Overview
In November 2024, the total loss of Web3 security incidents was about 86.24 million US dollars. Among them, according to the SlowMist Blockchain Hacked Archives (https://hacked.slowmist.io), there were 21 hacking incidents, resulting in a loss of about 76.86 million US dollars, and 25.5 million US dollars were returned. The causes of the incidents involved contract loopholes, account hacking, and price manipulation. In addition, according to the Web3 anti-fraud platform Scam Sniffer, there were 9,208 victims of phishing incidents this month, with a loss of 9.38 million US dollars.
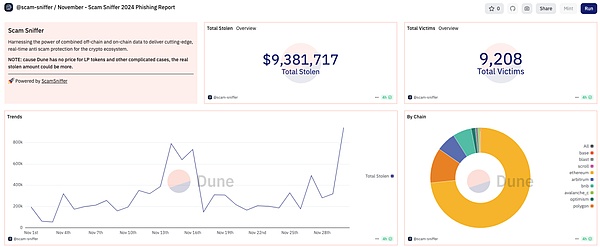
(https://dune.com/scam-sniffer/november-scam-sniffer-2024-phishing-report)
Major Security Events
MetaWin
On November 4, 2024, according to the chain detective ZachXBT monitoring, the encrypted gambling platform MetaWin was suspected of being attacked. More than $4 million was stolen from Ethereum and Solana chains. According to MetaWin CEO Skel, the attacker hacked into MetaWin's hot wallet through the platform's frictionless withdrawal system.
DeltaPrime
On November 11, 2024, the DeFi protocol DeltaPrime was attacked on Avalanche and Arbitrum, and DeltaPrime initially estimated the loss to be $4.75 million. The root cause of the attack was the lack of input verification in the reward collection function.
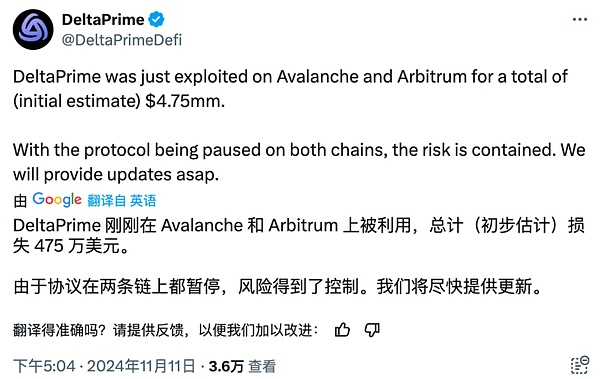
(https://x.com/DeltaPrimeDefi/status/1855899502944903195)
Thala
On November 15, 2024, the Aptos-based DeFi project Thala was attacked, resulting in the theft of $25.5 million. The attacker exploited a vulnerability in its smart contract. The project party suspended the relevant smart contracts and froze some tokens, and finally successfully froze about $11.5 million in assets. After working with law enforcement and multiple blockchain security teams, the project party successfully negotiated the recovery of the assets and allowed the attacker to keep $300,000 as a bounty.
(https://x.com/thalalabs/status/1857703541089120541?s=46&t=bcMyidYO0QkS5ajIW9CBdg)
DEXX
On November 16, 2024, funds of multiple users of the on-chain trading terminal DEXX were stolen. According to the statistics of the SlowMist Security Team, the scale of the loss of this incident has reached 21 million US dollars. At present, the SlowMist Security Team is assisting DEXX officials and partners to continue the analysis. On November 28, the SlowMist security team announced the 8,612 DEXX attacker addresses collected on the Solana chain. The attacker addresses on the EVM chain will also be made public after the cleaning statistics are completed.
(https://x.com/MistTrack_io/status/1862134946090881368)
Polter Finance
On November 17, 2024, the Fantom-based DeFi project Polter Finance was attacked and lost about $12 million. The attacker exhausted BOO's token reserves through flash loans and artificially raised the computing price of BOO. This enabled it to lend tokens far in excess of the actual value of the collateral, resulting in huge profits. The platform’s founders said they had filed a report with the Singapore authorities and tried to contact the attackers via on-chain messaging to negotiate the return of the funds, but have yet to receive a response.
(https://x.com/polterfinance/status/1857971122043551898)
Characteristic Analysis and Security Recommendations
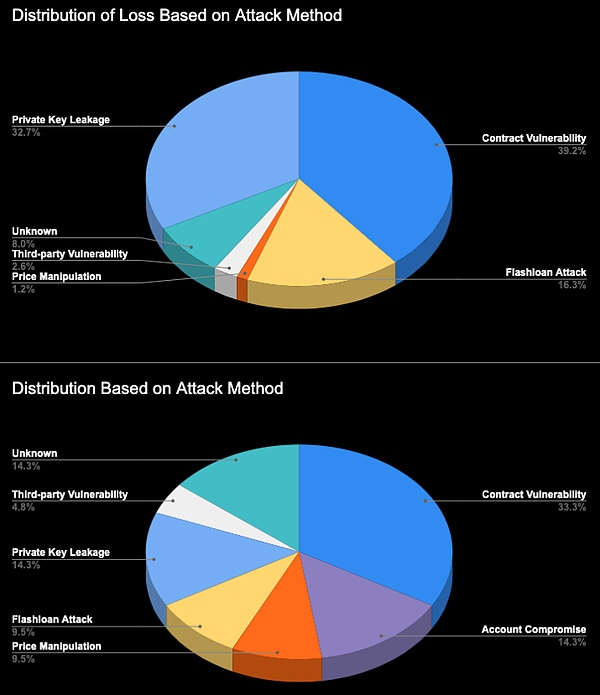
The number of security incidents and the scale of losses this month have decreased significantly compared with last month. This change to a certain extent reflects the industry's continuous improvement of security protection measures. It is worth noting that contract vulnerabilities account for the highest proportion of both the distribution of attack causes and the scale of losses caused. The 7 contract vulnerability exploitation incidents that occurred this month caused a loss of approximately US$30 million, accounting for 39% of the total losses. The SlowMist Security Team recommends that project owners always remain vigilant and conduct comprehensive security audits regularly to track and resolve new security threats and vulnerabilities to protect project and asset security.
In addition, the SlowMist Security Team noted that a real attack case of AI poisoning against the Crypto industry occurred this month. This phenomenon shows that the target range of supply chain attacks is further expanding. While pursuing efficiency, some developers may rely too much on AI-generated code and ignore the review of code security. Therefore, the SlowMist Security Team reminds developers and project owners not to blindly trust the output results when using AI to generate code. All codes should undergo strict security audits and tests before being put into actual use to prevent security risks and protect the asset security of projects and users. At the same time, project owners should also strengthen the overall security management of the supply chain, conduct a comprehensive assessment of third-party tools and services, and continue to pay attention to security trends in related fields to respond to new threats in a timely manner.
 ZeZheng
ZeZheng
 ZeZheng
ZeZheng Catherine
Catherine Coinlive
Coinlive  Others
Others Tristan
Tristan Coinlive
Coinlive  Beincrypto
Beincrypto Cointelegraph
Cointelegraph Nulltx
Nulltx Cointelegraph
Cointelegraph