Introduction
With the continuous development of blockchain technology, Bitcoin not only exists as a cryptocurrency, but its ecosystem is also expanding and deepening. The Bitcoin expansion ecosystem covers a variety of Layer 2 solutions and applications. These extensions not only improve the transaction speed and efficiency of Bitcoin, but also provide support for emerging fields such as smart contracts, decentralized finance (DeFi), and non-fungible tokens (NFTs). These innovations have made Bitcoin's application scenarios more extensive. It is no longer limited to value storage and peer-to-peer payments, but can meet more complex and diverse needs, promoting the progress of the entire blockchain industry.
However, as the ecosystem expands, security issues are gradually emerging. New technologies and applications bring more potential risks and challenges. How to ensure the security of the system while improving functions has become the key. Security vulnerabilities, attacks, and technical defects not only threaten the security of users' assets, but may also affect the overall stability and trust of the Bitcoin network. ScaleBit, a subsidiary of BitsLab, wrote this article to explore the construction process of the Bitcoin expansion ecosystem, the security incidents it faces, and the future outlook in terms of security. By analyzing the current technical solutions and security challenges, it aims to provide valuable insights and suggestions for the development of the Bitcoin ecosystem to ensure that it can maintain a high degree of security and reliability during its continuous expansion.

What is the Bitcoin expansion ecosystem?
The Bitcoin expansion ecosystem mainly refers to the various expansion solutions and application ecosystems developed around the Bitcoin basic network. Bitcoin was originally designed to be used for peer-to-peer payments and value storage, but with the development of blockchain technology, the Bitcoin community and developers are also exploring how to add more functions to it, especially in smart contracts, decentralized finance (DeFi), NFTs, and more efficient transaction expansion.
How does the Bitcoin expansion ecosystem work?
The operation of the Bitcoin expansion ecosystem mainly depends on the expansion technologies and protocols built on or outside the Bitcoin main chain, which enable Bitcoin to support more diverse application scenarios. The following are the operating principles of several key technologies in the Bitcoin ecosystem:
(1) Lightning Network
The Lightning Network is one of the most mature and widely used solutions for Bitcoin Layer 2. It establishes payment channels to move a large number of small transactions from the main chain to the off-chain, thereby greatly improving Bitcoin's transaction speed and reducing transaction fees.
Trends: The infrastructure of the Lightning Network is constantly improving, and the user experience is also improving. More and more merchants are beginning to support Lightning payments.
Challenges: Liquidity issues and routing efficiency still need to be further optimized, especially in large-value transaction scenarios.
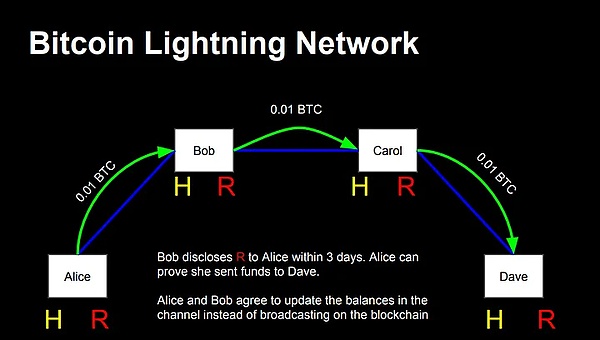
Source: https://lightning.network/lightning-network-presentation-time-2015-07-06.pdf
(2)Liquid Network (LQ)
Liquid Network is a sidechain running on the open source Elements blockchain platform, designed for faster transactions between exchanges and institutions. It is governed by a distributed alliance of Bitcoin companies, exchanges and other stakeholders. Liquid uses a two-way peg mechanism, converting BTC to L-BTC and vice versa.
Liquid supports confidential transactions and tokenization, making it suitable for enterprise applications. If Bitcoin is the value layer of the Internet and Lightning is the peer-to-peer payment network in the Bitcoin-driven financial system, then Liquid is the financial layer, adding multi-asset support and financial instruments such as securities and commodities.
Compared to Lightning, Liquid is a Layer 2 solution for Bitcoin that focuses on facilitating larger and more complex transactions, such as issuing and trading assets such as securities and stablecoins. Liquid has built-in confidential transactions that hide transaction amounts and asset types, while Lightning mainly provides privacy through its off-chain transactions. While Lightning excels at small payments and daily transactions, Liquid is more suitable for institutional finance, asset issuance, and cross-border transactions.
With over 50 exchanges now using Liquid Network, it has facilitated billions of dollars in transactions, proving its effectiveness in increasing the utility of Bitcoin for institutional trading. Liquid Network is able to provide faster settlement times for exchanges, thereby increasing liquidity in the Bitcoin market and enabling institutions to operate more efficiently and securely.
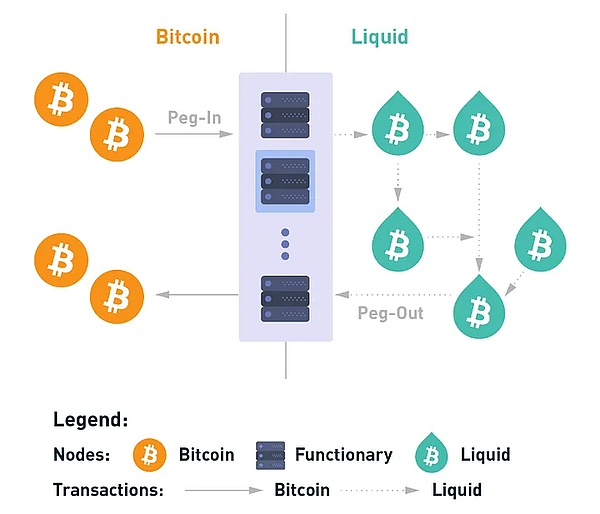
Source: https://docs.liquid.net/docs/technical-overview
(3)Rootstock Infrastructure (RBTC)
Rootstock is the longest-running Bitcoin sidechain since its inception in 2015 and launched its mainnet in 2018. It is unique in that it combines the security of Bitcoin’s Proof of Work (PoW) with Ethereum’s smart contracts. As an open-source, EVM-compatible Bitcoin Layer 2 solution, Rootstock provides an on-ramp to the growing dApp ecosystem and is committed to achieving full trustlessness.
Similar to Liquid, Rootstock uses a two-way peg so users can easily swap between BTC and RBTC. RBTC is the native currency on the RSK blockchain and is used to pay miners for processing transactions and contracts. While Liquid focuses on fast, private transactions and asset issuance, Rootstock expands Bitcoin's DeFi and dApp ecosystem through smart contracts.
As of this writing, Rootstock has a total value locked (TVL) of over $170 million and a market cap of $380 million.
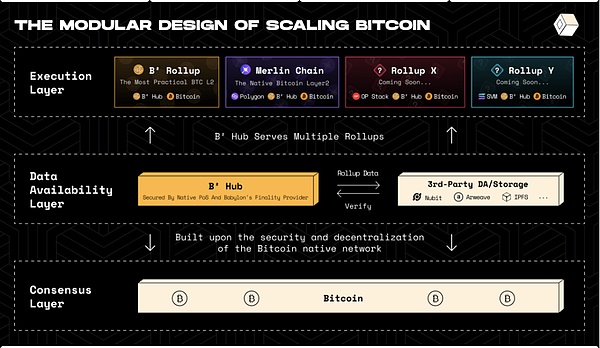
(4)B² Network
The technical architecture of B² Network consists of two layers: Rollup layer and Data Availability (DA) layer. B² Network aims to redefine users' views on Bitcoin's second-layer solutions.
B² adopts ZK-Rollup as the Rollup layer. The ZK-Rollup layer adopts the zkEVM solution and is responsible for executing user transactions and output-related proofs within the second-layer network. User transactions are submitted and processed on the ZK-Rollup layer. User status is also stored on the ZK-Rollup layer. Batch proposals and generated zero-knowledge proofs are forwarded to the data availability layer for storage and verification.
The data availability layer includes distributed storage, B² nodes, and the Bitcoin network. This layer is responsible for permanently storing a copy of the Rollup data, verifying the Rollup's zero-knowledge proof, and ultimately performing final confirmation on Bitcoin.
Distributed storage is a key aspect of the B² Network, serving as a repository for ZK-Rollup user transactions and their associated proofs. By decentralizing storage, the network fundamentally improves security, reduces single points of failure, and ensures data immutability.
To guarantee data availability, B² also writes a Tapscript script to the Bitcoin network in each Bitcoin block, as shown below. The script anchors the data path and zero-knowledge proof of the Rollup that is effectively stored in decentralized storage during this period. This process is cost-controlled and generates 6 transactions per hour. Therefore, when verifying, users will compare the transactions and Taproot script data on Bitcoin Layer1 one by one to ensure the ultimate credibility of the Rollup data.
(5)Stacks Protocol (STX)
Since its launch on the mainnet under the name of Blockstack in 2018, Stacks has become the leading Bitcoin Layer 2 solution.
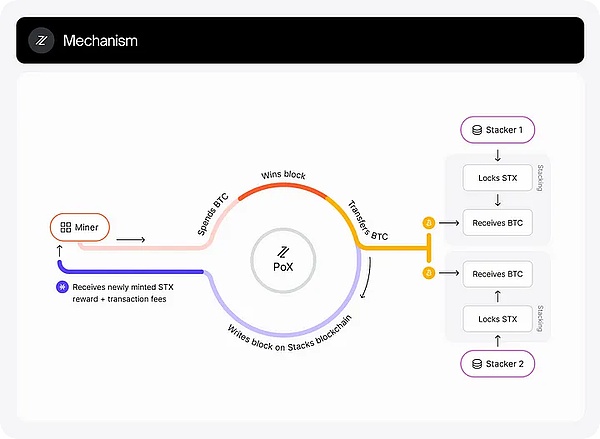
Source: https://docs.stacks.co/stacks-101/proof-of-transfer
Stacks connects directly to Bitcoin, allowing smart contracts, dApps, and NFTs to be built on Bitcoin, significantly expanding Bitcoin's functionality to make it more than just a value storage tool. It uses a unique proof-of-transfer (PoX) consensus mechanism that directly links its security to Bitcoin without modifying Bitcoin itself.
With over $99 million in total value locked (TVL), Stacks’ established infrastructure and growing developer community make it a project to be reckoned with in the space.
(6)Babylon
Babylon’s vision is to extend the security of Bitcoin to protect the decentralized world. By leveraging three aspects of Bitcoin — its timestamping service, block space, and asset value — Babylon is able to deliver Bitcoin’s security to numerous Proof-of-Stake (PoS) chains, creating a stronger, unified ecosystem.
Babylon's Bitcoin staking protocol uses a remote staking approach that overcomes the lack of smart contracts through cryptography, consensus protocol innovations, and optimized use of the Bitcoin scripting language. Babylon's staking protocol allows Bitcoin holders to trustfully stake Bitcoin without bridging to a PoS chain, and provides complete slashable security guarantees for that chain. Babylon's innovative protocol eliminates the need for bridging, wrapping, and hosting of staked Bitcoin.
A key aspect of Babylon is its BTC timestamp protocol. It timestamps events from other blockchains onto Bitcoin, allowing these events to enjoy Bitcoin's timestamps just like Bitcoin transactions. This effectively borrows the security of Bitcoin as a timestamp server. The BTC timestamp protocol enables fast stake unbinding, composable trust, and reduced security costs to maximize liquidity for Bitcoin holders. The protocol is designed as a modular plug-in that can be used on top of a variety of different PoS consensus algorithms and provides a foundation for building a reset protocol.

After exploring the various technical solutions for Bitcoin's expansion ecosystem, we can clearly see that these innovations have not only significantly improved the performance and functionality of the Bitcoin network, but also provided a solid foundation for the diversification of its application scenarios. However, with the continuous expansion of the expansion ecosystem and the increasing complexity of technology, security issues have also emerged and become an important aspect that cannot be ignored. New expansion technologies introduce more potential risks and attack vectors, making the overall security of the system face greater challenges.
In this context, ensuring the security of Bitcoin's expansion ecosystem is not only related to the protection of user assets, but also to the stability and trust of the entire network. Therefore, this section will introduce the vulnerabilities of the Lightning Network in 2023 in detail, providing a valuable reference for future security protection.
Security incidents in Bitcoin's expansion ecosystem
In October 2023, Bitcoin's expansion technology, the Lightning Network, was found to have a potential security vulnerability. After discovering the vulnerability, developer Antoine Riard announced the relevant details.
This vulnerability, known as "replacement cycling attacks," could compromise the security of funds flowing through the Lightning Network, causing transactions to be delayed or not processed as expected, which could result in the risk of losing funds within the Bitcoin Lightning Network channel.
This incident highlights that security must always be top priority in a rapidly evolving expansion ecosystem. Developers and the community need to continuously monitor and improve existing expansion solutions to guard against potential security threats and ensure the safety of user funds.

Prospects for the security of the Bitcoin extension ecosystem
Although the Bitcoin extension ecosystem has made significant progress in improving transaction efficiency and functional diversity, its security still needs to be continuously strengthened. This section will explore the future development direction and challenges of the Bitcoin extension ecosystem in terms of security.
The Bitcoin extension ecosystem aims to solve the transaction throughput problem of the main chain while ensuring security and decentralization.
Trust model of off-chain transactions: Bitcoin's expanded ecosystem uses off-chain technology to increase transaction speed. Developers need to ensure that the trust mechanism of off-chain transactions is reliable enough. For example, the two-way payment channel in the Lightning Network needs to use multi-signature technology and ensure that the channel closing process is safe to prevent funds from being frozen or lost.
Privacy and transparency: The channel transactions of the Lightning Network can be completed without being public. Although it improves privacy, it also increases the difficulty of supervision and potentially triggers malicious behavior. Layer 2 networks need to strike a balance between privacy and transparency, and enhance compliance by selectively disclosing some transaction records.
User experience and security: The complexity of the expanded ecosystem brings difficulty to user operations. For example, the channel management of the Lightning Network may not be friendly to ordinary users, increasing the risk of operational errors. The Bitcoin expansion ecosystem can improve user experience and reduce security risks by designing more friendly interfaces and simplified operation tools.
Looking forward, the Bitcoin expansion ecosystem needs to continuously optimize technical solutions, improve user experience, and strengthen regulatory compliance while maintaining decentralization and security to achieve more robust and widespread applications.
Summary
The Bitcoin expansion ecosystem has significantly improved the functionality and transaction efficiency of the Bitcoin network through a variety of Layer 2 solutions and innovative protocols, and promoted the development of emerging fields such as smart contracts, DeFi, and NFT.
However, as the ecosystem continues to expand, security issues are gradually emerging, which requires the high attention of developers and the community. In the future, while pursuing higher transaction throughput and diversified applications, the Bitcoin ecosystem must continue to strengthen security mechanisms, optimize user experience, balance privacy and transparency, and ensure that it achieves more extensive and robust development based on decentralization and security.
Read the full report:https://bitslab.xyz/reports-page
 Brian
Brian
 Brian
Brian Alex
Alex Joy
Joy Brian
Brian Joy
Joy Brian
Brian Weiliang
Weiliang Miyuki
Miyuki Alex
Alex Brian
Brian