Once upon a time, the Greeks used giant wooden horses to build horses and dedicated them to the city of Troy. The people in the city thought it was a symbol of peace, not knowing that there was a threat lurking in it.
With the successful launch of Bitcoin ETF, more and more new users and funds are flocking to Web3 again. The warm-up of the market seems to indicate the future of Web3. The future of large-scale applications is one step closer. However, a lack of policy and security concerns remain major obstacles to the widespread adoption of cryptocurrencies.
In the encryption world, hackers can directly profit from millions or even hundreds of millions of dollars by attacking vulnerabilities on the chain. At the same time, the anonymity of cryptocurrency This creates conditions for hackers to escape unscathed. The total value locked (TVL) across all decentralized finance (DeFi) protocols will be around $4 billion by the end of 2023 (currently $10 billion)And in 2022 alone, the total number of tokens stolen from DeFi protocols The value reached US$310 million, accounting for 7% of the above value. This number fully illustrates the seriousness of security issues in the Web3 industry, hanging above our heads like the sword of Damocles.
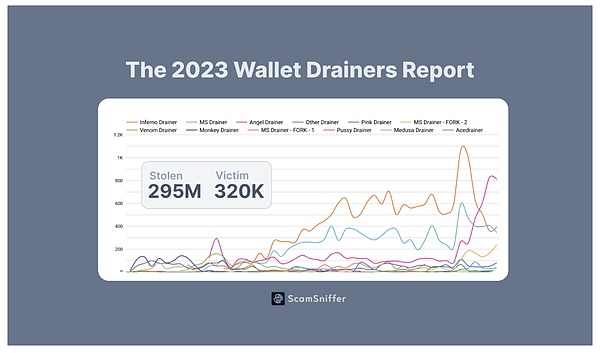
Not only the on-chain environment, but also the security issues of the Web3 client cannot be underestimated. Judging from the data disclosed by Scam Sniffer, in 2023, 324,000 users had their assets stolen due to phishing, and the total value of the stolen amount was as high as US$295 million. This is very serious in terms of both the scope of the impact and the amount of the amount. However, from the user's perspective, security incidents themselves are lagging - it is often difficult for users to fully realize the seriousness of potential risks before an incident actually occurs. As a result, people often fall into the“survivor error”, thereby neglecting the importance of safety.
This article starts from the security challenges faced by the current market and discusses the security risks brought about by the rapid growth of Web3 users. By analyzing security solutions proposed by companies such as Goplus, we further understand how to support the large-scale application of Web3 from aspects such as compliance and security. We believe that Web3 security is an underexplored 100-billion-dollar market, and as the Web3 user base continues to expand, the demand for client security services is showing an exponential growth trend.
Did you know the article earlier?
Hidden threats and the billion-dollar market
1.1 Asset security
1.2 Behavioral security
1.3 Protocol Security
Web3 Security Track Analysis< /p>
Next generation security products: escorting large-scale applications of Web3
Conclusion
The full text is 5,400 words and the estimated reading time is 12 minutes
Hidden threats and the billion-dollar market
Currently, Web3 security products are mainly in the form of ToB , ToC, ToD mainly. The B-side mainly conducts product security audits, conducts penetration tests on products and outputs audit reports, and mainly performs security protection on the product side. The C-side is mainly aimed at protecting the user's security environment. Based on the real-time capture and analysis of threat intelligence, it outputs detection services through APIs and performs security protection on the user side. ToD (Developer) is mainly aimed at developer tools, providing automated security audit tools and services for Web3 developers.
Security audit is a necessary static security measure. Almost every Web3 product will conduct a security audit and make the audit report public. Security audits not only enable the community to secondary verify the security of the protocol, but are also one of the foundations for users to build trust in the product.
However, security auditing is not a panacea. In view of the market development trends and current narrative, we foresee that the challenges of user security environment will continue to rise, mainly reflected in the following aspects:
Assets Security
The launch of each round of market must be accompanied by the issuance of new assets. With the popularity of ERC404 and the rise of FT and NFT hybrid tokens, the issuance of assets on the chain will continue to innovate and become more complex in the future. Challenges to the security of new types of assets are increasing day by day. As different asset types are mapped and integrated through smart contracts, the complexity of the system increases, and accordingly, its security faces greater challenges. This complexity provides attackers with a broader attack space. For example, by designing a specific callback mechanism or tax collection mechanism, attackers can interfere with asset transfers or even launch direct DoS attacks. This makes traditional Pre-Chain methods such as asset issuance contract security auditing and formal verification difficult. Solutions with real-time monitoring, warnings, and dynamic interception are urgently needed.
Behavioral Safety
Data provided by CSIA shows that 90 % of cyber attacks begin with phishing. The same applies to web3. Attackers target users' private keys or on-chain funds and send phishing links or fraudulent information through platforms such as Discord, , or install virus files and other behaviors.
On-chain interaction has high learning costs, which itself is anti-human. Even an offline signature can lead to millions of dollars in losses. When we click to sign and face various input parameters, do we really know what we are authorizing? On January 22, 2024, a cryptocurrency user suffered a phishing attack and signed a Permit signature with incorrect parameters. After obtaining the signature, the hacker used the wallet address authorized by the signature to withdraw $4.2 million worth of tokens from the user's account.
A weak user-side security environment can also lead to asset loss. For example, when a user imports a private key into an App wallet on Android, the private key often remains unoverwritten on the phone's clipboard after being copied. In this case, the private key will be read when the malware is opened, and the on-chain assets owned by the wallet will be automatically detected and transferred automatically, or the user's assets will be stolen after an incubation period.
As more and more new users enter Web3, the security issue of the user-side environment will become a huge hidden danger.
Protocol Security
Re-entrancy attacks are still part of the current protocol One of the biggest challenges facing security. Despite numerous risk control strategies, incidents involving this type of attack occur frequently. For example, in July last year, Curve suffered a severe reentrancy attack due to a compiler flaw in its contract programming language Vyper, resulting in losses of up to $60 million. This incident also caused the security of DeFi to be widely questioned.
Although there are many "white box" solutions for contract source code logic, hacking incidents like Curve reveal an important issue: even if the contract source code is To be sure, compiler problems may also cause the final running results to be different from the expected design. "Converting" a contract from source code to actual runtime is a challenging process, each step may bring unexpected problems, and the source code itself may not fully cover all potential scenarios. Therefore, it is far from enough to rely solely on security at the source code and compilation level; even if the source code seems flawless, vulnerabilities may still appear quietly due to compiler problems.
Therefore, runtime protection will become necessary. Unlike existing risk control measures that focus on the protocol source code level and take effect before running, runtime protection involves protocol developers writing runtime protection rules and operations to handle unanticipated situations at runtime. This facilitates real-time assessment and response to runtime execution results.
According to predictions by crypto asset management company Bitwise, total cryptocurrency assets will reach $16 trillion in 2030. If we analyze quantitatively from the perspective of Security Cost Risk Assessment, the occurrence of on-chain security incidents brings almost 100% asset loss, so the Exposure Factor (EF) can be set to 1, so a single loss The Single Loss Expectancy (SLE) is $16 trillion. When the Annualized Rate of Occurrence (ARO) is 1%, we can get the Annualized Loss Expectancy (ALE) to be $160 billion, which is the maximum value of the security investment cost of cryptocurrency assets.
Based on the seriousness, frequency and rapid growth of the market size of cryptocurrency security stories, we can foresee that Web3 security will be a market worth hundreds of billions of dollars. It has grown rapidly with the growth of Web3 market and user scale. Furthermore, considering the huge growth in the number of individual users and the increasing concern for asset security,we can foresee that the demand for Web3 security services and products in the C-side market will grow exponentially, which is a problem that needs to be deeply explored. blue ocean market.
Web3 Security Track Analysis
As Web3 security issues continue to arise, there is a significant increase in demand for advanced tools that can protect digital assets, verify the authenticity of NFTs, monitor decentralized applications, and ensure compliance with anti-money laundering regulations. According to statistics, the current security threats faced by Web3 mainly come from:
Protocol-oriented hackers Attacks
User-oriented fraud, phishing, and private key theft
Security attacks on the chain itself
In order to deal with these risks, the current market The company mainly launches corresponding services and tools focusing on ToB testing and auditing (Pre-Chain) and ToC monitoring (On-Chain). Compared to ToC, players on the ToB track were introduced earlier, and new players continue to enter. However, as the Web3 market environment becomes more complex, ToB auditing becomes increasingly difficult to deal with various security threats. The importance of ToC monitoring has also become highlighted, and its demand has therefore continued to grow.
In the current market, companies represented by Certik and Beosin provide ToB testing and auditing services. Most of the services provided by such companies are at the smart contract level, performing security audits and formal verification of smart contracts. Through this kind of pre-chain method, through wallet visual analysis, smart contract vulnerability security analysis, source code security audit, etc., smart contracts can be detected to a certain extent and risks can be reduced.

ToC is monitored on the chain ( On-Chain) process execution is completed through risk analysis, transaction simulation and status monitoring of smart contract code, on-chain status, and user transaction meta-information. Compared with ToB, Web3 C-side security companies are generally founded later, but their growth rate is very impressive. The services provided by Web3 security companies represented by GoPlus are gradually being applied to various Web3 ecosystems.
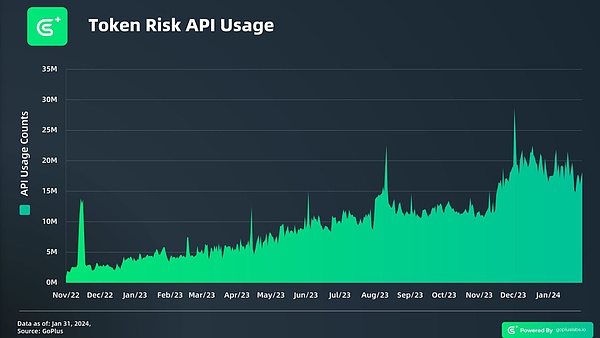
Since GoPlus was founded in May 2021, the number of daily calls to the application API it launched has increased rapidly, from the initial few hundred queries per day to 20 million calls per day at the peak of the market. The figure below shows the change in call volume of the Token Risk API from 2022 to 2024. Its growth rate shows the growth of GoPlus' importance in the Web3 field.
The user data module it launched has gradually become an important part of various Web3 applications. It is used in top-level applications such as CoinMarketCap (CMC), CoinGecko, Dexscreener, and Dextools. It plays a key role in market websites, leading decentralized exchanges such as Sushiswap and Kyber Network, and wallets such as Metamask Snap, Bitget Wallet, and Safepal.
In addition, this module is also used by user security service companies such as Blowfish, Webacy, and Kekkai. This demonstrates the important role of the GoPlus User Security Data Module in defining the security infrastructure of the Web3 ecosystem and demonstrates its important place in contemporary decentralized platforms.
GoPlus mainly provides the following API services. Through targeted data analysis of multiple key modules, it provides comprehensive insights into user security data to prevent evolving security threats and respond to the multi-faceted challenges of Web3 security.
Token Risk API: used to assess the risks associated with different cryptocurrencies
NFT Risk API: Risk summary for evaluating various NFTs
Malicious Address API: Used to identify and flag addresses related to fraud, phishing, and other malicious activities
dApp Security API: Provides real-time monitoring and threat detection for decentralized applications
Approval Contract API : Used to manage and review smart contract calling permissions
In the C-side track, we also noticed Harpie. Harpie focuses on protecting Ethereum wallets from theft, and has cooperated with companies such as OpenSea and Coinbase to protect thousands of users from fraud, hacker attacks, private key theft and other security threats. The products launched by the company start from the two aspects of "monitoring" and "recovery", by monitoring the wallet to find vulnerabilities or threats, and immediately notify and help users to repair the vulnerabilities after discovering them; in a timely manner after the user becomes a victim of a hacker attack or fraud Respond to save assets. It can prevent attacks and respond to security emergencies, and has achieved great results in Ethereum wallet security.
In addition, ScamSniffer provides its services as a browser plug-in. The product can perform real-time detection through a malicious website detection engine and multiple blacklist data sources before users open the link, protecting users from malicious websites. When users conduct online transactions, it provides detection of fraud methods such as phishing to protect the security of user assets.
Next generation security products: escorting large-scale applications of Web3
In response to the issues mentioned above such as asset security, behavioral security, protocol security, and the need for on-chain compliance, we conducted an in-depth study of the solutions of GoPlus and Artela to understand how they maintain user security environments. and on-chain operating environment to support large-scale applications of Web3.
User security environment Infra
Blockchain transaction security is the cornerstone of Web3's large-scale application security. On-chain hacking attacks, phishing attacks, and Rug Pulls occur frequently, and the security of on-chain transaction traceability, on-chain suspicious behavior identification, and user profiling capabilities is crucial. Based on this, GoPlus launched the first full-scenario personal security detection platform SecWareX.
SecWareX is a Web3 personal security product built based on the SecWare user security protocol. It provides complete and real-time identification of runtime attacks on the chain, taking the lead in A one-stop, comprehensive security solution for alerts, timely interception, and subsequent disputes, and supports asset issuance contracts to customize security interception strategies for specific scenarios.
For user behavioral security education, SecWareX cleverly combines learning security knowledge with token incentives by launching the Learn2Earn program , allowing users to gain actual rewards while enhancing their security awareness.
Financial compliance solutions
Anti-Money Laundering (AML) is one of the most pressing needs on public blockchains today. On the public chain, by analyzing factors such as the source, expected behavior, amount, and frequency of transactions, suspicious or abnormal behaviors can be identified in a timely manner, which helps decentralized exchanges, wallets, and regulatory agencies detect potential money laundering, fraud, gambling, etc. Illegal activities, and promptly take measures such as warnings, freezing assets, or reporting to law enforcement agencies to strengthen DeFi's compliance and large-scale application.
With the continuous enrichment of on-chain behaviors, Know Your Transaction for decentralized applications will become indispensable for large-scale applications Necessary conditions. GoPlus’ malicious address API is critical for exchanges, wallets and financial services operating in Web3 to comply with regulatory requirements and safeguard their operations, highlighting the inherent link between regulatory compliance and technological advancement in the Web3 space and emphasizing The importance of continuous monitoring and adaptation to safeguard the integrity of the ecosystem and the safety of its users.
On-chain security protocol
Artela is the first public chain Layer 1 to natively support runtime protection. Through EVM++ design, Artela's dynamically integrated native extension module Aspect supports adding extension logic at various points in the transaction life cycle and recording the execution status of each function call.
When a threatening reentrant call occurs during the execution of the callback function, Aspect will detect and immediately retract the transaction to prevent Attackers exploit reentrancy vulnerabilities. Taking the re-entrancy attack protection of the Curve contract as an example, Artela provides chain-native level protocol security solutions for various DeFi applications.
As protocol complexity and the diversity of underlying compilers increase, the "black box" solution to on-chain runtime protection Compared with the "white box" solution that only statically checks the contract code logic, the importance of this solution has become increasingly prominent.
Conclusion
On January 10, 2024, the SEC officially announced its approval of the listing and trading of spot Bitcoin ETFs, representing the most important step in achieving mainstream adoption of the crypto asset class. As the policy environment matures and security protection measures continue to be strengthened, we will eventually see the arrival of large-scale applications of Web3. If the large-scale application of Web3 is like turbulent waves, then Web3 security is a solid dam built for user assets to resist external waves and ensure that everyone can ride out every wave smoothly.
Reference:
Scam Sniffer Reports Cryptocurrency Phishing Scams Will Steal $300 Million in 2023 https://drops.scamsniffer.io/zh/post/scam-sniffer - Annual Report $300 Million from 320,000 Users Assets were damaged due to malicious attacks this year/
Mike: erc404 security risk https://x.com/mikelee205/status/1760512619411357797?s =46&t=0AOF3L1pmOanZxpmmZpkwg
How We Go Mainstream: The State of Web3 Security | Patrick Collins at SmartCon 2023 https:// www.youtube.com/watch?v=EYF6lUoWAgk&t=1489s
2023 Web3 Security Landscape Report. https://salusec .io/blog/web3-security-landscape-report
Defillama https://defillama.com/
< /li>Quantitative information security assessment method. https://www.sohu.com/a/561657716_99962556
- < p style="text-align: left;">Eliminate Reentrancy Attacks with On-chain Runtime Protection. https://artela.network/blog/eliminate-reentrancy-attacks-with-on-chain-runtime-protection
Signature phishing. https://support.metamask.io/hc/en-us/articles/18370182015899-Signature-phishing
How dangerous is Permit signature fishing? $4.2 million stolen from crypto giant. https://www.coinlive.com/news/how-dangerous -is-permit-signature-fishing-4-2-million-stolen-from
CISA report https://www. cisa.gov/stopransomware/general-information
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Brian
Brian Clement
Clement Coinlive
Coinlive 


 Cointelegraph
Cointelegraph