Author: Byte Jun; Compiler: Byte CKB
In the blockchain industry, " The term "Isomorphic binding" first appeared in "RGB++ Protocol Light Paper" written by Cipher, co-founder of Nervos CKB. Isomorphic binding is one of the core technologies used by the Bitcoin layer asset issuance protocol RGB++. Through this technology, RGB++ can solve various problems encountered by the RGB protocol and give RGB more possibilities.
However, what many people don’t know is that isomorphic binding technology is not limited to enabling RGB protocols. In fact, it can also be used Other one-layer asset issuance protocols that use UTXO characteristics (such as Runes, Atomic, Taproot Assets, etc.) bring Turing-complete contract extensions and performance extensions to these assets without cross-chains or loss of security.
In today’s article, we will introduce the technology and development of isomorphic binding to you in detail through easy-to-understand language. prospect.
What is isomorphic binding?
The premise of using isomorphic binding technology is isomorphism. EVM blockchains such as Ethereum use an account model, which is another accounting method. The difference between the UTXO model and the account model is similar to the difference between using banknotes and using bank transfers in real life. Therefore, if the EVM blockchain wants to empower a layer of asset issuance protocol that uses UTXO characteristics, it will be difficult to use isomorphic binding technology, and the traditional cross-chain bridge solution must be chosen. Asset transfer and performance expansion are achieved through locking/minting, destroying/minting, or locking/unlocking.
The Cell model of the CKB blockchain is an improved version based on the Bitcoin UTXO model. It has the same origin as the UTXO model. Therefore, we can bind or map UTXOs on one blockchain to UTXOs on another blockchain one by one through isomorphic binding technology. Take the RGB++ protocol as an example. Since RGB assets are essentially parasitic on Bitcoin UTXO, the RGB++ protocol can use isomorphic binding technology to map Bitcoin UTXO to the Cell of the CKB blockchain one by one, so that we can use CKB Blockchain to replace client-side verification of RGB.
In order to better understand the isomorphic binding technology, we use Land and Land Deed as analogous objects :
1. If we compare the Bitcoin main network to land, Zhang San issued an asset through the RGB++ protocol. This asset ispaper Land deedcorresponds to 100 acres of land. The paper land deed is stored on the Bitcoin blockchain (that is, in UTXO, and Zhang San owns this UTXO). The isomorphic binding technology is equivalent to issuing a correspondingfor this paper land title on the CKB blockchain. >Electronic version of the title deed(stored in Cell, Zhang San owns this Cell).
2. Zhang San transferred 40 acres of land to his relative Li Si, so the original 100 acres of paper land deeds were destroyed and a new paper land deed was generated. , one of the paper land deeds is 40 acres, and the other is 60 acres, and they are still stored on the Bitcoin blockchain. The difference is that the 40 acres of land deeds are stored in the UTXO controlled by Li Si, and the 60 acres of land deeds are stored in the UTXO controlled by Li Si. In the UTXO controlled by Zhang San. It should be noted that the role of the Bitcoin blockchain here is to prevent Zhang San from using the 100-acre paper land deed multiple times (that is, double-spending), rather than to verify whether the newly generated land deed adds up to exactly the right area. Equal to 100 acres. In other words, under the original RGB agreement, Li Si had to verify whether the land deed obtained by Li Si said 40 acres, and Li Si himself had to verify the land traceability certificate provided by Zhang San ( The original RGB protocol requires client verification, and client verification needs to be done by the user himself).
3. The Bitcoin light client deployed on the CKB blockchain is responsible for the " Destroy the paper land deed of 100 acres and generate a paper land deed of 40 acres and a paper land deed of 60 acres" to verify this matter and verify whether it really happened.
4. After passing the verification, the electronic land deed of 100 acres on the CKB blockchain is destroyed, and an electronic land title of 40 acres is generated and stored in Lisi In the Cell controlled by Zhang San, an electronic version of the land deed of 60 acres is stored in the Cell controlled by Zhang San. It should be noted that since the CKB blockchain is Turing complete, it can verify and ensure that the total land area of the two newly generated electronic land deeds is exactly 100 acres, and Li Si can also see it at a glance My land deed says 40 acres (because the data on the CKB blockchain is publicly visible). Therefore, the RGB++ protocol can replace the client verification of the RGB protocol, that is, the verification in step 2 (including land traceability verification) is omitted.
The above four steps correspond to the four operating processes of isomorphic binding technology: Mapping UTXO into Cell, verifying transactions, and cross-chain verification , perform status changes on CKB.
If you want to understand these 4 processes more deeply, it is recommended to read the article "Isomorphic Binding: The Heartbeat of Cross-Chain Synchronization in RGB++》:
https://mirror.xyz/zhixian.eth/2xAcBzO28RueHTaNFMU2MTaM1jFT0MoV0ZtXb7madxk
Security Analysis
In order to more easily understand the security of isomorphic binding, we still take the RGB++ protocol as an example.
In the above analogy between land and land deeds, we can clearly see that the paper land deeds stored in Bitcoin UTXO are secure and prevent double-spending. , mainly relies on the security of the Bitcoin blockchain, and Bitcoin is by far the longest and most secure PoW chain.
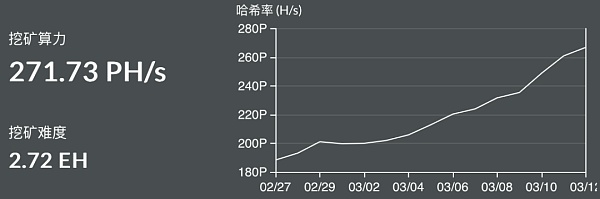
The security of the electronic title deed generated through isomorphic binding technology and the prevention of double spending mainly rely on the security of the CKB blockchain. CKB has adopted the same time-tested PoW consensus mechanism as Bitcoin from the beginning to maximize security and decentralization. Currently, the mining machines used by CKB are produced by Bitmain, the world’s largest AISC mining machine manufacturer. CKB’s current network computing power is approximately 271 PH/s, which has reached a record high. It is extremely difficult to forge or reconstruct a PoW chain because the computing power of each block needs to be recalculated, so we can trust the security of the CKB blockchain.
Of course, you can also choose not to trust it. Then all you need to do is the second step in the above example. Verify for yourself whether the land deed says 40 acres and whether the land traceability certificate provided by Zhang San is true and valid. This is also the approach of the RGB protocol. Users need to complete the client verification by themselves; theRGB++ protocol just provides one more choice. In addition to choosing to complete the client verification by themselves, you can also choose to trust the CKB area. For the verification of the blockchain, the CKB blockchain is only used here as the DA layer and status announcement. The security of paper title transactions does not even have anything to do with CKB.
The RGB++ protocol not only allows the CKB blockchain to act as the DA layer, it also supports Jump operations, allowing assets on the Bitcoin blockchain to Go to the CKB blockchain (and vice versa) at any time. Because the CKB blockchain is Turing complete, DeFi applications such as lending and DEX can be built on it, so the assets jumped can participate in various financial activities such as mortgage lending, staking for interest, and transactions.
Taking assets from Jump to participate in various activities on the CKB chain, its security depends on the security of the CKB blockchain, and in the above we Introducing the CKB blockchain, which is actually very secure. If you still don’t trust the security of the CKB blockchain, after you get the assets on the CKB chain, you can directly jump back to the Bitcoin blockchain and become assets on the Bitcoin blockchain.
The risk of the Jump function lies in block reorganization, which can be avoided by waiting for a few more block confirmations. On the Bitcoin chain, a transaction is considered irreversible after 6 blocks are confirmed. The number of PoW confirmations and security are not linearly related. The difficulty of overturning a PoW block increases exponentially as the block advances. Therefore, on the CKB blockchain, it is necessary to achieve the same confirmation level of 6 blocks in Bitcoin. For security, it only takes about 24 block confirmations, while CKB’s average block generation time is about 10 seconds. The 24 block confirmation time is actually much shorter than Bitcoin’s 6 block confirmation time.
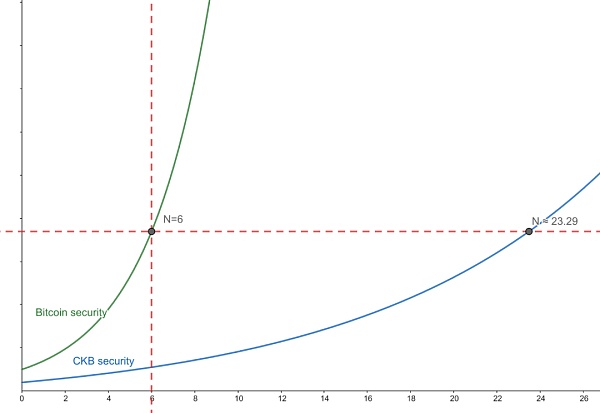
Schematic diagram of PoW security (non-theoretical calculation)
Therefore, if you want to get better security, choose to wait for a few more block confirmations ; If you want to take into account the user experience, make some trade-offs and product optimization. For more discussions on the security of RGB++, it is recommended to read "RGB++ In-depth Discussion (1): Security Analysis":
https://talk. nervos.org/t/rgb-1/7798
The development prospects of isomorphic binding technology
As mentioned at the beginning of the article, isomorphic binding The specific technology is not limited to enabling the RGB protocol. In fact, it can also be used in other layer-one asset issuance protocols that use UTXO characteristics. The picture below illustrates the use of isomorphic binding technology well:

From the picture we can see that using isomorphic binding technology, we can issue a layer of Bitcoin assets Assets issued by protocols such as Runes, Atomical, Taproot Assets, etc. are all bound or mapped to CKB's Cell, bringing Turing-complete contract expansion and performance expansion to these assets without cross-chain or loss of security.
In addition to the assets issued by Bitcoin, we can also use isomorphic binding technology to integrate other pan-UTXO model blockchains (such as Dogechain, Ergo , BCH, BSV, LTC, etc.) are mapped to the Cell of CKB. This is a very imaginative blueprint. With the addition of the Jump operation, the CKB blockchain becomes a marketplace for all crypto assets parasitic on UTXO. “All roads lead to CKB.”

Summary
Isomorphic binding technology originates from the RGB++ protocol. RGB++ maps Bitcoin UTXO to the Cell of Nervos CKB through isomorphic binding, thus solving the technical problems of the original RGB protocol in actual implementation and providing More possibilities. But isomorphic binding technology is not limited to empowering the RGB protocol, nor is it limited to the Bitcoin layer. In fact, it can be used in any layer-of asset issuance protocol of the pan-UTXO blockchain that uses UTXO characteristics, and uses Jump Technology brings Turing-complete contract expansion and performance expansion to these assets without the need for cross-chains or loss of security.
UTXO is the prerequisite for the use of isomorphic binding technology, and PoW provides sufficient security for isomorphic binding. As a UTXO+PoW chain, CKB will make isomorphic binding technology shine. In the near future, we may see a scenario where “all roads lead to CKB”.
 JinseFinance
JinseFinance
 JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance JinseFinance
JinseFinance Coindesk
Coindesk Cointelegraph
Cointelegraph 链向资讯
链向资讯 链向资讯
链向资讯