Written by: Jinse Finance xiaozou
On April 15, 2024, Vitalik transferred 100 ETH to the privacy protocol RAILGUN. The next day, Vitalik tweeted again to like RAILGUN, saying that privacy is normal and Railgun uses a privacy pool protocol, which makes it more difficult for bad actors to join the pool without compromising user privacy.
What exactly attracted Vitalik to RAILGUN? This article will help you understand RAILGUN with 6 questions.
1, What is RAILGUN?
RAILGUN is a privacy system built directly on Ethereum, BSC, Polygon, and Arbitrum chains. It uses zero-knowledge (ZK) cryptography to enable privacy for smart contracts and DeFi without sacrificing the security of the user's preferred chain.
RAILGUN refers only to a set of smart contracts that support backend privacy infrastructure. Wallet providers can choose to integrate the RAILGUN protocol.
Since RAILGUN is just on-chain smart contract logic, privacy is achieved without the need for a separate L2 validator set or vulnerable bridges, which has two main advantages:
Security and decentralization - fewer validator set issues, no bridging risk. RAILGUN is as secure as the EVM chain it is deployed on.
Full ecosystem - RAILGUN users have access to all economic activity on Ethereum and benefit from the rich history of existing dApps and builders, rather than an isolated ecosystem on a standalone privacy chain.
The user experience is similar to using a public wallet like MetaMask to interact with the Ethereum/EVM chain for liquidity and DeFi, except with the added ability to transact privately.
RAILGUN consists of two main components:
RAILGUN integrated wallet - an EVM wallet built by independent community developers, through which users can use the RAIGLUN protocol.
Developer tools - TypeScript SDKs for building RAILGUN privacy into existing or new wallets, or dApps with privacy protection features.
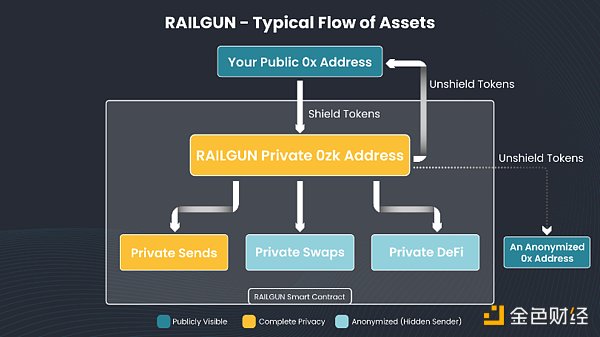
2、What are the advantages and use cases of RAILGUN?
Complex DeFi transactions help make RAILGUN more private than other protocols with similar anonymity. All transfers, exchanges, loans, and dApp calls increase the interaction changes in RAILGUN.
RAILGUN achieves better privacy protection with less liquidity and shorter time frames than other privacy systems. The dApp interactions in the RAILGUN privacy system also incentivize users to hold assets in RAILGUN longer because there is no reason to transfer funds out of RAILGUN.
Potential use cases are:
Privacy: Wallet dynamics are not known, account balances are private, trading strategies are protected, trading habits are not monitored, and data collection is prevented
Alpha security: Traders who want to keep their alpha confidential can trade freely and maintain their hard-earned information advantage.
Privacy payroll: Provide payroll services for companies that pay salaries in cryptocurrency. If the current state of the public blockchain is used, the payroll will show the exact salary of each employee.
Censorship resistance: Support citizens living in countries with unfriendly or corrupt government officials to make censorship-resistant donations.
Anonymous analysis: In contrast to services such as Nansen or Etherscan, well-known wallets are marked or recognized in the services of Nansen or Etherscan, which means that the personal identities of some large investors are identifiable.
Compliance: Financial companies are still subject to data protection laws, such as GDPR
RAILGUN is a disruptive toolkit and objectively the most uncompromising and complete privacy solution for DeFi. Privacy DeFi will provide the cryptocurrency industry with new business possibilities that are not possible on public blockchains. All other privacy solutions have some trade-offs, such as requiring users to trust custodial bridges or trade with fragmented (or non-existent) liquidity.
3 How is RAILGUN different from other privacy-preserving protocols?
Other security solutions usually require dedicated infrastructure to run and are called L2 solutions. L2 solutions do not have direct access to DeFi protocols and rely on bridging technology that has many security vulnerabilities. Since L2 solutions use their own nodes, they do not have the full security or liquidity of the main blockchain.
Other solutions, such as mixers, lack functionality and ease of use. For example, mixers usually do not support internal shielded transactions or interaction with smart contracts. They may also require users to send and receive fixed amounts, such as 1 or 10 ETH. Mixers cannot simply and efficiently use the protocol while preserving privacy. They also do not allow users to keep their balances private in their wallets. However, RAILGUN makes users' privacy secure and maintained even when no transactions are taking place.
Previous generation privacy protocols cannot compare to the convenience, flexibility, and privacy that RAILGUN ensures.
4Which tokens does RAILGUN support?
RAILGUN is permissionless. By default, all standard ERC-20 tokens can be used in the RAILGUN privacy system.
Some ERC-20 tokens are non-standard, such as rebasing tokens and lottery tokens. These tokens are currently incompatible with the RAILGUN privacy system and should not be stored.
Although it is not fully compliant with the ERC-20 standard, Tether (USDT) can be used in the RAILGUN privacy system.
5 How easy is RAILGUN to use?
RAILGUN is very easy to use through front-ends such as web apps. The technology can also be easily integrated into existing protocols.
Although the code is very complex, it is easy to use the RAILGUN privacy system. Wallet apps that contain RAILGUN smart contracts (such as RAILWAY) have very intuitive user interfaces.
6 How is the balance privacy achieved? What is the cryptographic principle?
The RAILGUN wallet consists of two keys: the spending key and the viewing key. The RAILGUN wallet address (also known as the 0zk address) is two corresponding public keys - the spending public key and the viewing public key.
Therefore, if user A (Alice) knows the RAILGUN address of user B (Bob), she can initiate a transaction.
Alice does this by creating a note containing what is called a commitment in cryptography. The commitment contains information about the tokens and how much of them to transfer. These commitment values are encrypted using information from Bob's public key.
Next, Alice creates a zk-SNARK proof that shows that she didn't spend more than she had on deposit. This also shows that she didn't double-spend - she also spent the tokens somewhere else.
Finally, Alice sends the proof, commitment, and ciphertext to the RAILGUN smart contract. The smart contract verifies the proof, accumulates the commitments, and emits the ciphertext as an event. This means it's up to it to check that everything is correct and enables Bob to interact with the transaction.
Only Bob can decrypt the ciphertext using his view key to get the private information. With this information and his spend key, Bob can spend the note - which means he can transfer or withdraw the tokens.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Max Ng
Max Ng Brian
Brian JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Cointelegraph
Cointelegraph