Source: Chainalysis; Compiler: Deng Tong, Golden Finance
The purpose of money laundering is to conceal the criminal origin of funds so that the funds can be obtained and used. In cryptocurrency-based crime, this often means moving funds to a service that can be converted into cash, while often taking additional steps to hide the source of the funds. Therefore, our on-chain analysis of cryptocurrency money laundering focuses on two distinct sets of services and on-chain entities:
Intermediary services and wallets. This category includes personal wallets, mixers, instant exchangers, various types of DeFi protocols, and other legal and illegal services. Cryptocurrency criminals often use such services to hold funds or obfuscate their criminal origins by masking the on-chain link between their source address and current address.
Fiat off-ramping service. This category includes any service that converts cryptocurrencies into fiat currencies, most commonly centralized exchanges. But it can also include P2P exchanges, gambling services and cryptocurrency ATMs. It is also important to consider nested services that use centralized exchange infrastructure and allow fiat currencies to be offshored, such as many over-the-counter trading platforms.
It is important to remember that all of these services have different features and options when it comes to solving money laundering problems. For example, centralized exchanges have more control because they can freeze funds from questionable or illegal sources. However, DeFi protocols typically do not have this option as they operate autonomously and do not have custody of user funds. Of course, the decentralized nature of DeFi protocols also means that blockchain analysts can often track the flow of funds through DeFi protocols to their next stop, whereas this is not the case with centralized services. Of course, illegal services that knowingly facilitate money laundering can usually only be stopped through law enforcement actions or other legal proceedings. It is also important to remember that token issuers also have an active role to play. For example, stablecoins such as USDT and USDC have the ability to freeze assets held by addresses associated with crimes.
With this in mind, let’s take a look at the key trends in cryptocurrency money laundering in 2023.
Cryptocurrency Money Laundering in 2023: Key Trends
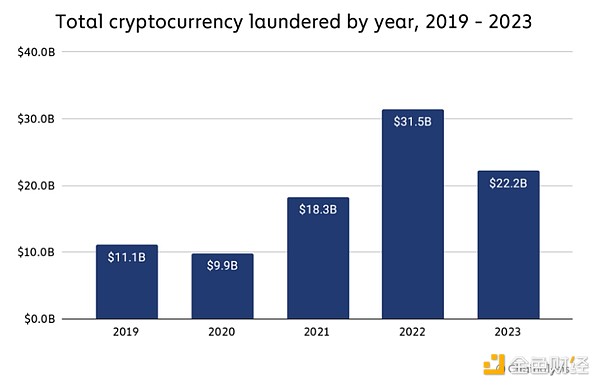
In 2023, illegal addresses sent Cryptocurrency worth $22.2 billion, which is a significant decrease from the $31.5 billion sent in 2022. Part of this decline may be due to an overall decline in legal and illegal cryptocurrency trading volumes. However, money laundering activity fell more sharply, at 29.5%, compared to a 14.9% decline in total transaction volume.
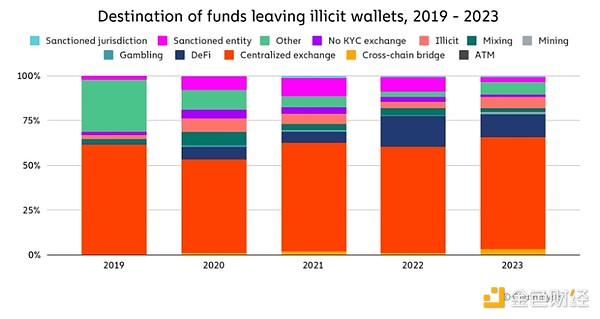
Overall, Centralized exchanges remain the primary destination for funds sent from illicit addresses, with rates increasing over the past five years. Remained relatively stable through the middle of the year. Over time, the role of illicit services has shrunk, while the share of illicit funds flowing to DeFi protocols has increased. We attribute this primarily to the overall growth of DeFi during that period, but it’s also important to note that DeFi’s inherent transparency often makes it a poor choice for obfuscating fund flows.
2023 will be broadly similar to 2022 in terms of Breakdown of types of services used for money laundering >, but we did see a slight decrease in the proportion of illicit funds going to illegal service types and an increase in funds going to gambling services and bridge protocols.
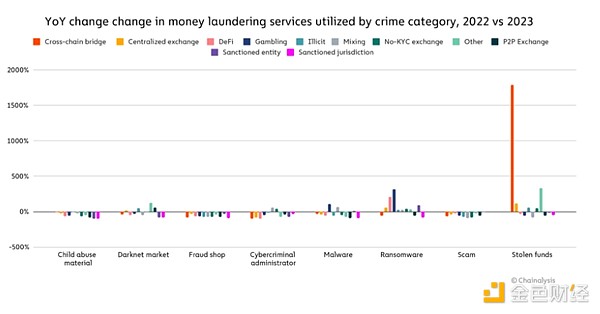
However, if we Zooming in to look at how specific types of crypto criminals launder money, we can see that some areas are actually seeing significant changes. Most notably, we saw a significant increase in the amount of funds being sent to cross-chain bridges from addresses associated with stolen funds, we will look at this trend in more detail later. We also observed a significant increase in funds sent from ransomware to gambling platforms and funds sent from ransomware wallets to bridges.
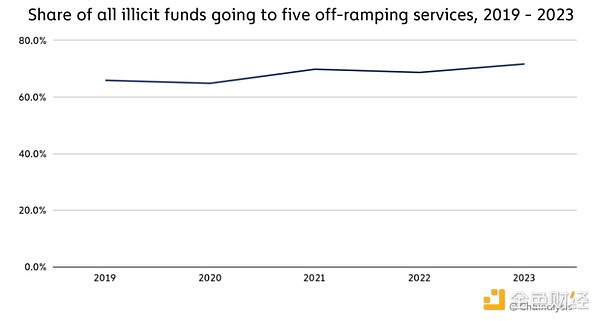
Money laundering focuses on fiat export services
Fiat export services are important because they are where criminals can convert cryptocurrencies into cash, which is the culmination of the money laundering process. Although there are thousands of export services operating, most money laundering activity is concentrated in a few services. In 2023, 71.7% of all illicit funds flowing to exported services went to just 5 services, up slightly from 68.7% in 2022.
We can also add more An in-depth examination of money laundering concentrations at the deposit address level. Deposit addresses are centralized service addresses associated with individual users - you can think of them similar to bank accounts. Therefore, examining money laundering activity in terms of deposit addresses can give us a better understanding of the individuals or nested services that are most directly responsible for most cryptocurrency money laundering activity. From this perspective, we can see that Money laundering in 2023 will actually be less concentrated at the deposit address level, although money laundering will be more concentrated in services Level concentration has increased slightly.
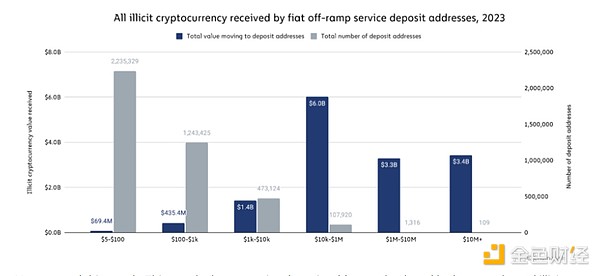
The chart above shows service deposit addresses broken down by the total amount of illegal cryptocurrency received by each address individually in 2023. Each gray bar represents the number of deposit addresses in the bucket, while each blue bar represents the total value of illegal cryptocurrency received by all deposit addresses in the bucket. Taking the first bucket as an example, we see that 2,235,329 deposit addresses received between $5 and $100 worth of illicit cryptocurrency, for a total of $69.4 million worth of illicit cryptocurrency across all of these deposit addresses.
In 2023, 109 exchange deposit addresses received over $10 million worth of illicit cryptocurrency each, for a total of $3.4 billion in illicit cryptocurrency. While this still represents a high level of concentration, only 40 addresses received more than $10 million in illicit cryptocurrency in 2022, for a total of just under $2 billion. In 2022, just 542 deposit addresses received more than $1 million in illicit cryptocurrency, for a total of $6.3 billion, accounting for more than half of all illicit value received by centralized exchanges that year. In 2023, 1,425 deposit addresses received more than $1 million in illicit cryptocurrency, totaling $6.7 billion, accounting for just 46% of all illicit value received from transactions that year.
However, it is also worth noting that Money laundering concentrations vary by crime type. For example, the concentration of CSAM vendors and ransomware operators is very high. Only 7 recharge addresses accounted for 51.0% of the total value obtained by the exchange from CSAM vendors. For ransomware , only 9 addresses accounted for 50.3%. On the other hand, scams and darknet markets are much less concentrated. Forms of cryptocurrency crime that display higher levels of concentration may be more vulnerable to law enforcement because their money laundering operations rely on relatively few interruptible services.
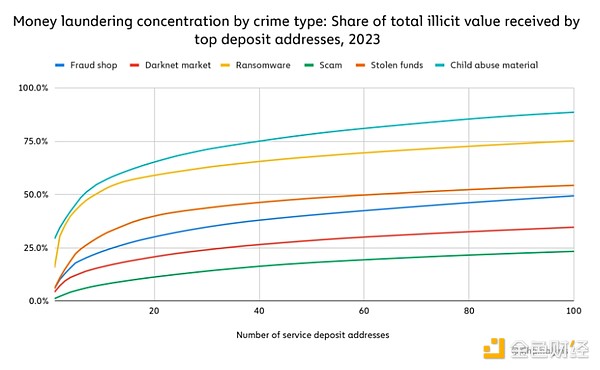
Overall, crypto criminals may be diversifying their money laundering operations with more nested services or deposit addresses to better conceal their whereabouts from law enforcement and exchange compliance teams. Spreading activity across more addresses may also be a strategy to mitigate the impact of any one deposit address being frozen due to suspicious activity. Therefore, combating cryptocurrency crime by targeting money laundering infrastructure may require greater diligence and understanding of the interconnectedness of on-chain activity than in the past, as activity is more dispersed.
Money laundering tactics change: The most sophisticated cryptocurrency criminals exploit bridges and mixers
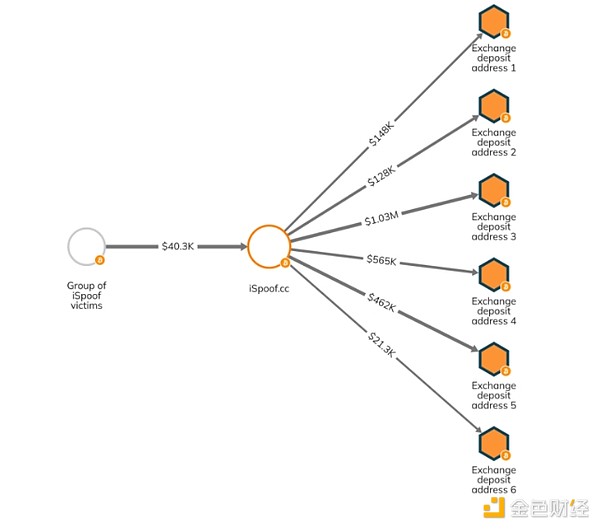
Big Some cryptocurrency money laundering operations are relatively simple, with bad actors sending funds directly to exchanges. We can see this in the Chainalysis Reactor graph below, which shows the now-defunct phone number spoofing service iSpoof, which facilitated over £100m in fraud before being shut down by law enforcement, leaving numbers Millions of Bitcoins are sent directly to deposit addresses on a set of centralized exchanges.
However, there are more Cryptocriminals with sophisticated on-chain money laundering skills—such as the notorious North Korean cybercriminals associated with hacking gangs such as the Lazarus Group—tend to use a wider variety of cryptographic services and protocols. Below, we'll use the example of the Lazarus Group to understand two important ways sophisticated bad actors adapt their money laundering strategies:
Let’s take a look.
New mixer: YoMix succeeds Sinbad
Overall, Funds sent to mixers from illicit addresses declined in 2023, from $1 billion in 2022 to $504.3 million in 2023.
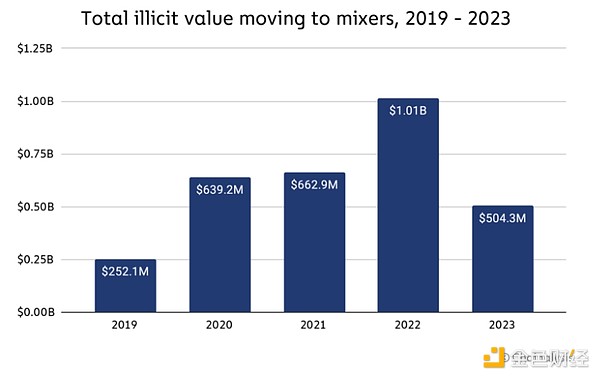
This is likely due in large part to enforcement and regulatory efforts, such as the sanctions and closure of mixer Sinbad in November 2023. But sophisticated cybercriminal groups like the Lazarus Group have adapted how they use mixers. As we reported in last year’s Cryptocurrency Crime Report, Sinbad became the go-to mixer for North Korea-related hackers in 2022, shortly after the sanctions on Tornado Cash, which had previously been a go-to for these sophisticated cybercriminals Molecule of choice. With Sinbad out, Bitcoin-based mixer YoMix has emerged as its replacement. We can see an example of this in the Reactor diagram below, which shows a wallet associated with North Korean hacking activity receiving funds from YoMix, having previously received funds from Sinbad.
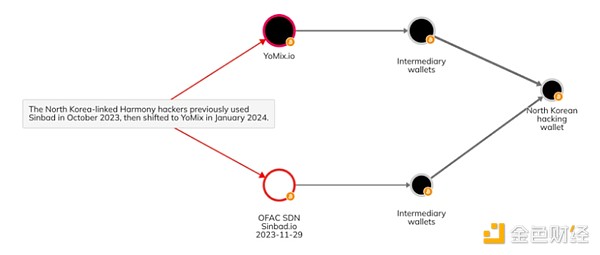
Overall, YoMix saw huge growth in 2023, with inflows increasing more than 5x for the year.

According to Chainalysis data, About a third of YoMix’s inflows come from wallets associated with cryptocurrency hacks. The development of YoMix and its popularity with Lazarus Group is a prime example of the ability of established players to adapt and find alternative mixing services when previously popular mixing services are shut down.
Using cross-chain bridges
Cross-chain bridges allow users to transfer funds from one blockchain to another A blockchain. Generally speaking, anyone can access these smart contracts, although in theory the bridge could implement blacklisting. All of this activity happens on-chain, which means blockchain analysts can track funds through the bridge because there is no centralized entity hosting the funds transferred to the bridge.
As mentioned previously, 2023 has seen a significant increase in the use of bridging protocols by illicit actors for money laundering, particularly in cryptocurrency thefts.
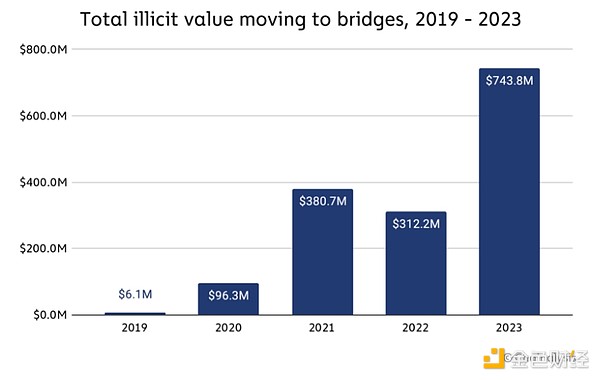
Overall, The bridge protocol received $743.8 million in cryptocurrency from illicit addresses in 2023, compared to only $312.2 million in 2022.
Hackers associated with North Korea are among the most common to exploit cross-chain bridges for money laundering, and we can see an example of this activity on the Reactor diagram below.
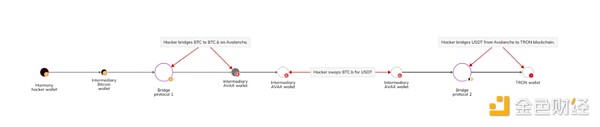
In this case Next, funds related to the 2022 Harmony hack were transferred to the popular bridging protocol in May 2023, from the Bitcoin blockchain to the Avalanche blockchain. These funds are then traded for stablecoins and then bridged again using a different protocol, this time from the Avalanche blockchain to the TRON blockchain.
Sophisticated hackers often adapt money laundering strategies
The changes in money laundering strategies we see from cryptocurrency criminals such as the Lazarus Group remind us that the most sophisticated illicit actors are always on the lookout for Adapting their money laundering strategies and leveraging new crypto services. By researching these new money laundering methods and becoming familiar with the on-chain patterns associated with them, law enforcement and compliance teams can become more efficient.
 ZeZheng
ZeZheng
 ZeZheng
ZeZheng JinseFinance
JinseFinance JinseFinance
JinseFinance Beincrypto
Beincrypto cryptopotato
cryptopotato Bitcoinist
Bitcoinist Numen Cyber Labs
Numen Cyber Labs Bitcoinist
Bitcoinist Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph