Author: Box | 826.eth Source: X, @BoxMrChen
Recently, more and more friends have come to me and told me that their private keys have been stolen for no apparent reason. To be honest, I don't believe it. However, after many investigations, we found that they actually have a very obvious characteristic, that they are all local dog players. After investigation and summary, we finally summarized a complete process chain. I hope it can be of some inspiration to everyone.
1. Automatically cast a net
With the rapid growth of Sol's ecology, there are now many automated monitoring robots that are very perfect and can obtain a lot of information for analysis, and the attacker first took advantage of this.
Let's use an example to show.
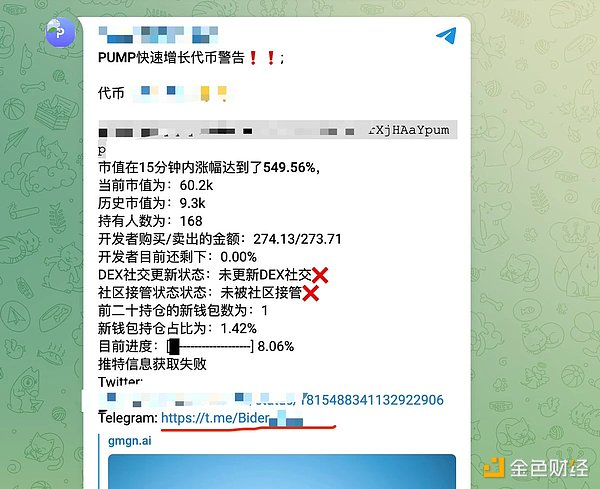
Pay attention to the red line mark, where a Telegram group appeared, which happened to be the main entrance for the theft. Sol's tokens are unique, and a lot of data can be automatically set by uploading Metadata, such as avatars, social links, etc.
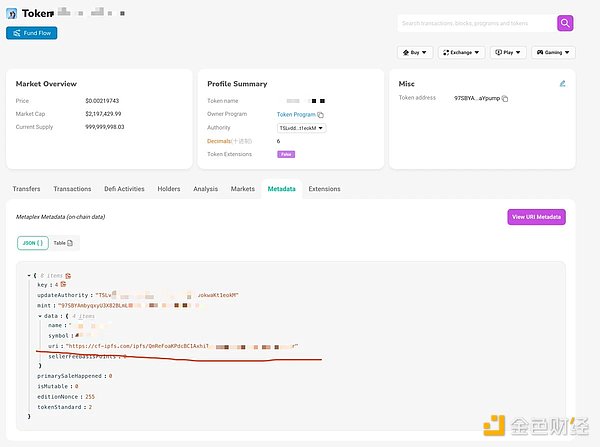

You can see that the data here is exactly the data displayed by the monitoring robot, that is, the attacker took advantage of the fact that everyone would believe in the monitoring robot, a highly credible channel, to spread their phishing links. To trigger this kind of monitoring, you only need to create some robots to pull the market. They only need to make the data look good, and many people will be easily fooled. Go to the next step at this time. 2. False verification If you accidentally click on this TG and want to enter these TG groups, congratulations, you are one step closer to being stolen. Thanks to the latest applet function of TG, attackers have a perfect way to make a fake look real. When you enter these groups, you will see a verification request, which is very common, because many TG groups have to prevent robots, so it is also a very credible demand. When you click on it, you need to be careful.
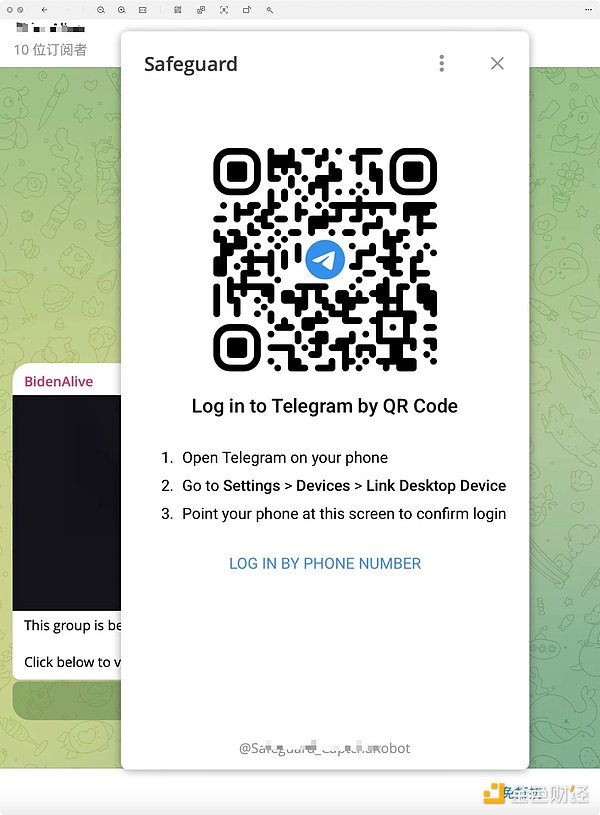
At this time, he will use the TG applet to pop up a fake TG login window. At this time, as long as you accidentally scan the code, I'm sorry, your TG has been logged in and controlled by the attacker.
3. Record scanning
At this stage, the attacker will quickly scan your chat records and your various TG Bots. As we all know, the current TG Bots are basically naked. The attacker can easily take your assets from your Bot, and the target users they attack happen to be these local dog players, which is a clear target user. At this time, many high-value meme coins become the hacker's meal.
At this point, the attack ends. Why is this case worth talking about? Because many users can't even tell that this is a hacker attack. When consulting us, they will not provide any information about TG. They always believe that there are computer Trojans or phishing links. The whole process seems very credible to ordinary users, from the credible monitoring Bot to the credible TG verification, there is no suspicious operation in any part.
Rescue measures
After you scan the code, your information should be synchronized immediately. We recommend that you do the following.
1. Immediately transfer all assets in the Bot, in order from large funds to small funds.
2. Check the devices that have been logged in in TG and immediately exit the suspicious devices.
3. Contact TG regulars and declare that your TG account has been stolen to prevent further credible dissemination.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Bitcoinist
Bitcoinist Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph