Lazarus Group
2023 Updates< /p>
According to public information in 2023, as of June, there were still no major cryptocurrency thefts attributed to the North Korean hacker Lazarus Group. Judging from on-chain activities, North Korean hackers Lazarus Group are mainly laundering cryptocurrency funds stolen in 2022, including approximately US$100 million in funds lost in the Harmony cross-chain bridge attack on June 23, 2022.
Subsequent facts show that in addition to laundering the cryptocurrency funds stolen in 2022, the North Korean hacker Lazarus Group is not idle at other times. Hibernating in the dark, secretly carrying out APT-related attacks. These activities directly led to the cryptocurrency industry’s “Dark 101,” which began on June 3.
During the "Dark 101 Days", a total of 5 platforms were stolen, with the amount stolen exceeding US$300 million. Most of the stolen objects were centralized services. platform.

Around September 12, SlowMist and its partners discovered that the hacker group Lazarus Group conducted large-scale APT attacks targeting the cryptocurrency industry. The attack method is as follows: first, disguise the identity, deceive the auditor through real-person authentication and become a real customer, and then make a real deposit. Under the cover of this customer identity, Mac or Windows customized Trojans are accurately targeted at official personnel at multiple communication time points between official personnel and customers (attackers). After obtaining permission, they move laterally within the intranet and lurk for a long time to achieve the goal. Purpose of stealing funds.
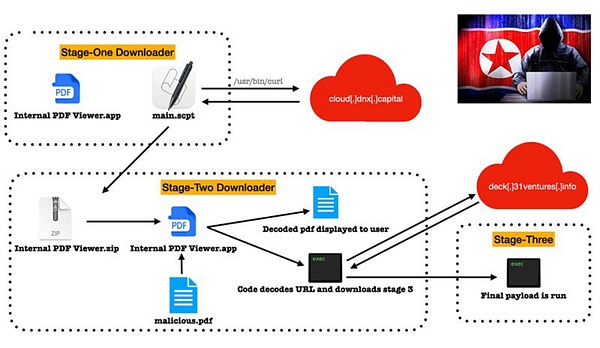
The U.S. FBI is also paying attention to major thefts in the cryptocurrency ecosystem, and publicly stated in a press release that it was controlled by the North Korean hacker Lazarus Group. The following is the relevant press release issued by the FBI in 2023 about the North Korean hacker Lazarus Group:
On January 23, the FBI confirmed (https://www.fbi.gov/news/press-releases/fbi-confirms-lazarus-group-cyber-actors-responsible-for-harmonys-horizon-bridge-currency-theft) North Korean hackers Lazarus Group should be responsible for the Harmony Hack incident.
On August 22, the FBI issued a notice (https:// www.fbi.gov/news/press-releases/fbi-identifies-cryptocurrency-funds-stolen-by-dprk) stated that the North Korean hacker group involved Atomic Wallet, Alphapo and CoinsPaid in hacking attacks, stealing a total of $197 million in cryptocurrency. .
On September 6, the FBI issued a press release (https:/ /www.fbi.gov/news/press-releases/fbi-identifies-cryptocurrency-funds-stolen-by-dprk), confirmed that North Korean hackers Lazarus Group were responsible for the theft of $41 million from the Stake.com cryptocurrency gambling platform.
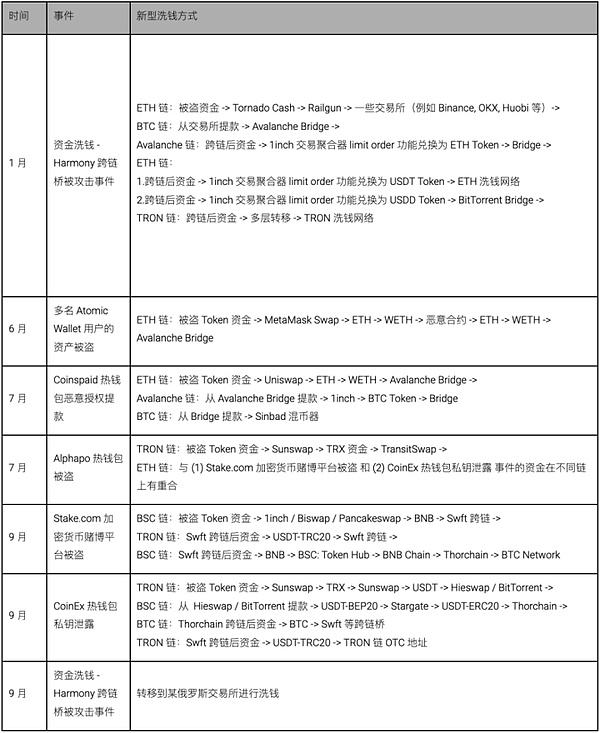
Analysis of money laundering methods
According to our analysis, the money laundering methods of North Korean hackers Lazarus Group have also continued to evolve over time. New money laundering methods will appear every once in a while. The timetable for changes in money laundering methods is as follows:
Gang profiling analysis
Based on the strong intelligence-related support of InMist intelligence network partners, the SlowMist AML team analyzed these stolen The data related to the incident and the hacker group Lazarus Group were followed up and analyzed to obtain a partial portrait of the hacker group Lazarus Group:
Often use European or Turkish identities as disguises.
Dozens of IP information, dozens of email information and partial desensitization have been mastered Post-identity information:
111.*.*.49
103.*.*.162
103.*.*.205
210.*.*.9
103.*.*.29
103.*.*.163< /p>
154.*.*.10
185.*.*.217
Wallet Drainers
Note: This section was lovingly written by Scam Sniffer. grateful.
Overview
Wallet Drainers are relevant as a cryptocurrency Malware has achieved significant "success" in the past year. The software was deployed on phishing websites to trick users into signing malicious transactions and then steal assets from their cryptocurrency wallets. These phishing campaigns continue to attack ordinary users in many forms, resulting in many people suffering significant property losses after unknowingly signing malicious transactions.
Stolen statistics

In the past year, Scam Sniffer has monitored that Wallet Drainers has stolen from approximately 320,000 victims Withdrawn nearly US$295 million in assets.
Stolen Trends

It is worth mentioning that nearly 7 million US dollars was stolen on March 11. Mostly due to the fluctuation of the USDC exchange rate, I encountered a phishing website pretending to be Circle. There has also been a large number of hacks approaching the Arbitrum Discord hack on March 24th and subsequent airdrops.
Each wave peak is accompanied by related mass events. It might be an airdrop, or it might be a hacking incident.
Notable Wallet Drainers
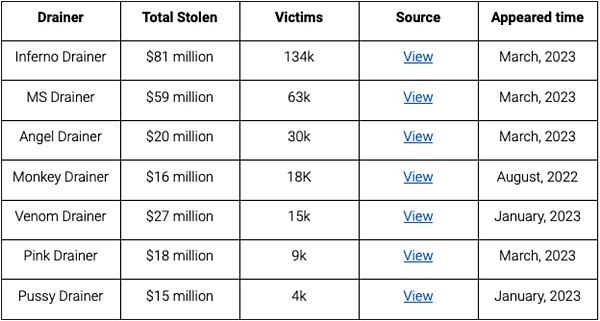
After ZachXBT exposed Monkey Drainer, they announced their withdrawal after being active for 6 months , and then Venom took over most of their clients. Then MS, Inferno, Angel, and Pink also appeared around March. As Venom ceased service around April, most of the phishing gangs turned to other services. At a 20% Drainer fee, they made at least $47 million from selling their services.
Wallet Drainers Trend

By analyzing trends, it can be found that phishing activities have been growing relatively speaking. And after every Drainer quits, there will be a new Drainer to replace them. For example, after Inferno recently announced his withdrawal, Angel seems to have become the new replacement.
How did they launch the fishing campaign?

The ways in which phishing websites obtain traffic can be roughly divided into several categories:
Hacker attack
Natural traffic
Paid traffic
Google Search Ads
Twitter Ads
Although hacker attacks have a large impact, the response is often sufficient In a timely manner, usually within 10-50 minutes, the entire community takes action. However, airdrops, organic traffic, paid advertising, and invalid Discord links are occupied, and these methods are even more difficult to detect. In addition, there are also more targeted private message phishing of individuals.
Common phishing signatures

There are different ways to initiate malicious phishing signatures for different asset types. The above are some Common phishing signature methods for different types of assets. Drainers decide what kind of malicious phishing signature to launch based on the type of assets the victim’s wallet holds.
From the case of using GMX's signalTransfer to steal the Reward LP token, we can find that they have conducted very detailed research on the phishing methods of specific assets.
Use smart contracts more
1) Multicall

Starting from Inferno, they also began to devote more resources to the use of contract technology. For example, the Split fee needs to be divided into two transactions, and this may not be fast enough, causing the victim to revoke the authorization in advance during the second transfer. Therefore, in order to improve efficiency, they use multilcall for more efficient asset transfers.
2) CREATE2 & CREATE

Similarly in order to bypass the security verification of some wallets, they also began to try to use create2 or create to dynamically generate temporary addresses. This will render the blacklist on the wallet side ineffective and increase the difficulty of phishing research. Because you don’t know what address the assets will be transferred to without signing, and the temporary address has no analytical significance. This is a big change from last year.
Phishing website

By analyzing the number trend of phishing websites, it can be clearly seen that phishing activities are gradually increasing every month , which has a lot to do with the stable wallet drainer service.
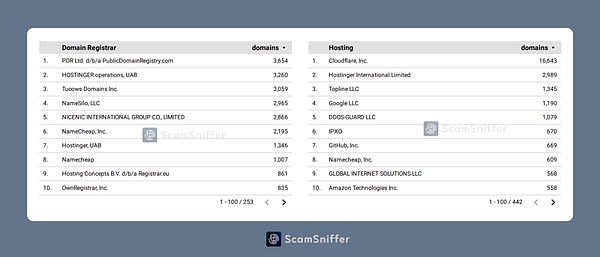
The above are the domain name registrars mainly used by these phishing websites. By analyzing the server address, we can find that most of them use Cloudflare to hide the real server address.
Money laundering tool
Sinbad
Sinbad is a Bitcoin mixer founded on October 5, 2022, which obfuscates transaction details to hide the flow of funds on the chain.
The U.S. Treasury Department describes Sinbad as a "virtual currency mixer that serves as the primary money laundering vehicle for the Lazarus Group, an OFAC-designated North Korean hacking group." Sinbad processed funds from the Horizon Bridge and Axie Infinity hacks and also moved funds related to "sanctions evasion, drug trafficking, purchase of child sexual abuse material, and other illicit sales on darknet markets."
Alphapo hackers (Lazarus Group) have used Sinbad in money laundering processes, such as transactions:

(https://oxt.me/transaction/2929e9d0055a431e1879b996d0d6f70aa607bb123d12bfad42e1f507d1d200a5)
Tornado Cash
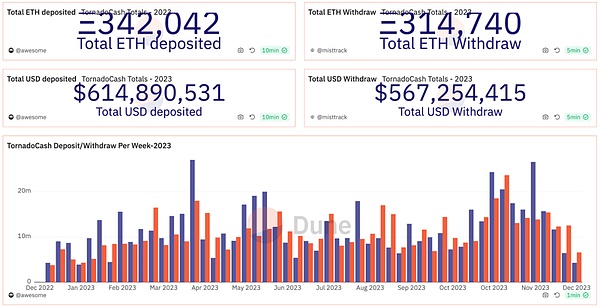
(https://dune.com/misttrack/mixer-2023)
Tornado Cash is A fully decentralized, non-custodial protocol that improves transaction privacy by breaking the on-chain link between source and destination addresses. To protect privacy, Tornado Cash uses a smart contract that accepts ETH and other token deposits from one address and allows them to withdraw to a different address, i.e. sending ETH and other tokens to any address in a way that hides the sending address. .
In 2023, users deposited a total of 342,042 ETH (approximately $614 million) into Tornado Cash, and withdrew a total of 314,740 ETH (approximately $567 million) from Tornado Cash.
eXch

(https://dune.com/misttrack/mixer-2023)
In 2023, users deposited a total of 47,235 ETH (approximately $90.14 million) to eXch, and a total of 25,508,148 ERC20 stablecoins (approximately $25.5 million) to eXch.
Railgun
Railgun uses zk-SNARKs cryptography technology Make transactions completely invisible. Railgun works by “shielding” the user’s tokens within its privacy system so that every transaction appears on the blockchain as being sent from a Railgun contract address.
In early 2023, the FBI said the North Korean hacker gang Lazarus Group used Railgun to launder more than $60 million stolen from Harmony's Horizon Bridge.
Summary
This article introduces the North Korean hacker Lazarus Group's 23-year history, the SlowMist security team has continued to pay attention to the hacker group, summarized and analyzed its dynamics and money laundering methods, and output a portrait of the gang. In 2023, phishing gangs have been rampant, causing huge financial losses to the blockchain industry, and the actions of such gangs have the characteristics of "relay". Their continuous and large-scale attacks have caused greater challenges to the security of the industry. I would like to thank you for this. Web3 anti-fraud platform Scam Sniffer contributed disclosures about the phishing group Wallet Drainers, which we believe is an important reference for understanding how it works and makes money. Finally, we also introduced the money laundering tools commonly used by hackers.
Full report download:
https://www.slowmist.com/report/ 2023-Blockchain-Security-and-AML-Annual-Report(CN).pdf
 Kikyo
Kikyo
 Kikyo
Kikyo CoinBold
CoinBold Davin
Davin TheBlock
TheBlock Bitcoinist
Bitcoinist Catherine
Catherine Catherine
Catherine Others
Others Catherine
Catherine Bitcoinist
Bitcoinist