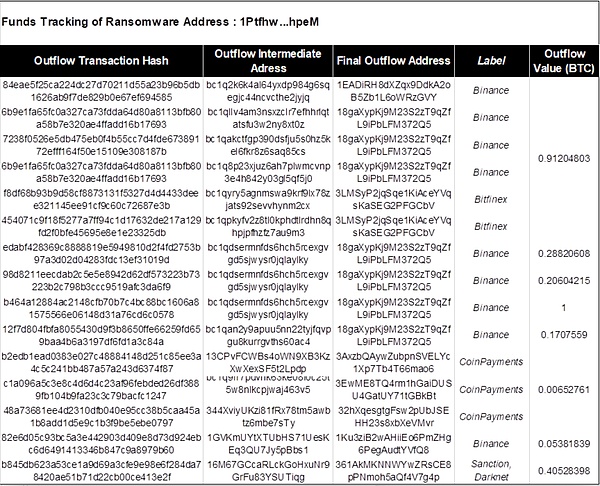
Figure: Intermediate addresses and fund flow details involved in address 1 (1Ptfhw...hpeM)
Figure: Address 1 (1Ptfhw...hpeM) transaction map
(2) Blackmail collection address 2: 1HPz7rny3KbjEUURHKHivwDrNWAAsGVvPH
The victim paid 4.16 BTC to the ransomware operator LockBit through 11 transactions between May 24, 2021, and May 28, 2021. Immediately, address 2 (1HPz7rn...VvPH) quickly transferred the extortion funds 1.89 BTC to the intermediate address 1: bc1qan...0ac4, 1.84 BTC to the intermediate address 2: 112QJQj...Sdha, and 0.34 BTC to the intermediate address 3: 19Uxbt... 9RdF.
Final intermediate address 2: 112QJQj…Sdha and intermediate address 3: 19Uxbt…9RdF both transfer funds to intermediate address 1: bc1qan…0ac4. Immediately afterwards, the intermediate address 1 bc1qan...0ac4 continued to transfer funds. A small part of the funds was transferred directly to the Binance exchange. The other part of the funds was transferred through the intermediate addresses layer by layer, and finally transferred to Binance and other platforms for money laundering. The specific transaction details and The address labels are as follows.
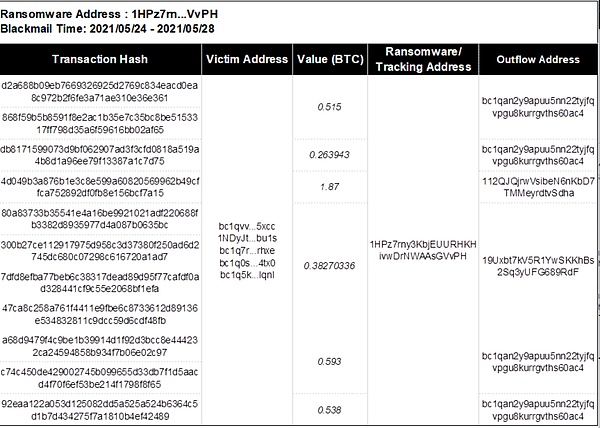
Picture: Address 2 (1HPz7rn...VvPH) fund source and fund outflow details
< p style="text-align:center;">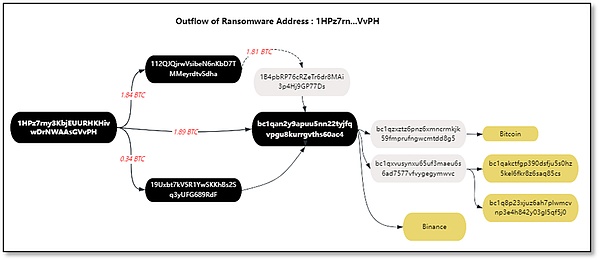
Picture: Address 2 (1HPz7rn...VvPH) fund flow tracking
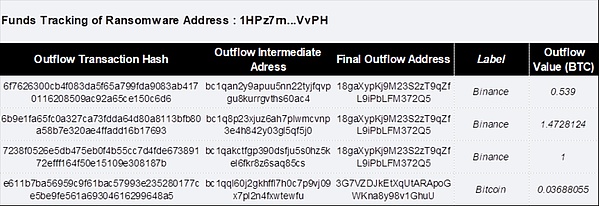
Figure: Intermediate addresses and fund flow details involved in address 2 (1HPz7rn...VvPH)
LockBit will conduct cryptocurrency laundering after receiving the ransom. This money laundering model is different from traditional money laundering methods. It usually occurs on the blockchain and has the characteristics of long cycle, dispersed funds, high degree of automation and high complexity. To carry out cryptocurrency supervision and fund tracking, on the one hand, we must build on-chain and off-chain analysis and evidence collection capabilities, and on the other hand, we must launch APT-level security attack and defense at the network security level, and have the ability to integrate attack and defense.
Money laundering is a method of legalizing illegal income The behavior of illegal income mainly refers to using various means to cover up and conceal the source and nature of illegal income and the income generated, so as to make it legal in form. Its actions include but are not limited to providing capital accounts, assisting in converting property forms, assisting in transferring funds or remitting them overseas. Cryptocurrencies—especially stablecoins—have been exploited by money laundering activities quite early on due to their low transfer costs, de-geographicalization, and certain anti-censorship characteristics. This has also led to cryptocurrencies being criticized. One of the main reasons.
Traditional money laundering activities often use the cryptocurrency OTC market to exchange from legal currency to cryptocurrency, or from cryptocurrency to legal currency. Among them, money laundering scenarios They are different and have diverse forms, but no matter what, the essence of this type of behavior is to block law enforcement officials from investigating the financial links, including accounts of traditional financial institutions or accounts of cryptographic institutions.
Different from traditional money laundering activities, the laundering target of new cryptocurrency money laundering activities is the cryptocurrency itself, including wallets, cross-chain bridges, and decentralized transactions. Crypto industry infrastructure, including platforms, will be illegally exploited.
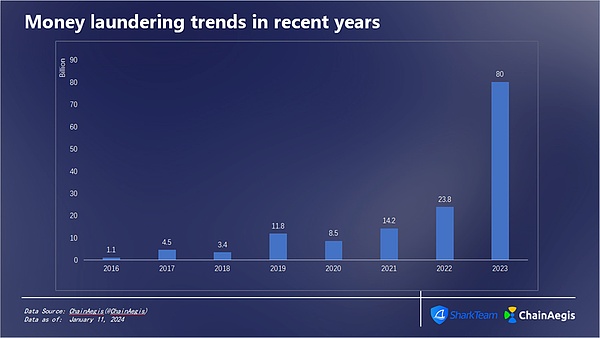
Picture: Amount of money laundering in recent years
From 2016 to 2023, cryptocurrency money laundering totaled $147.7 billion. The amount of money laundered has been increasing at an annual rate of 67% since 2020, reaching US$23.8 billion in 2022, and reaching US$80 billion in 2023. The amount of money laundered is staggering, and cryptocurrency anti-money laundering operations are imperative.
According to ChainAegis platform statistics, the amount of funds in the on-chain currency mixing platform Tornado Cash has maintained rapid growth since January 2020, and currently has nearly 3.62 million ETH is deposited in this capital pool, with a total deposit amounting to US$7.8 billion. Tornado Cash has become the largest money laundering center in Ethereum. However, as U.S. law enforcement agencies issued sanctions against Tornado Cash in August 2022, the number of weekly deposits and withdrawals of Tornado Cash doubled. However, due to the decentralized nature of Tornado Cash, it was impossible to stop it from the source, and funds still continued to flow in. Enter the system to mix coins.
National APT (Advanced Persistent Threat (Advanced Persistent Threat) organization is a top hacker group with state-backed support that specializes in long-term and persistent cyber attacks against specific targets. The North Korean APT organization Lazarus Group is a very active APT group. Its attack purpose is mainly to steal funds, making it the biggest threat to global financial institutions. In recent years, they have been responsible for many attacks and fund theft cases in the cryptocurrency field.
The security incidents and losses caused by Lazarus attacks in the encryption field that have been clearly counted are as follows:
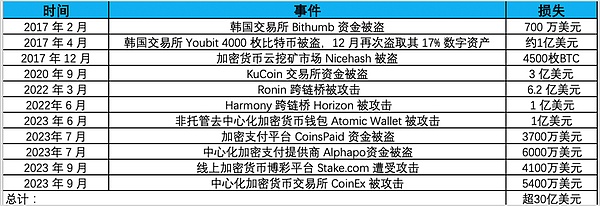
More than US$3 billion The funds were stolen by Lazarus in a cyber attack. It is reported that the Lazarus hacker organization is backed by North Korea's strategic interests and provides funds for North Korea's nuclear bomb and ballistic missile programs. To this end, the United States announced a $5 million reward and sanctions against the Lazarus hacking organization. The U.S. Department of the Treasury has also added relevant addresses to the OFAC Specially Designated Nationals (SDN) list, prohibiting U.S. individuals, entities and related addresses from conducting transactions to ensure that state-sponsored groups cannot cash out these funds as a sanction. Ethereum developer Virgil Griffith was sentenced to five years and three months in prison for helping North Korea use virtual currency to evade sanctions. In 2023, OFAC also sanctioned three individuals related to the Lazarus Group, two of whom were sanctioned Cheng Hung Man and Wu Huihui was the over-the-counter (OTC) trader who facilitated cryptocurrency trading for Lazarus, while a third person, Sim Hyon Sop, provided other financial support.
Despite this, Lazarus has completed the transfer and laundering of assets of more than US$1 billion. Their money laundering model is analyzed below. Taking the Atomic Wallet incident as an example, after removing the technical interference factors set up by hackers (a large number of fake token transfer transactions + multi-address splitting), the hacker’s fund transfer model can be obtained:
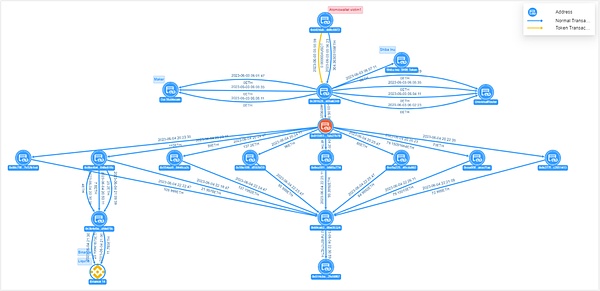
Picture: Atomic Wallet Victim 1 fund transfer view
Victim 1 address 0xb02d... c6072 transferred 304.36 ETH to the hacker address 0x3916...6340. After 8 splits through the intermediate address 0x0159...7b70, it was collected to the address 0x69ca...5324. Afterwards, the collected funds were transferred to the address 0x514c...58f67. The funds are still in this address, and the address ETH balance is 692.74 ETH (valued at US$1.27 million).
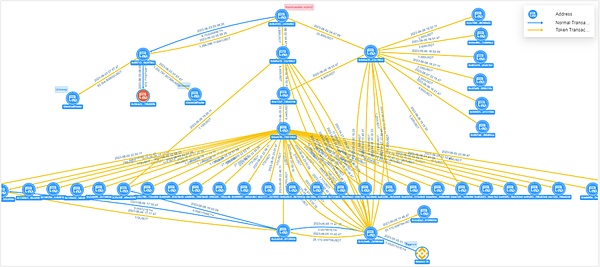
Picture: Atomic Wallet victim 2 fund transfer view
Victim 2 address 0x0b45...d662 transferred 1.266 million USDT to the hacker address 0xf0f7...79b3. The hacker divided it into three transactions, two of which were transferred to Uniswap, with a total transfer of 1.266 million USDT; the other The pen is transferred to the address 0x49ce...80fb, and the transfer amount is 672.71ETH. Victim 2 transferred 22,000 USDT to the hacker address 0x0d5a...08c2. The hacker split accounts multiple times through the intermediate address 0xec13...02d6, etc., and directly or indirectly collected the funds to the address 0x3c2e...94a8.
This money laundering model is highly consistent with the money laundering model in the previous Ronin Network and Harmony attacks, both including three steps:
(1) Stolen funds sorting and exchange: After launching the attack, sort out the original stolen tokens, and swap multiple tokens into ETH through dex and other methods. This is a common way to avoid fund freezes.
(2) Collection of stolen funds: Gather the organized ETH into several disposable wallet addresses. Hackers used a total of 9 such addresses in the Ronin incident, 14 in Harmony, and nearly 30 addresses in the Atomic Wallet incident.
(3) Transferring stolen funds: Use the collection address to launder the money through Tornado.Cash. This completes the entire fund transfer process.
In addition to having the same money laundering steps, there is also a high degree of consistency in the details of money laundering:
(1) The attackers were very patient and took up to a week to conduct money laundering operations. They all started subsequent money laundering operations a few days after the incident.
(2) Automated transactions are used in the money laundering process. Most of the fund collection actions involve a large number of transactions, a small time interval, and a unified pattern.
Through analysis, we believe that Lazarus’ money laundering model is usually as follows:
(1) Many Separate accounts and transfer assets in multiple small amounts make tracking more difficult.
(2) Begin to create a large number of counterfeit currency transactions, making it more difficult to track. Taking the Atomic Wallet incident as an example, 23 of the 27 intermediate addresses were counterfeit currency transfer addresses. A recent analysis of the Stake.com incident also found that similar technology was used, but this was not the case in the previous Ronin Network and Harmony incidents. Interference technology shows that Lazarus’ money laundering technology is also upgrading.
(3) More on-chain methods (such as Tonado Cash) are used to mix coins. In early incidents, Lazarus often used centralized exchanges to obtain start-up funds. Or carry out subsequent OTC, but recently fewer and fewer centralized exchanges are used, and it can even be considered that they are trying to avoid using centralized exchanges. This should be related to several recent sanctions.
U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC), etc. agency, and similar agencies in other countries, by imposing sanctions against countries, regimes, individuals and entities deemed to pose a threat to national security and foreign policy. Sanctions enforcement has traditionally relied on the cooperation of mainstream financial institutions, but some bad actors have turned to cryptocurrencies to circumvent these third-party intermediaries, creating new challenges for policymakers and sanctioning agencies. However, the inherent transparency of cryptocurrencies, as well as the willingness of compliant cryptocurrency services, especially the many centralized exchanges that serve as a link between cryptocurrencies and fiat currencies, have proven that imposing sanctions is possible in the cryptocurrency world.
The following is the situation of some individuals or entities related to cryptocurrency that are subject to sanctions in the United States in 2023, and the reasons for OFAC sanctions.
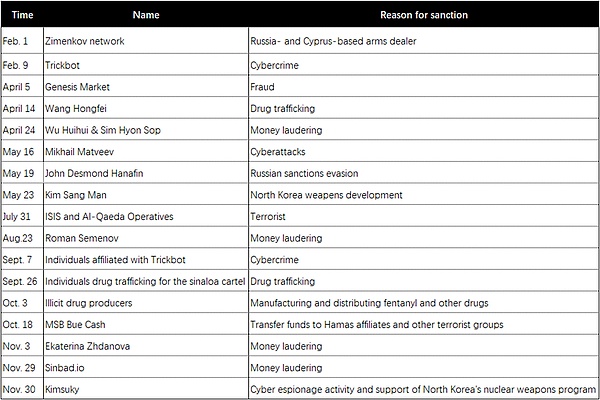
Tether, the company behind the world's largest stablecoin, announced on December 9, 2023 that it would "freeze" the wallets of sanctioned individuals on the U.S. Office of Foreign Assets Control (OFAC) sanctioned individuals list. of tokens. In its announcement, Tether viewed the move as a voluntary step to "proactively prevent any potential misuse of Tether tokens and enhance security measures."
This also shows that the investigation and sanctions of cryptocurrency crimes have entered a substantial stage. Cooperation between core enterprises and law enforcement agencies can form effective sanctions, supervision and punishment. Cryptocurrency Crime.
Hong Kong has also made great progress in the regulation of Web3 in 2023, and is sounding the clarion call for "compliant development" of Web3 and the encryption market. When the Monetary Authority of Singapore begins to restrict retail customers from using leverage or credit for cryptocurrency trading in 2022, and the Hong Kong SAR government publishes the "Policy Declaration on the Development of Virtual Assets in Hong Kong", some Web3 talents and companies are heading to the new promised land. land.
On June 1, 2023, Hong Kong fulfilled the Declaration and issued the "Guidelines Applicable to Virtual Asset Trading Platform Operators", and the virtual asset trading platform license system was officially implemented. , and has issued Category 1 (securities trading) and Category 7 (providing automated trading services) licenses.
At present, OKX, BGE, HKbitEX, HKVAX, VDX, Meex, PantherTrade, VAEX, Accumulus, DFX Labs and other institutions are actively applying for virtual asset trading platform licenses ( VASP).
Chief Executive Li Ka-chiu, Financial Secretary Paul Chan and others have frequently spoken out on behalf of the Hong Kong government to support the implementation of Web3 in Hong Kong and attract encryption companies and talents from all over the world to build it. In terms of policy support, Hong Kong has introduced a licensing system for virtual asset service providers, allowing retail investors to trade cryptocurrencies, launched the Web3 Hub Ecological Fund with a scale of tens of millions of dollars, and plans to invest more than HK$700 million to accelerate the development of the digital economy and promote the development of the virtual asset industry. A Web3.0 development task force has also been established.
However, while making rapid progress, risky events are also coming. The unlicensed crypto exchange JPEX was involved in a case involving more than 1 billion Hong Kong dollars, the HOUNAX fraud case involved an amount of over 100 million yuan, and HongKongDAO and BitCuped were suspected of virtual asset fraud... These vicious incidents have attracted great attention from the Hong Kong Securities Regulatory Commission and the police. The Securities and Futures Commission of Hong Kong stated that it will formulate risk assessment criteria for virtual asset cases with the police and conduct information exchanges on a weekly basis.
I believe that in the near future, a more complete supervision and security system will help Hong Kong. As an important financial hub between the East and the West, Hong Kong is opening its arms to Web3.
Bitcoin becomes digital gold only out of necessity? AVM under the Atomicals protocol may "restart" the Bitcoin programming era
 JinseFinance
JinseFinanceSolana’s largest liquidity staking provider has taken a meaningful step toward re-staking.
 JinseFinance
JinseFinanceWhere did the funds go? Why don’t exchanges like your B? Arrogance is not unsolvable. We can find a way out by learning from past experience.
 JinseFinance
JinseFinanceI have conducted comprehensive thinking from the perspective of the flow of the entire capital market, as well as exchanges and VC business models.
 JinseFinance
JinseFinanceThe first episode of Behind the Code Season 2, "Creating the Future of Web3", is now online. The first episode takes a deep dive into the huge potential of Polkadot and Web3 technology in solving digital identity, data ownership, and decentralized governance.
 JinseFinance
JinseFinanceLegally speaking, Alexey Pertsev’s case is more important to the future of DeFi than the simple fraud cases against SBF and Do Kwon or Changpeng Zhao’s failure to put in place the required anti-money laundering protocols.
 JinseFinance
JinseFinanceThe white hat hackers were rewarded for safeguarding over $25 billion in crypto assets.
 cryptopotato
cryptopotatoDoes the OFAC not know that code is speech? Yesterday, we covered the EFF’s demands for clarity around the Tornado ...
 Bitcoinist
Bitcoinist Nulltx
NulltxForbes named 15 of its latest 30 business leaders under 30, including OpenSea co-founder Alex Atallah and Alamada Research co-CEOs Caroline Ellison and Sam Trabucco.
 Cointelegraph
Cointelegraph