Foreword
SlowMist Technology releases "2023 Blockchain Security and Anti-Money Laundering Annual Report", we hope that this report will provide readers with useful information, help practitioners and users more comprehensively understand the current status and solutions of blockchain security, and contribute to promoting the security of the blockchain ecosystem.
Due to space limitations, only the key contents of the analysis report are listed here. The complete content can be downloaded from the PDF at the end of the article.

1. Overview< /strong>
2023 will be an exciting and turbulent year for the blockchain industry. Against this background, this report will review key regulatory compliance policies and developments in the blockchain industry in 2023, summarize blockchain security incidents and anti-money laundering trends in 2023, conduct statistics on some money laundering tools, and analyze typical security incidents and typical Conduct a detailed analysis of phishing scam techniques and propose prevention plans and measures. In addition, we also invited Web3 anti-fraud platform Scam Sniffer to write about the phishing group Wallet Drainers, and we analyzed and analyzed the money laundering methods and profit-making funds of the hacker group Lazarus Group.
2. Blockchain security situation
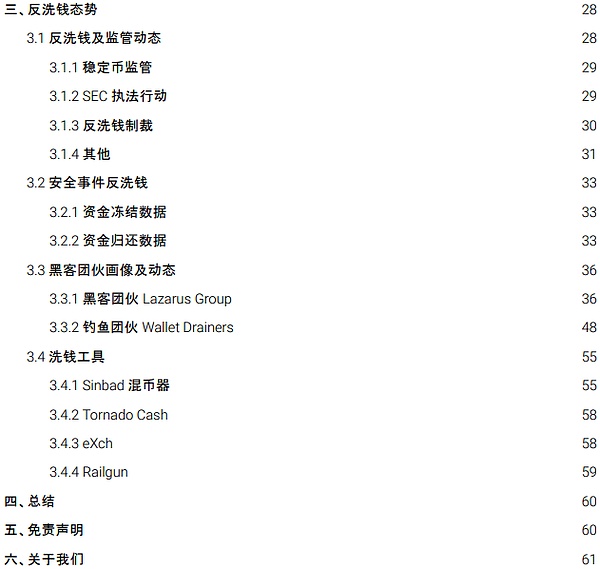
According to the slow According to statistics from SlowMist Hacked, there were a total of 464 security incidents in 2023, with losses as high as US$2.486 billion. Compared to 2022 (a total of 303 cases, losses of approximately US$3.777 billion), losses decreased by 34.2% year-on-year.
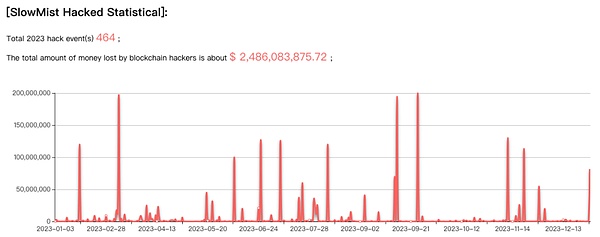
From the project track, DeFi is still the most frequently attacked area. There were 282 DeFi security incidents in 2023, accounting for 60.77% of the total incidents, with losses as high as US$773 million. Compared with 2022 (a total of 183 incidents, losses of approximately US$2.075 billion), losses dropped by 62.73% year-on-year.
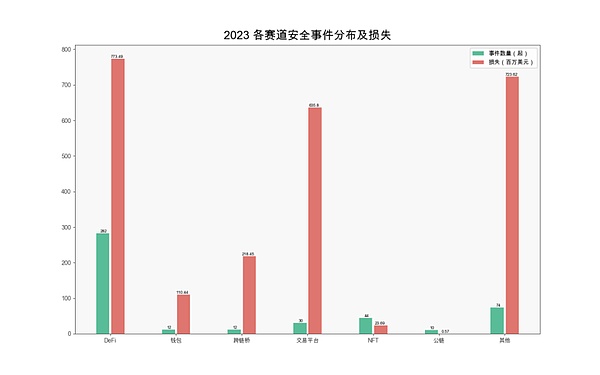
(Distribution and losses of safety incidents at each track in 2023)
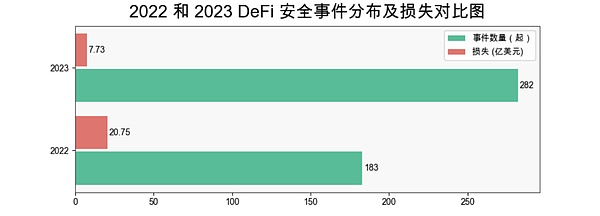
(2022 and 2023 DeFi security incident distribution and loss comparison chart)
From an ecological perspective, Ethereum has the highest loss, reaching US$487 million. Next is Polygon at $123 million.
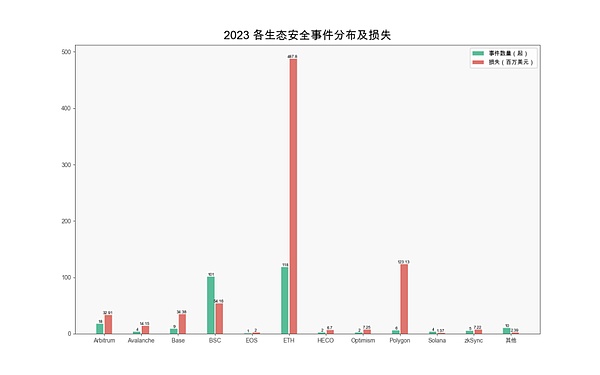
(Distribution and losses of various ecological security incidents in 2023)
From In terms of the causes of incidents, runaway incidents were the most common, with 117 incidents, resulting in losses of approximately US$83 million. Secondly, there are security incidents caused by account hacking.
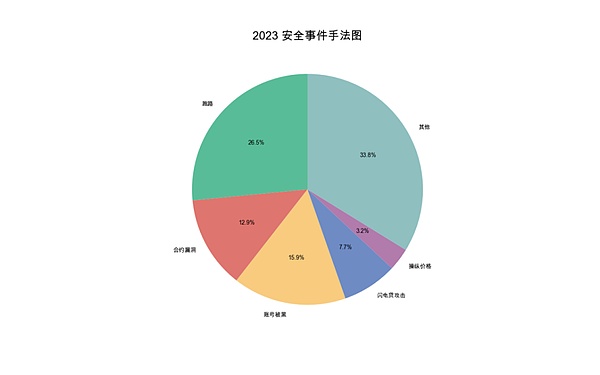
(2023 Security Incident Methods Map)
This section selects the year 2023 Loss of the Top 10 security incidents. See the PDF file at the end of the article for details.
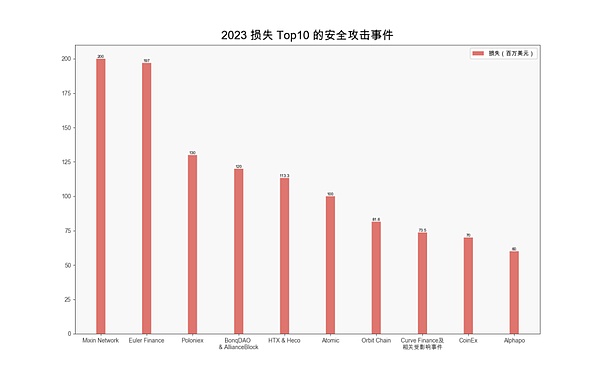
(Security attacks that lost Top 10 in 2023)
According to the slow fog block According to statistics from the Chain Hacked Event Archive (SlowMistHacked), there were as many as 117 Rug Pull incidents in 2023, resulting in losses of approximately US$83 million. Among them, Base’s ecological losses were the highest, reaching US$32.5 million. Followed by BSC Ecology, reaching US$23.05 million.
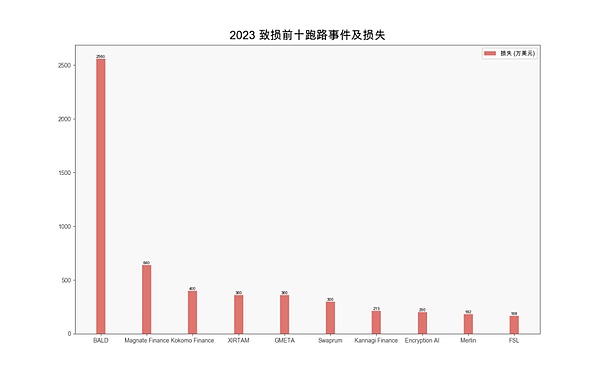
(2023 top ten runaway events and losses)
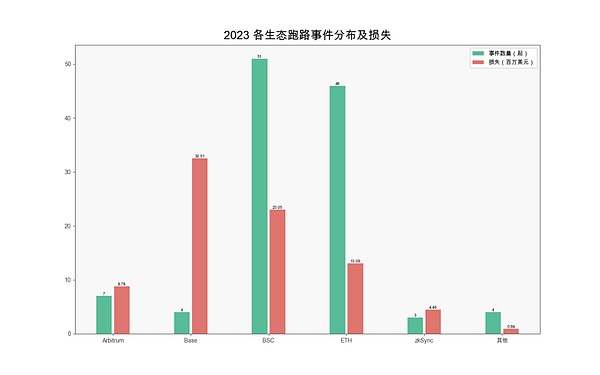
(2023 Distribution and losses of various ecological runaway events)
Rug Pull is a scam, usually the project party takes the initiative to commit evil, and it happens in a variety of ways: For example, the project party initiates initial liquidity, pushes up the price and then withdraws the liquidity; for example, the project party first creates an encryption project, attracts investment from encryption users through marketing means, and then takes away the funds invested by users without warning at the right time and sells them. Crypto assets eventually disappeared; for example, a website was launched and closed after attracting hundreds of thousands of deposits; for example, the project party left backdoor code in the project. Regardless, any type of Rug Pull will cause investors to lose money.
At the same time, this section introduces an extremely covert Rug Pull case caused by contract storage: when the project token does not have any additional issuance records, malicious users The funds in the pool were siphoned away using large amounts of additional tokens that were not recorded.
Fraud
In recent years, the cryptocurrency market has become a fertile ground for scammers to commit fraud. Scammers often use fake accounts to impersonate celebrities, make friends to kill pigs, promote fake trading platforms, Ponzi schemes, etc., and even with the development of technology, scammers will also use artificial intelligence software to make the scam more convincing. This section will introduce a cryptocurrency scam that mainly occurred in Hong Kong - the JPEX incident. According to relevant reports, the JPEX thunderstorm may become the largest financial fraud case in Hong Kong history.
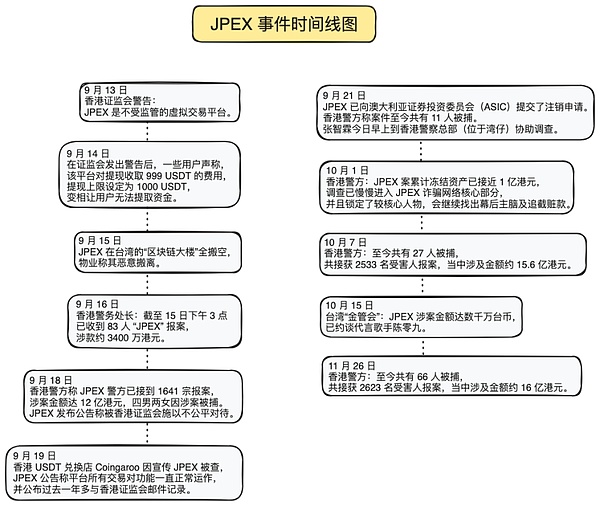
(JPEX event timeline chart)
This section selects our Some phishing/scam techniques disclosed in 2023:
1. WalletConnect phishing risk
2 , Permit signature phishing
3. Fake Skype App phishing
4. Disguised as a transfer address Phishing URL
5. Telegram fixed-point fraud attack
6. Create2 phishing risk (https://drops.scamsniffer.io/post/wallet-drainers-starts-using-create2-bypass-wallet-security-alert)
7. SIM card swap attack
3. Anti-money laundering situation
This section is divided into four parts: anti-money laundering and regulatory trends, security incident anti-money laundering, hacker group portraits and dynamics, and money laundering tools.
In 2023, the world of cryptocurrency continues to experience turmoil. During the last crypto bull run, every move by two industry giants, SBF and CZ, seemed to have a profound impact on the market. In November, however, a federal jury convicted SBF on charges of fraud and conspiracy stemming from FTX's collapse. Just weeks later, Binance accepted the charges, paid a $4.3 billion fine, and CZ agreed to relinquish control of Binance. As the cryptocurrency industry has experienced ups and downs between the turbulent "cold winter" and the bear market, governments and international organizations have also shown a more cautious attitude towards this, and regulatory policies for cryptocurrency in various countries are still gradually taking shape. Specific policies and enforcement actions can be found in the PDF at the end of this article.
1. Fund freezing data
With the strong support of InMist intelligence network partners , in 2023 SlowMist assisted customers, partners and public hacking incidents to freeze funds totaling more than 12.5 million US dollars.
2. Fund return data
It can still be fully or partially recovered after being attacked in 2023 There were 31 incidents of loss of funds. Across the 31 incidents, approximately $384 million was stolen, of which $297 million was returned, accounting for 77% of the stolen funds. Of the 31 incidents, 10 protocols had their funds returned in full.
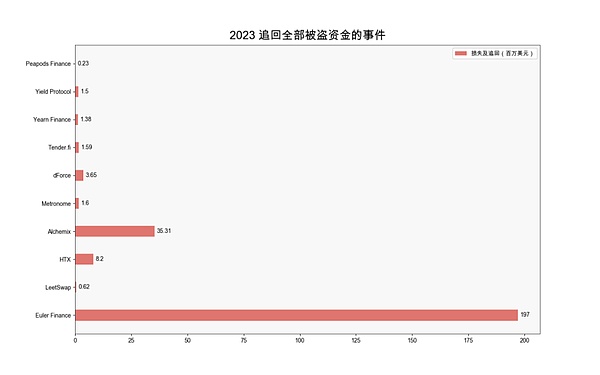
(2023 incident of recovery of all stolen funds)
1. Hacker Group Lazarus Group
According to public information in 2023, as of June, there are still no major cryptocurrency thefts attributed to the North Korean hacker Lazarus Group . Judging from on-chain activities, North Korean hackers Lazarus Group are mainly laundering cryptocurrency funds stolen in 2022, including approximately US$100 million in funds lost in the Harmony cross-chain bridge attack on June 23, 2022. In addition to laundering the cryptocurrency funds stolen in 2022, the North Korean hacker Lazarus Group is not idle at other times. This hacker group is dormant in the dark and secretly conducts APT-related attacks. These activities directly led to the cryptocurrency industry’s “Dark 101,” which began on June 3.
During the "Dark 101 Days", a total of 5 platforms were stolen, with the amount stolen exceeding US$300 million. Most of the stolen objects were centralized services. platform.
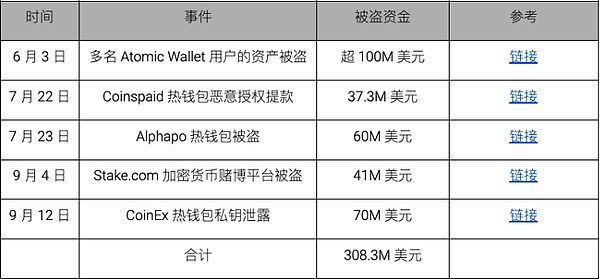
According to our analysis, the money laundering methods of North Korean hackers Lazarus Group have also continued to evolve over time. New money laundering methods will appear every once in a while. The timetable for changes in money laundering methods can be found in the PDF at the end of the article.
2. Fishing gang Wallet Drainers
Note: This section is written by Scam Sniffer. Thank you for this.
Wallet Drainer has achieved significant "success" as a cryptocurrency-related malware over the past year. The software was deployed on phishing websites to trick users into signing malicious transactions and then steal assets from their cryptocurrency wallets. These phishing campaigns continue to attack ordinary users in many forms, resulting in many people suffering significant property losses after unknowingly signing malicious transactions. In the past year, Scam Sniffer has monitored these Wallet Drainers to steal nearly $295 million from approximately 320,000 victims.
It is worth mentioning that nearly 7 million US dollars was stolen on March 11. Mostly due to the fluctuation of the USDC exchange rate, I encountered a phishing website pretending to be Circle. There has also been a large number of hacks approaching the Arbitrum Discord hack on March 24th and subsequent airdrops.
Each wave peak is accompanied by related mass events. It might be an airdrop, or it might be a hacking incident.
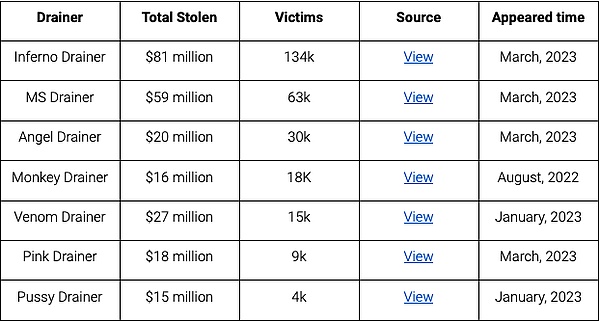
Following ZachXBT's revelations about Monkey Drainer, they announced their exit after being active for 6 months, and then Venom took over most of their clients. Then MS, Inferno, Angel, and Pink also appeared around March. As Venom ceased service around April, most of the phishing gangs turned to other services. At a 20% Drainer fee, they made at least $47 million from selling their services.
Money laundering tools
1. Sinbad Coin Mixer
2. Tornado Cash
3. eXch
4. Railgun
IV. Summary
This report summarizes the key regulatory compliance policies and developments in the blockchain industry in 2023, including but not limited to Global regulatory attitudes toward cryptocurrencies and a series of key policy changes. At the same time, we also summarized the blockchain security incidents and anti-money laundering trends in 2023, analyzed some money laundering tools, explained those typical security incidents and phishing scams, and proposed corresponding prevention and response measures. We hope that this report can provide readers with valuable information and help them gain a more comprehensive understanding of the security and anti-money laundering status of the blockchain industry, so that every industry participant can benefit from it and contribute to promoting the security of the blockchain ecosystem. Contribute to development.
5. Disclaimer
The content of this report is based on our Understanding of the blockchain industry, data support from SlowMist Hacked, the SlowMist blockchain hacked archive, and MistTrack, the anti-money laundering tracking system. However, due to the "anonymous" nature of the blockchain, we cannot guarantee the absolute accuracy of all data, nor are we responsible for errors, omissions, or losses caused by the use of this report. At the same time, this report does not constitute the basis for any investment advice or other analysis. If there are any omissions or shortcomings in this report, you are welcome to criticize and correct us.
The introduction reads here, the complete version, welcome to read and share:)
https:/ /www.slowmist.com/report/2023-Blockchain-Security-and-AML-Annual-Report(CN).pdf
 Edmund
Edmund



















