Author: Maika Isogawa Source: bankless Translation: Shan Oba, Golden Finance
The rise may have paused, but the bull market is still there It's far from over. As price fluctuations fuel activity, so does the potential for mistakes in all the craziness.
Don’t worry! Security tools have improved significantly since the last cycle, and the industry's understanding of attack vectors and vulnerabilities has improved.
Here are things you need to pay attention to to improve security.
Wallet Hygiene
Wallet hygiene is crucial to protecting your on-chain assets… but what is it?
Usually, wallet hygiene means developing good habits and using different wallets for different purposes. Your high-value NFTs and large token holdings should be kept in more secure wallets than the ones you use to trade spam coins.
However, there are situations where you will be tempted to put your high-value assets at risk, for example, when you need to verify ownership of an asset to join a community, or to take advantage of a large Wallet features to obtain airdrop rewards.
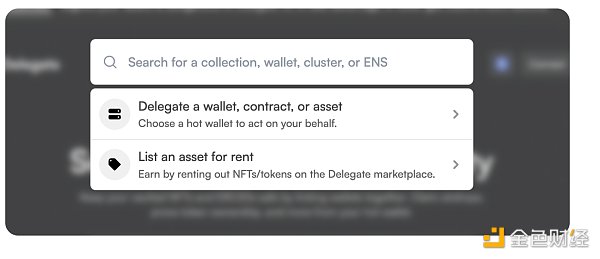
delegate.cash ( delegate.xyz) is a popular choice for delegation. Delegation is the process of extending the permissions of one wallet to another, ultimately leaving your assets in a more secure state.
In addition to delegation, regularly cleaning and checking your cold wallets, hot wallets, browser wallets, and hardware wallets are all part of solid crypto hygiene.
Monitoring
How do you know what is happening in your wallet?
As users, when we actively trade, exchange and send, we will be aware of the changes happening in the wallet, but you may be surprised to find that there are a lot of things happening on the chain that we are not aware of .
Some activity may be benign, such as spam NFTs being sent to your address, but there are also occasional cases of unknown activity that are concerning. Regularly monitoring the status of your wallet is an important part of keeping your assets safe in the long term. Companies like Webacy (Hi I'm the CEO!) make monitoring easy by sending text messages or emails in real time as activity occurs in and around your wallet.
Pre-trade research
We’ve all been there. You see everyone making money on a coin that goes up 1000% overnight and you want to be a part of it. You see a link and click on it. Your browser wallet pops up and prompts you to connect, and then...this is where many errors occur.
In the midst of the excitement, it can be difficult to pause to evaluate the security of the deal you're about to sign. Often, the transactions themselves are difficult to explain and may even be malicious.
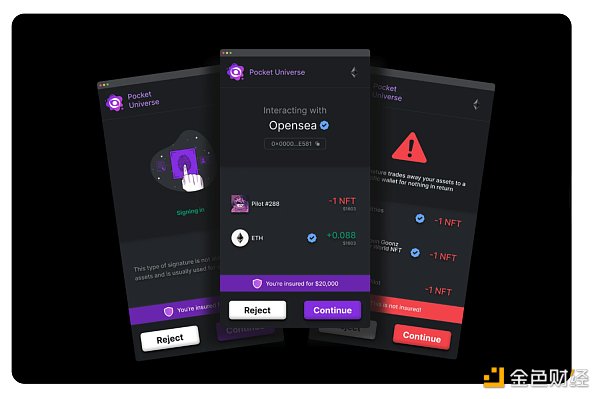
Browser extension tool Can help users evaluate transactions before they occur, including Pocket Universe, Fire and Wallet Guard.
In recent years, wallets themselves have also taken on more user security responsibilities by integrating additional security features. Phantom Wallet has an excellent user interface that displays changes in wallet status after transactions, allowing users to easily make informed decisions. Other wallets are trying their own security enhancements, with mixed reviews.
If possible, you need to evaluate the team behind the project, the contract itself, and the project's historical success rate before jumping in blindly.
Approval Review
When you transact on-chain, you typically need to grant other addresses permission to spend your tokens and NFTs. These permissions are called "approvals." These permissions are often necessary, but sometimes they can be overreaching or even malicious.
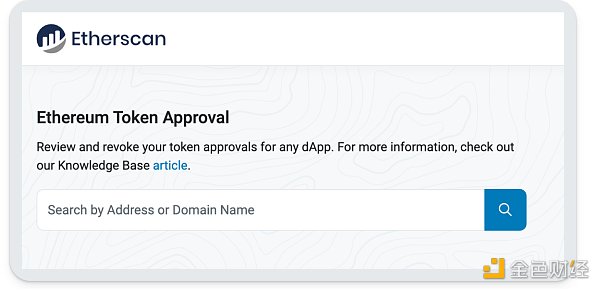
If you have already used If your wallet is old for a while, or is just very active, you should check your open permissions regularly. While tools like revoke.cash or etherscan’s token approval service are great, they don’t provide users with information about which approvals are good or bad. Our revocation feature provides both native revocation functionality and the ability to evaluate which open approvals are potentially dangerous to your wallet.
Traditional Cyber Security
We must not forget that traditional cyber security (OpSec) is critical to the overall security of crypto assets. After all, everything uses the Internet.
The common culprits highlighted here are the reasons why many users fall victim to hackers and scams. Take the time to check your systems – don’t be the next person to trend on Twitter.
SMS 2FA is no longer reliable. Sim swapping has become a major topic in the crypto-security world and a playbook that hackers follow. Remove your phone number from the two-factor authentication option on all accounts that support other methods.
Password managers and cloud storage providers are not safe havens for your login information or seed phrases. Through a hack or a data breach of the company itself, this information could be exposed, putting you at risk.
Set bookmarks for your most visited crypto websites to avoid phishing link scams.
Close your Discord private messages.
There’s a lot more to be aware of, but following just these few steps will ensure you’re less of an easy target.
Use projects that care about user security
The last thing to note is to choose companies and projects that care about user security. Now that mature solutions are available, such as embedded security APIs, there is no reason for projects not to provide additional protection measures for their end users.
Self-hosting means users need to take more responsibility for protecting themselves, but self-security is only part of the equation. Project owners also have a responsibility to utilize newly developed risk mitigation tools to protect end users and ultimately the health of the company.
Companies like Mintify are actively taking steps to integrate security measures directly into their platforms - a clear indication that they care about the security of their end users.
Distributed security means a more secure Web3
Decentralization - a buzzword in the blockchain world and one of the cornerstones of what makes cryptocurrencies so great. It must also be applied to safety and security. If data and ownership are no longer controlled by a central entity within a walled garden, then neither is the security and ownership of that data.
As control shifts to users and the companies building networks for them, risk mitigation and security will become a category that improves together to address emerging challenges and use cases.
 JinseFinance
JinseFinance





