Source: Shenzhen Lingshi Technology
Background
On-chain attacks against DualPools were detected:
https://bscscan.com/tx/0x90f374ca33fbd5aaa0d01f5fcf5dee4c7af49a98dc56b47459d8b7ad52ef1e93
DualPools (https://dualpools.com) ; is based on VenusProtocol (https://venus.io/) Modified, it is a DeFi project that provides Swap, Lend, Borrow and other services.
The operating mode is as follows:
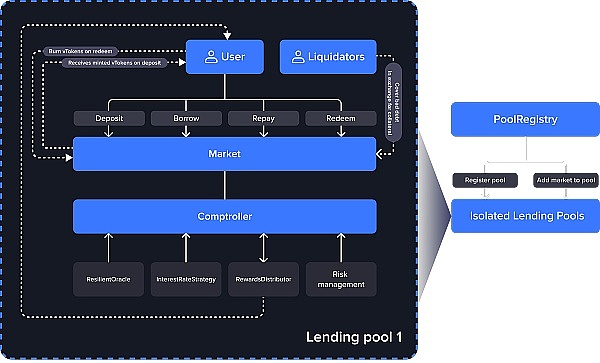
DualPools is a decentralized lending platform. Users deposit underlyingAssets (underlying assets) through deposti and obtain the corresponding dToken; conversely, when withdrawing underlyingAssets through Redeem, the corresponding assets are destroyed. dToken.
Among them, the exchange ratio between underlyingAssets underlying assets and dToken is controlled by exchangeRate (liquidity index). Simply put, exchangeRate is the value of dToken.
exchangeRate = (totalCash + totalBorrows - totalReserves) / totalSupply
Attack Analysis
Simply speaking, the attack is divided into two parts:
1. The hacker used the DualPools new trading pool to have insufficient liquidity (liquidity is 0), which significantly Raise the price of dLINK and borrow the underlying assets of other trading pools (WBNB, BTCB, ETH, ADA, BUSD).
2. Use the problem of precision truncation to get back all the LINK invested in the early stage.
Detailed analysis of step 1
The attacker borrowed money through DODO Private Pool and PancakeSwapV3, and obtained BNB and BUSD as initial attack funds, as shown below :
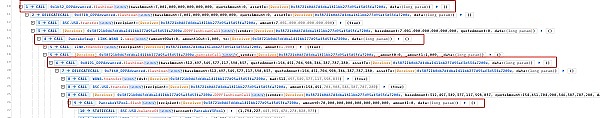
Subsequently, BNB and BUSD were mortgaged through VenusProtocol, and 11,500 LINK was lent to carry out attacks against DualPools.
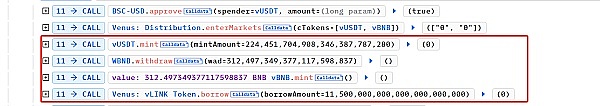
First, the attacker obtained 2 minimum units of dLINK through the transaction pool dLINK-LINKmint, and then transferred 1149999999999999999999998 units of LINK to the transaction pool.
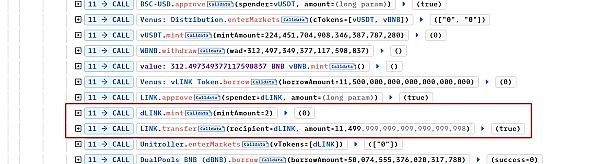
Since the trading pool has not been initialized, there is no liquidity. And exchangeRate is calculated as follows:
exchangeRate = (totalCash + totalBorrows - totalReserves) / totalSupply
At this time, totalCash is the balance of LINK in the transaction pool, which is 11499999999999999999998+2=1150000000000000000000. TotalBorrows and totalReserves are both 0, and totalSupply is 2 (because the hacker obtained 2 minimum units of dLINK through mint). Therefore, the exchangeRate at this time is 5750000000000000000000 (increasing the value of dLINK by 575 times). Since the attacker owned 2 dLINKs and their value was high enough, the hacker borrowed 50 BNB, 0.17 BTCB, 3.99 ETH, 6378 ADA, and 911 BUSD from other pools.
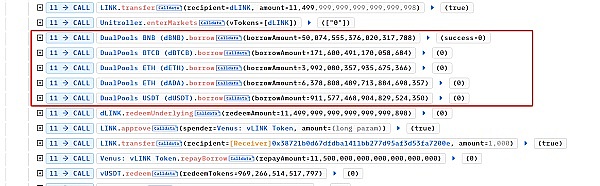
Detailed analysis of step 2
< p style="text-align:left;">The attacker redeemed the 2 minimum units of dLINK from the previous mint into 114999999999999999999898 units of LINK through redeemUnderlying. Because, the exchangeRate was manipulated by the attacker to 5750000000000000000000. Therefore, the dLINK required to exchange 11499999999999999999898 minimum units of LINK is 11499999999999999999898 / 5750000000000000000000 = 1.9999999999999999 That is, 1.999999 minimum units of d LINK, but due to data precision truncation, only 1 minimum unit of dLINK is needed.
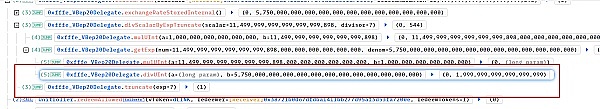
At this point, the attacker has taken out the 11499999999999999999898 units of LINK that he invested previously. Subsequently, the borrowed money from VenusProtocol, PancakeSwapV3, and DODO Private Pool will be returned to complete the attack.
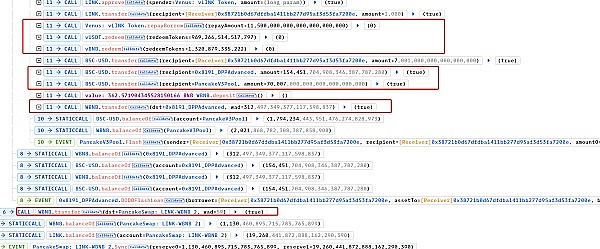
Summary
The attacker takes advantage of the poor liquidity of the DualPools new trading pool to manipulate the exchangeRate of the underlying asset, causing the price of the dToken corresponding to the underlying asset to be distorted, so that a very small dToken can be used as collateral to lend a large amount of other underlying assets. Then, the truncation problem of smart contract division is used to retrieve the assets invested in the previous attack. At this point, the attack on the DeFi project DualPools is completed.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance Coinlive
Coinlive  Beincrypto
Beincrypto Others
Others Bitcoinist
Bitcoinist Beincrypto
Beincrypto Cointelegraph
Cointelegraph Bitcoinist
Bitcoinist Bitcoinist
Bitcoinist Bitcoinist
Bitcoinist