Author: Keystone Source: X, @KeystoneCN
1. Understand what Permit is in one minute
Let's start with a short story about borrowing money:
I am going to borrow 1 million from my good friend Jack Ma. Jack Ma picked up the phone and called the bank without saying a word. After confirming his identity, he told the bank: I want to authorize a withdrawal limit of 1 million to someone. The bank replied that it had received the authorization and recorded it.
The next step is to go to the bank and tell the counter that I am going to take the 1 million that Jack Ma authorized me to take. At this time, the bank will check whether there is any authorization record and give me 1 million after confirming that I am someone.
This short story can be regarded as the embodiment of Approve authorization on ETH. In this process, authorization can only be obtained by Jack Ma (the asset owner) calling the bank to authorize (on the chain), and the bank (Token contract) manages these authorizations, and then I (the authorized party) can transfer money from the bank that is not higher than the authorized amount. If the bank does not find the authorization record, my withdrawal application will undoubtedly be rejected.
Okay, if I change to another authorization method - Permit, what will happen to the process if I borrow money from Jack Ma?
This time I asked to borrow another 1 million yuan, and the generous Jack Ma was too lazy to call. He took a check from his pocket, filled in the amount and signed it and gave it to me. I took this check to the bank to exchange it. At this time, although the bank had no authorization record, with Jack Ma's signature on the check, the bank confirmed the authenticity of the check and paid me the specified amount of money.
I believe that you have already seen the difference in the process between the two. Approve, as an important function in ERC-20, has been widely used shortly after ETH was launched. Why was the Permit method introduced in ERC-2612 to achieve the same effect?
2. Why is Permit needed?
The ERC-2612 proposal was proposed in March 2019 and the final review was completed in October 2022. Its launch is closely related to the multiple surges in gas prices on the ETH mainnet during this period.
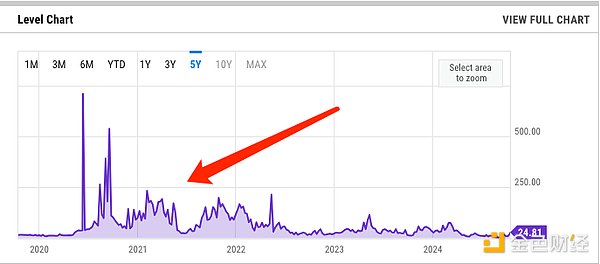
Figure: ETH mainnet gas price remained high during 2020-2022
The violent bull market and the wealth-creating effect of new projects on the chain have increased the enthusiasm of users for transactions on the chain, and they are willing to pay higher fees to get transactions on the chain faster, because sometimes getting on the chain one block in advance often means higher returns.
However, the consequence of this phenomenon is that when users trade tokens on the chain, they often need to bear high gas fees. Under the Approve method, 2 TXs are required to complete a token swap. For users with small amounts of funds, the transaction fees are simply a nightmare.
The Permit introduced by ERC-2612 changes the authorization process to an offline signature. It does not need to be put on the chain immediately, but only needs to be provided when transferring tokens. It is like me who got Jack Ma's check in the story of borrowing money. I only need to verify the check with the bank when withdrawing money.
Busy Jack Ma saved a phone call, and it seems that the user also saved a TX. The cost savings are considerable when the gas price is high, and it seems to be a happy ending. But little did they know that Pandora's box was also quietly opening...

3. Wild growth like a volcanic eruption
Before the emergence of Permit, one of the means for hackers to phish cryptocurrency users was to induce users to sign Approve transactions. Such transactions require users to spend gas, which is easy to cause vigilance and fail. Even if the user clicks it quickly, since it takes a certain amount of time for the transaction to be uploaded to the chain, the user who comes to his senses can immediately submit a transaction with the same nonce to rescue it. Relatively speaking, it is not so easy for hackers to succeed.
The emergence of Permit is undoubtedly a sleepy pillow for hackers. Compared with Approve, Permit does not consume gas and only requires signatures, which reduces the vigilance of users. At the same time, due to the characteristics of offline signatures, the initiative is in the hands of hackers. Not only can users not regret it, but hackers can also use authorization to choose the right time to do bad things and maximize their benefits.
The adverse effects brought about by this are the surge in the number of phishing victims and the amount of stolen money we can see. According to @ScamSniffer's statistics:
The amount of losses suffered by phishing victims in 2023 was US$295 million.
In the first half of 2024, this amount has exceeded US$314 million.
At the end of Q3 in 2024, there was a big one: the wallet address suspected to be Shenyu suffered a Permit phishing attack, losing 12,000 $spWETH, worth 200 million yuan.
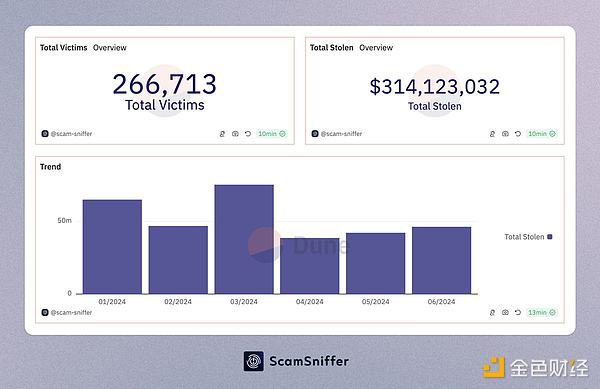
Figure: ScamSniffer 2024 First Half Phishing Attack Statistics Report
Such a scene is believed to be beyond the expectations of the original proposal developers. The original intention of introducing Permit was to reduce users' gas costs and improve user experience and efficiency. It was thought to be a double-edged sword with gains and losses, but it turned out to be a big kitchen knife with a sharp edge, which directly cut a big hole in the shield of user asset security.
There are many other signature authorization methods similar to Permit, such as Permit2 launched by Uniswap, which allows all ERC-20 tokens to support offline signatures. As the No. 1 DEX, UniSwap's move also increased users' reliance on offline signatures and increased the risk of being phished.
4. How to prevent it?
So, as ordinary users, facing this big knife of Damocles hanging over our heads, what are the preventive measures to avoid losses?
1. Raise awareness
Be calm about the temptation of airdrops
The airdrops from currency projects are indeed very attractive, but most of the time they are phishing attacks in the name of fake airdrops. When encountering such information, don’t be overwhelmed and directly "receive" it. Confirm the authenticity and official website of the airdrop through multiple sources to avoid entering phishing websites.
Avoid blind signing
If you are unlucky enough to enter a phishing website, and you are not aware of it, when the transaction window pops up in your wallet, you should carefully check the transaction content. When words such as Permit, Permit2, Approve, IncreaseAllowance, etc. appear, it means that this transaction is to take away token authorization. You should be vigilant because the normal airdrop process does not require this. Keystone also implements transaction analysis and display on the hardware side. Users can use transaction analysis to avoid blind signing and avoid serious consequences caused by impulse.
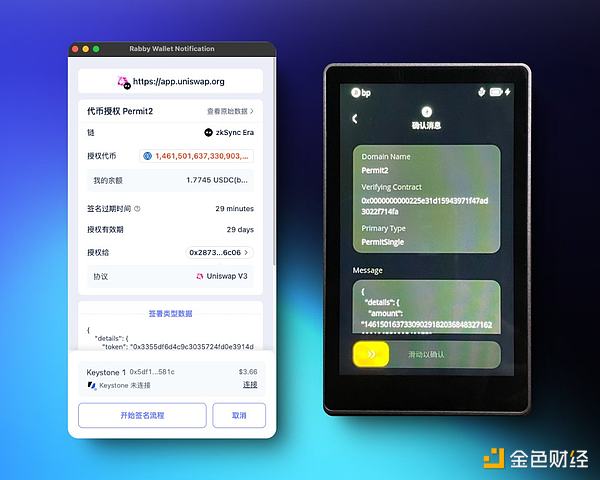
Figure: Keystone hardware wallet and Rabby Wallet parse and display Permit2 signature transaction
2. Make good use of tools
ScamSniffer
As an ordinary user, it is very difficult to accurately identify phishing websites, and it is inevitable that there will be fish that slip through the net. With the help of ScamSniffer's browser plug-in, before entering a suspected phishing website, you will receive a reminder from the plug-in, and the user can stop interacting in time after receiving the reminder.
Revoke
Revoke.cash can display the token authorization records in the user's wallet. We recommend revoking suspicious authorizations with unlimited amounts. Develop the habit of cleaning up authorizations regularly and try to do as few authorizations as possible that exceed the required amount.
3. Asset isolation and multi-signature
As the saying goes, don't put all your eggs in one basket, and this also applies to cryptocurrency assets. For example, we can store large amounts of assets in cold wallets such as Keystone, and use small amounts of hot wallets for daily interactions. Even if we are accidentally hacked, the assets will not be taken away in one go.
If you have higher requirements for security, you can use multi-signature to further improve security. For assets that have been added to the multi-signature, the assets can only be transferred when the number of wallet consents reaches the threshold. If a single wallet that does not reach the threshold is stolen, the hacker cannot get hold of the assets.
5. Conclusion
We cannot deny the value of Permit, but the recent increasing number of thefts also shows that it seems to cause greater harm. Just like the ethsign method in the past, it was favored by hackers at the time due to its poor readability and huge harm. Now it has been blocked and abandoned by most wallet software, and its functions have been replaced by some safer methods.
Focusing on Permit, has it also reached the same crossroads that ethsign once faced? Improvement and upgrading or abandonment requires ETH developers to spend some time thinking and discussing.
 Weatherly
Weatherly










