Source: Beosin
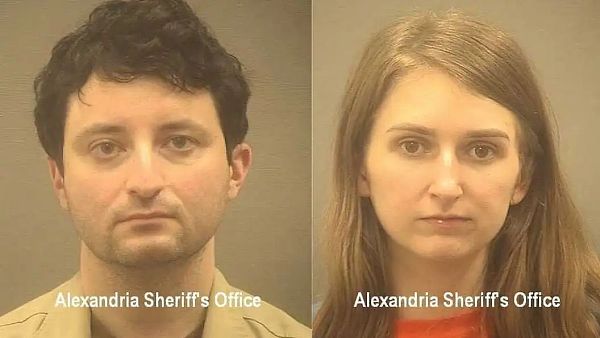
In 2022, Ilya Lichtenstein and Heather Morgan, known as the "crypto-stealing couple" Morgan)Arrested for conspiring to launder $4.5 billion worth of crypto assets stolen in the Bitfinex hack. They pleaded guilty last year.
Now, Lichtenstein has appeared as a cooperating U.S. government witness in an ongoing money laundering trial surrounding cryptocurrency mixing service Bitcoin Fog, according to a new report from Bloomberg. Why did the man behind the $4.5 billion Bitfinex incident become a federal witness in the money laundering trial? Today we will sort out the ins and outs of this virtual currency money laundering case.
Overview of the incident
In order to facilitate your understanding, we have summarized the timeline of this hacking incident as follows:
p>
In 2016, Hittenstein and his wife Heather Morgan stole $4.5 billion worth of Bitcoin from the Bitfinex exchange, but they are still at large;
https://gist.github.com/MrChrisJ/4a959a51a0d2be356cc2e89566fc1d87#file-20170127-bitfinex_hacked_coins-csv
In April 2021, the FBI arrested someone who could be used for money laundering Roman Sterlingov, the main operator of the platform Bitcoin Fog.
In 2021, the Bitcoin Fog and Helix platforms involved in money laundering were shut down, and the creator of Helix also pleaded guilty that year;
February 1, 2022 , the U.S. government’s wallet address received a huge amount of funds, approximately 94643.3 Bitcoins.The picture below shows the flow of funds tracked by the Beosin KYT anti-money laundering platform.
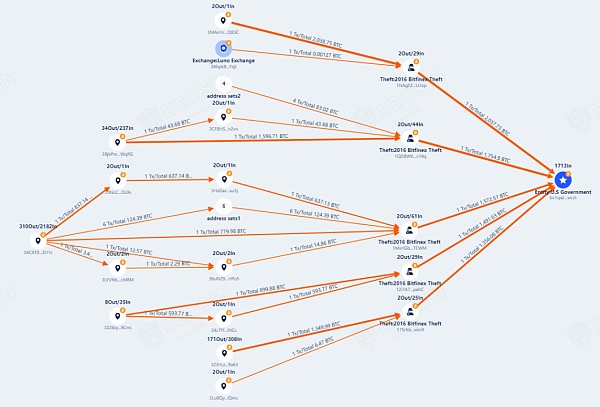
Lichtenstein and his wife in February 2022 Heather Morgan arrested;
Convicted of theft after pleading guilty in August 2023;
Meanwhile 'crypto-stealing couple' say they had access to Bitfinex's systems for months , stealing hundreds of millions of dollars. They used Bitcoin Fog to launder money as many as 10 times, though he noted that he later switched to other mixers.
"Coin-stealing couple" become federal witnesses in money laundering trial
In this testimony, the "crypto-coin stealing couple" stated that they used approx. He used Bitcoin Fog 10 times for money laundering, and then switched to Helix, a currency mixing service that he thought was better;
The use of currency mixing services only accounts for a small part of the overall money laundering activities, and most of them are used to transfer funds. Deposited into a cryptocurrency trading account registered with identity information purchased on the dark web;
Lichtenstein stated that he had never had direct communication with Sterling Goff, the operator of the money laundering platform Bitcoin Fog, and Don’t know him;
The U.S. Department of Justice (DOJ) accused Bitcoin Fog of laundering more than 1.2 million Bitcoins in 2021, worth about $335 million at the time of the transaction. The funds came primarily from darknet markets and were involved in a range of illegal activities, including drug trade, computer fraud and identity theft.
Facing up to 20 years in prison, Lichtenstein decided to cooperate with the US authorities and uncovered the truth of the case. To put it simply, the "coin-stealing couple" laundered money at Bitcoin Fog. It turned out that money laundering was really possible here. Unexpectedly, they could be a witness.
Bitfinex Mastermind Uncovers Cryptocurrency Theft and Money Laundering Network
As of February 27, 2024, the trial is still ongoing, The jury has yet to reach a verdict.
Similarly, the operations of cryptocurrency mixers such as Sinbad and Tornado Cash have also come under the scrutiny of regulators and faced sanctions. In October 2020, the Financial Crimes Enforcement Network (FinCEN) imposed sanctions and the operators behind Bitcoin mixers Helix and Coin Ninja were hit with a $60 million civil penalty for operating two unregistered money services businesses (MSBs).
Some methods and suggestions on anti-money laundering
In this incident, the Bitfinex attackers used a variety of methods to launder money, and the illegal funds passed through a large number of service providers. This makes it more difficult to track funds.
Solutions and Suggestions
1. Implement strict KYC and AML regulations
Virtual asset service providers should require users to Comprehensive identity verification and ensuring they comply with KYC and AML regulations. This includes collecting user identification information, address verification and other necessary information.
2. Monitor trading activities
Virtual asset service providers should implement real-time monitoring systems to detect and analyze suspicious trading activities. This includes monitoring information such as transaction amount, frequency, source and destination.
3. Establish a reporting mechanism
Virtual asset service providers should establish a reporting mechanismthrough the risk control system Report any suspicious transactions or activity. Virtual asset service providers should promptly address these reports and cooperate with regulators in their investigations.
4. Strengthen cooperation and communication
Virtual asset service providers should actively cooperate with security companies, regulatory agencies and law enforcement agencies to jointly Combating money laundering. It is foreseeable that criminals will continue to adjust and improve their money laundering strategies to adapt to changes in regulatory measures and AML tools. They may decentralize transactions, use covert transaction routes, or exploit technological vulnerabilities to hide illicit financial flows. Virtual asset service providers should regularly cooperate and communicate with security companies to identify and respond to these changes in a timely manner.
 Dante
Dante






