By: Lisa
Background
According to feedback from our partner imToken, a new type of cryptocurrency scam has emerged recently. This scam generally uses offline physical transactions as the main scenario, uses USDT as a payment method, and uses the modification of the Remote Procedure Call (RPC) of the Ethereum node to conduct fraudulent activities.
Malicious Process
The SlowMist Security Team analyzed this type of scam, and the specific malicious process of the scammers is as follows:
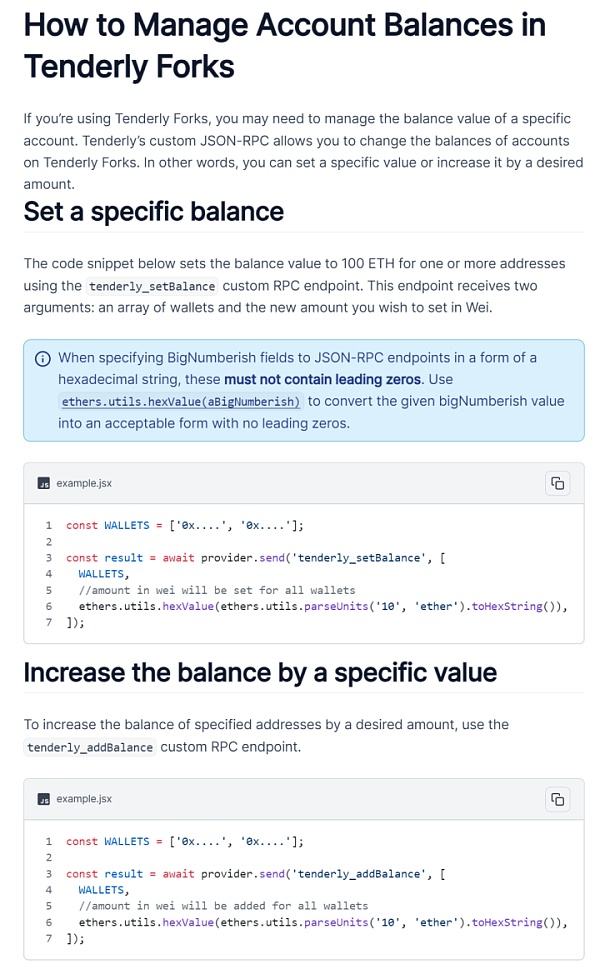
First, the scammers will induce the target users to download the genuine imToken wallet, and use 1 USDT and a small amount of ETH as bait to gain the trust of the users. Then, the scammer will guide the user to redirect their ETH RPC URL to the scammer's own node (https://rpc.tenderly.co/fork/34ce4192-e929-4e48-a02b-d96180f9f748).
This node has actually been modified by the scammer using Tenderly's Fork function, and the user's USDT balance has been falsified to make it look like the scammer has already deposited the money into the user's wallet. As a result, the user will mistakenly think that the balance has been credited. But when the user tries to transfer the mining fee to cash out the USDT in the account, he will realize that he has been fooled. At this time, the scammer has long disappeared.

In fact, in addition to the balance display being modified, Tenderly's Fork function can even change the contract information, posing a greater threat to users.
(https://docs.tenderly.co/forks)
Here we have to ask a question - what is RPC? In order to interact with the blockchain, we need a way to access the network server through the appropriate general options. RPC is a way to connect and interact, allowing us to access the network server and perform operations such as viewing balances, creating transactions, or interacting with smart contracts. By embedding RPC functions, users are able to execute requests and interact with the blockchain. For example, if a user uses a decentralized exchange by connecting a wallet (such as imToken), they are actually communicating with the blockchain server through RPC. Generally speaking, all types of wallets are connected to secure nodes by default, and users do not need to make any adjustments. However, if you easily trust others and link your wallet to an untrusted node, the balance and transaction information displayed in the wallet may be maliciously modified, resulting in financial loss.
MistTrack Analysis
We used the on-chain tracking tool MistTrack to analyze one of the known victim wallet addresses (0x9a7…Ce4), and we can see that the victim address received a small amount of 1 USDT and 0.002 ETH transferred from the address (0x4df…54b).

Checking the funds of the address (0x4df…54b), it was found that the address transferred 1 USDT to 3 addresses respectively. It seems that this address has been defrauded three times so far.

Tracing back further, the address is associated with multiple trading platforms and interacts with the address marked as "Pig Butchering Scammer" by MistTrack.

Summary
The cunning of this type of scam is that it exploits the psychological weaknesses of users. Users often only pay attention to whether there is money in their wallets, but ignore the possible risks behind it. Scammers take advantage of this trust and negligence to defraud users through a series of operations that make people believe in them, such as transferring small amounts of money. Therefore, the SlowMist Security Team recommends that users must remain vigilant when conducting transactions, improve their self-protection awareness, and do not trust others easily to avoid damage to their own property.
 Sanya
Sanya
 Sanya
Sanya JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Beincrypto
Beincrypto Bitcoinist
Bitcoinist Beincrypto
Beincrypto Beincrypto
Beincrypto Cointelegraph
Cointelegraph Cointelegraph
Cointelegraph