Source: Beosin
Beijing time on January 30, 2024, according to Beosin's EagleEye security risk monitoring, early warning and blocking platform monitoring display ,DeFi protocol MIM_Spell was attacked by hackers for flash loans, resulting in a loss of more than 6 million US dollars. Currently, the attacker converted the stolen funds into ETH and transferred them to two attacker addresses. Beosin KYT will continue to monitor the funds while we analyze this vulnerability.
Vulnerability Analysis
The main reason for the incident is The attacker took advantage of the project contract to use the rounding-up algorithm, and controlled the parameter to 1 to maximize the rounding-up error, thus causing the ledger to be unbalanced.
The contract has two functions, namely borrow and repay. One is to borrow money from the contract, and the other is to repay the money to the contract.
The Borrow function will specify the borrowing amount, calculate the debt value through proportional conversion, and update it to the caller's total debt value. As shown in the figure below, the add algorithm of the contract here uses rounding up.
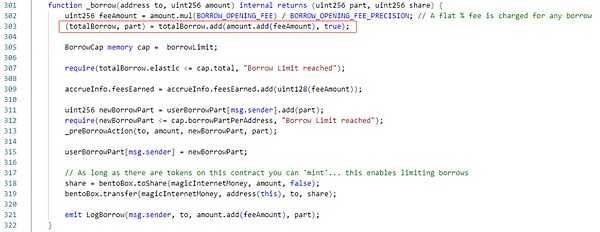

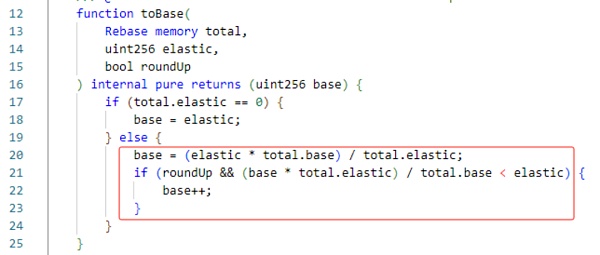
The Borrow function will specify the repayment debt value, calculate the repayment amount through proportional conversion, and transfer the repayment amount to this contract. As shown in the figure below, the sub algorithm of the contract here still uses upward rounding.
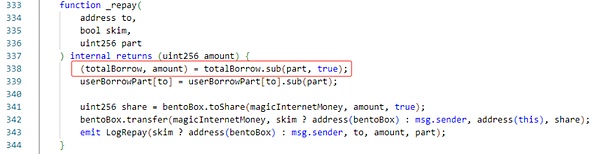

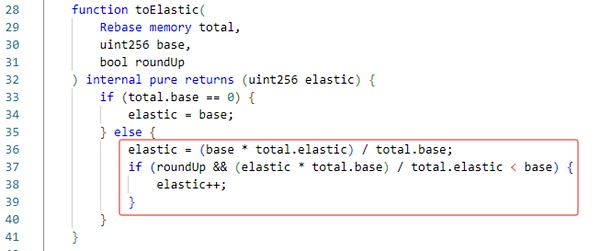
Understand the process of borrowing and repayment, Let’s take a look at how hackers exploited this vulnerability.
The hacker first controls the loan amount and debt value of the contract to 0 and 97 (how to control will be introduced in the next section).
Next, the borrow and repay functions are called continuously, and the borrowing and repayment values are both 1. Finally, the borrowing amount and debt value are controlled to 0 and 120080183810681886665215049728, leading to a serious imbalance in proportions.
According to the above code rules (elastic=0, base=97), when the attacker calls borrow once and passes in 1, the two ledgers will become elastic =1, base=98 (when elastic is 0, it will increase synchronously according to the value), when borrow is called again and 1 is passed in, it will become elastic=2, base=196 (when elastic is not 0, it will be synchronized proportionally) Increase).
Next, the attacker calls the repay function and passes in 1, which will call the sub function. At this time, the calculated elastic should be equal to 1*1/196= >0, but the algorithm rounds up, resulting in the calculation of elastic=1, and the result will become elastic=1, base=195. It can be seen that elastic remains unchanged at this time, but base has doubled.
The attacker used the above method many times to set elastic=0 and base=120080183810681886665215049728. In the end, more than 5 million MIM in the contract were loaned out through a borrow.
Attack process
Now that we understand the problem with the function, let’s take a look at the attack How the attacker carried out the attack (one of the transactions is an example).
1. The attacker first borrowed 300,000 MIM.
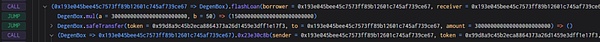
2. Subsequently, the attacker queries the loan amount and debt value in the callback function , you can see that it is 240,000 and 230,000 at this time.
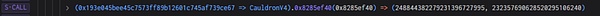
3. Next, the attacker calls the repayForAll function, returns 240,000 MIM tokens, and controls elastic to a very small size.
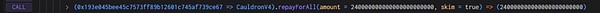

4. Next, the attacker returned the debts of other users through the repay function, and finally controlled the loan amount and debt value to 0 and 97.
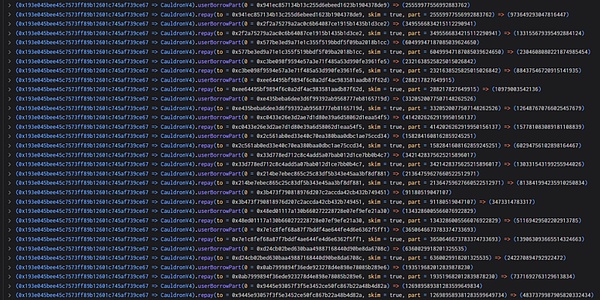

5. The attacker creates a new contract and controls the borrowing amount and debt value to 0 and by appealing to borrow and repay. 120080183810681886665215049728.
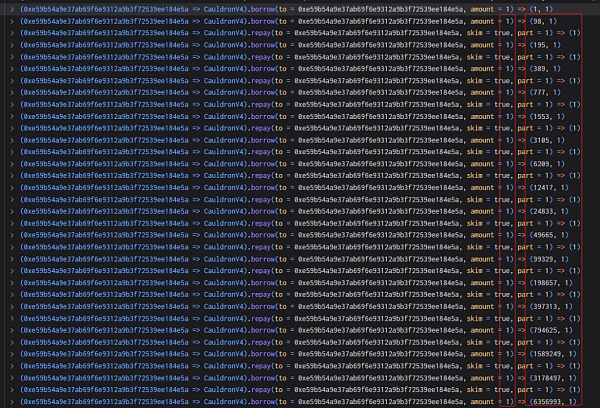

6. Finally, 5 million MIM was loaned out through a borrow and the flash loan was returned.
Fund Tracking
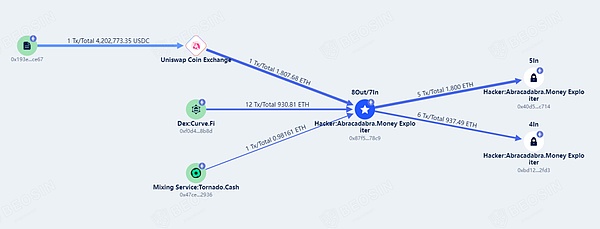
As of press time, the stolen funds of more than 6 million US dollars have all been converted into ETH by the attackers, and have been scattered in the hacker's address and have not been moved. Beosin KYT reversed The money laundering platform will continuously monitor the funds.
 JinseFinance
JinseFinance























